Given the current rate of technological progress, Microsoft Azure is rightfully considered the innovation leader. It has released Azure Bastion, a managed PaaS solution that allows users to securely access Azure Virtual Machines (VMs) via the Azure Portal without the need for a client.
Azure Bastion is a fully managed platform-as-a-service (PaaS) that allows users to connect to Azure virtual machines (VMs) securely using Remote Desktop Protocol (RDP) or Secure Shell (SSH) directly through the Azure portal, without requiring a public IP address or a virtual private network (VPN). Do you want to find out more about this service? Buckle up, because we’re about to take a deep dive into the universe of Azure Bastion today!
What is Azure Bastion?
Azure Bastion is a service that allows you to connect to a virtual machine using your browser and the Azure portal. The Azure Bastion service is a fully platform-managed PaaS service that you can deploy within your virtual network. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. Once you connect, your virtual machines do not require a public IP address, agent, or special client software.
Many of the VMs on the virtual network in which Bastion is provisioned have secure RDP and SSH connectivity. Bastion prevents the virtual machines’ RDP/SSH ports from exposing to the outside world while also allowing secure access using RDP/SSH.
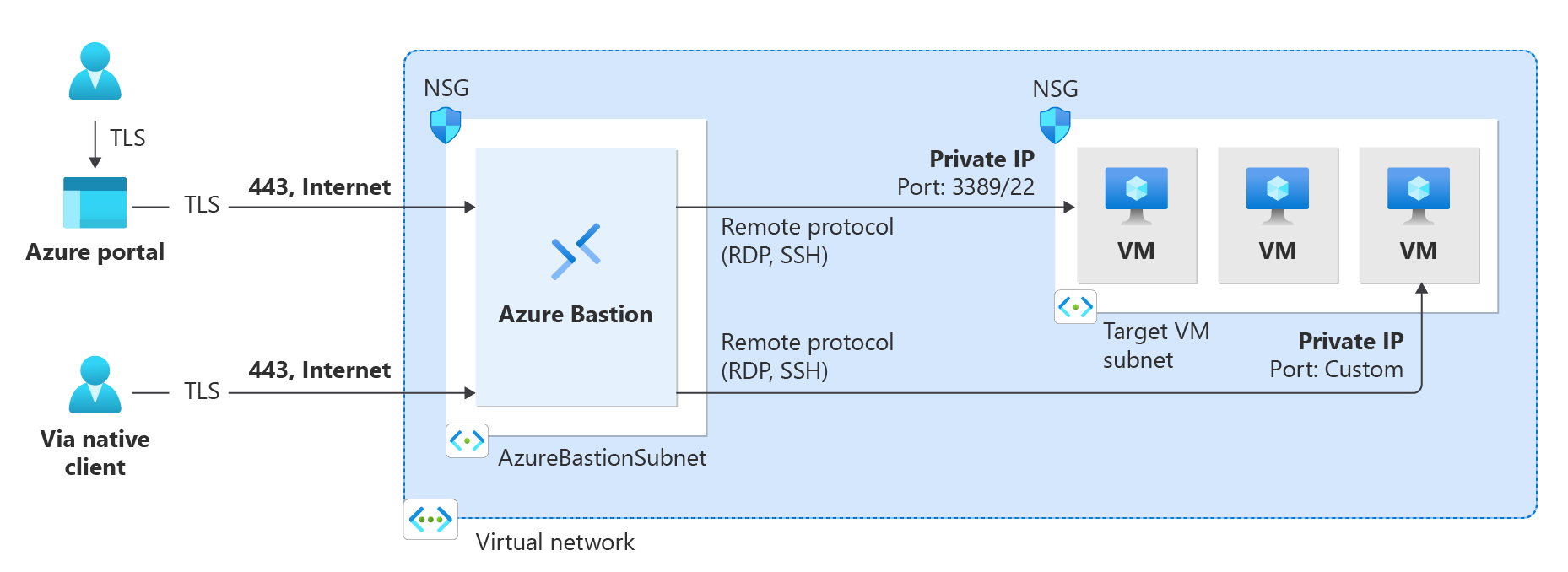
Azure Bastion Architecture:
The most straightforward approach to describe Azure Bastion is as a controlled jump host. A jump host, sometimes known as a jump box, is a virtual computer that connects to a virtual network, is assigned a public IP address, and is protected from network traffic entrance and egress using strict network traffic ingress and egress policies. The idea is that you connect to the jump host and then utilize the jump host to manage the network’s production VMs.
