With the advancement in the cloud technology sector, it has become has concern for securing the network and IP address. Related to this, Google cloud has introduced Cloud NAT (network address translation). This enables resources without external IP addresses to create outbound connections to the internet.
But, how this is useful in connectivity? To find an answer to this, we will cover all the areas of Cloud NAT to get better clarity of how this service operates and provides benefits.
What is Google Cloud NAT?
Cloud NAT refers to a GCP-manageable high-performance Network Address Translation. This allows you to deploy your application instances without public IP addresses while simultaneously allowing them to access the internet in a controlled and efficient manner for updates, patching, config management, and other tasks.
Google Cloud NAT (Network Address Translation) enables instances within a virtual private cloud (VPC) network to access the internet but not be directly accessible from the internet.
With Cloud NAT, instances in a VPC network can communicate with the internet using a pre-configured external IP address. This IP address links with the Cloud NAT gateway, which performs the NAT operation, translating the private IP addresses of the instances in the VPC to the external IP address.
Cloud NAT is useful in scenarios where instances within a VPC network need to access the internet for software updates, to download packages, or to send and receive data, but it is not necessary to expose them directly to the internet.
Further, outgoing connectivity is also provided by Cloud NAT for the following resources:
- Firstly, instances of Compute Engine virtual machines (VMs) without external IP addresses.
- Secondly, Private Google Kubernetes Engine (GKE) clusters.
- Thirdly, accessing Cloud Run instances via Serverless VPC Access.
- Then, using Serverless VPC Access, you can access Cloud Functions instances.
- Lastly, accessing App Engine standard environment instances via Serverless VPC Access.
Benefits of Cloud NAT:
Google Cloud NAT provides several benefits, including:
- Increased security: Cloud NAT provides an extra layer of security by isolating instances within a VPC network from direct internet access. This helps reduce the attack surface of the instances and reduces the risk of exposure to potential threats.
- Improved compliance: By using Cloud NAT, organizations can ensure that their instances comply with industry regulations and standards that require strict control over internet access.
- Simplified network management: With Cloud NAT, administrators can manage network access for instances within a VPC network from a central location, reducing the complexity of managing firewall rules and security groups.
- Increased scalability: Cloud NAT allows organizations to scale their network infrastructure more easily, as they can add or remove instances from the VPC network without having to reconfigure firewall rules and security groups.
- Improved performance: Cloud NAT uses Google’s high-performance network infrastructure, which provides fast and reliable internet access for instances within a VPC network.
- Cost savings: Cloud NAT provides a cost-effective solution for organizations that need to provide internet access to instances within a VPC network. It eliminates the need for expensive VPN solutions and reduces the costs associated with managing firewall rules and security groups.
Google Cloud NAT Architecture
Cloud NAT is a software-defined, distributed managed service. It isn’t based on proxy virtual machines or appliances. That is to say, it configures the Andromeda software that runs your VPC network for enabling source network