Azure Bastion is installed as a virtual network rather than a subscription, account, or virtual machine. Once you establish a Bastion service in your virtual network, the RDP/SSH experience is available to all of your VMs in the same virtual network. RDP and SSH are two of the most common methods for connecting to Azure workloads.
It’s not a good idea to expose RDP/SSH ports to the Internet because they’re regarded a large threat surface. Protocol weaknesses are commonly blamed for this. To control this danger surface, you should deploy bastion hosts on the public side of your perimeter network. Bastion host servers are built to survive attacks and are configured to do so. RDP and SSH connection to workloads behind the bastion, as well as farther inside the network, is provided via bastion servers.
The figure below helps in understanding the Azure Bastion Architecture.
- Firstly, the Bastion host is deployed in a virtual network that includes the AzureBastionSubnet subnet, which has a minimum prefix of /27.
- Secondly, Any HTML5 browser can connect to the Azure portal.
- Thirdly, the virtual computer to which the user connects is chosen by the user.
- Then, RDP/SSH session opens in the browser with a single key.
- Lastly, On the Azure VM, No public IP is required.
Features:
Azure Bastion provides several features that enable users to connect to their Azure virtual machines (VMs) securely and efficiently:
- Secure connectivity: Azure Bastion enables users to connect to their VMs securely using Remote Desktop Protocol (RDP) or Secure Shell (SSH) directly through the Azure portal, without requiring a public IP address or a virtual private network (VPN). This helps to ensure that connections are secure and private.
- Web-based access: This provides web-based access to VMs, which means that users do not need to install any client software or plugins. This makes it easy for users to connect to their VMs from any device with a web browser, including smartphones and tablets.
- Remote session management: Azure Bastion enables users to manage their remote sessions, including disconnecting or logging off from their sessions. This helps to ensure that VMs are not left open or accessible to unauthorized users.
- Customizable settings: Azure Bastion provides several customizable settings, including idle timeout settings, audio settings, and clipboard redirection settings. This enables users to customize their experience based on their specific requirements.
- Role-based access control: Azure Bastion supports role-based access control (RBAC), which means that users can be granted specific permissions based on their role in the organization. This helps to ensure that only authorized users have access to VMs and that access is granted based on the principle of least privilege.
- Diagnostic logs: Azure Bastion provides diagnostic logs that enable users to troubleshoot issues, including network connectivity issues and authentication issues. This helps to ensure that issues can be resolved quickly and efficiently.
Why Use Azure Bastion?
Azure Bastion enables secure remote access to Azure virtual machines (VMs) through Transport Layer Security from the Azure interface (TLS). The following are some of the benefits of using Azure Bastion:
1. Limit public exposure of virtual machine IPs
A single hardened access point provides access to all virtual machines in a virtual network. Exposing the bastion host as the primary exposed public access helps lockdown of public Internet exposure and reduces threats like port scanning and other forms of malware that threaten the VMs.
2. Using Azure Bastion to connect to your Azure VMs securely
Using a bastion host will help protect your VMs from threats like port scanning and other forms of malware. Azure Bastion provides stable and smooth RDP and SSH access to your virtual. You can now safely access your VMs from the Azure portal using SSL to avoid exposing public IP addresses.
3. Fully managed bastion service
Azure Bastion uses a PaaS provider that is completely managed, autoscaling, and hardened to provide reliable RDP and SSH connectivity. Network Security Groups (ACLs) across the subnets are seamlessly integrated and set up once, eliminating the need for ongoing maintenance. To protect the virtual machines, Bastion offers an integrated platform alternative to manually deploying and managing jump servers. You can deploy Azure Bastion in a matter of minutes and start using it right away
4. RDP and SSH to Azure Virtual Machines over SSL
You can connect to your virtual machines in your virtual network over SSL, port 443, directly from Azure Portal with Azure Bastion. This allows clientless RDP/SSH connectivity, allowing you to connect from anywhere like any device or platform, without the need for a additional agent running inside your virtual machines
5. Enhanced security
Azure Bastion provides a secure way to connect to your VMs using RDP or SSH directly through the Azure portal, without requiring a public IP address or a virtual private network (VPN). This helps to ensure that connections are secure and private, and that VMs are not exposed to the internet.
6. Easy access
Azure Bastion provides web-based access to VMs, which means that you can connect to your VMs from any device with a web browser, including smartphones and tablets. This makes it easy to access your VMs from anywhere, without requiring any additional software or plugins.
7. Reduced management overhead
This eliminates the need to manage remote desktop gateways or VPN connections, which can reduce the management overhead and simplify the overall experience of connecting to your VMs.
8. Customizable settings
This provides several customizable settings, including idle timeout settings, audio settings, and clipboard redirection settings. This enables you to customize your experience based on your specific requirements.
Prerequisites for Connecting to a VM securely
Using Azure portal and Azure Bastion you can connect to a virtual machine (VM) through your browser. But before learning how to create and connect a bastion host, lets have a look at the prerequisites:
- Firstly, you need an Azure account with an active subscription. To be able to connect to a VM through your browser using Bastion, you must be able to sign in to the Azure portal.
- Then, a Windows virtual machine in a virtual network.
- Moreover, if you already have a virtual network, make sure to select it on the Networking tab when you create your VM.
- Also, if you don’t have a virtual network, you can create one at the same time you create your VM.
- Further, you do not need to have a public IP address for this VM in order to connect via Azure Bastion.
- Additionally, Required VM roles include reader role on the virtual machine and reader role on the NIC with private IP of the virtual machine.
- Lastly, the Required VM ports is Inbound ports: RDP (3389)
Let’s concentrate on learning how to create and configure an Azure Bastion host
Creating a Bastion Host
A bastion host can configure in a few different ways. You’ll build a bastion host in the Azure portal directly from your VM in the steps that follow. Various settings corresponding to your virtual machine and/or virtual network will automatically populate when you create a host from a VM.
- To begin with, Sign in to the Azure portal.
- Then, Navigate to the VM that you want to connect to, then select Connect.
- Next, from the dropdown, select Bastion.
- On the TestVM | Connect page, select Use Bastion.
- Moreover, n the Connect using Azure Bastion page, configure the values.
- Further, Click Create Subnet to create the AzureBastionSubnet.
- After the subnet creates, the page advances automatically to Step 3. For Step 3, use the following values:
- Firstly, Name: Name the bastion host.
- Then, Public IP address: Select Create new.
- Further, Public IP address name: The name of the Public IP address resource.
- Also, Public IP address SKU: Pre-configured as Standard
- Next, Assignment: Pre-configured to Static. You can’t use a Dynamic assignment for Azure Bastion.
- Then, Resource group: The same resource group as the VM.
- Lastly, after completing the values, select Create Azure Bastion using defaults. Azure validates your settings, then creates the host. The host and its resources take about 5 minutes to create and deploy.
Now, that your Azure Bastion has been deployed to the virtual network, you move on to the connect page.
Connecting Azure Bastion to Azure VMs
On the VM overview page, select Connect > Bastion > Use Bastion. Then follow these steps:
- Firstly, Type the username and password for your virtual machine.
- Next, Select Connect
- The RDP connection to this virtual machine will open directly in the Azure portal (over HTML5) using port 443 and the Bastion service.
With, this you have successfully and securely connected to a VM by using Azure Bastion!
Pricing:
Looking at the Azure Bastion functionality and features, are you thinking about its pricing? Here is the answer to your question
Bastion features a straightforward pricing scheme. You are charged for the time the Bastion hast is in use. Like all Microsoft VM Services, as well as any Bastion services you’ve deployed. You can rapidly calculate the expenses for the Bastions Hosts using the Azure Price Calculator. Furthermore, Microsoft provides Azure customers with a variety of buying options:
- Firstly, Purchase Azure directly from Microsoft: If you build an account through the Azure website or through a Microsoft representative, you’ll get the same Azure pricing.
- Secondly, Use Azure as part of a managed service from a Microsoft partner: Microsoft Cloud Solution Provider (CSP) partners offer a variety of complete managed cloud solutions for Azure.
Final Words
To summarise, Azure Bastion is a fully managed PaaS service that provides secure and seamless RDP and SSH access to your virtual machines directly through the Azure Portal. Moreover, Azure Bastion is provisioned directly in your Virtual Network (VNet) and supports all VMs in your Virtual Network (VNet) using SSL without any exposure through public IP addresses.
Furthermore, it connects your RDP and SSH sessions in the Azure Portal with only a single click. Additionally, when signing into your Azure virtual machines, use your SSH keys for authentication. Although Azure Bastion offers a number of benefits, it is not available in all areas. Despite this, it helps you stream user session information to your storage account. You can also view existing remote sessions and force-disconnect users from those sessions. Take Azure Certification to further enhance your skills and career. Test your knowledge about Azure Bastion with the Microsoft Azure Architect Technologies (AZ-303) exam Now!


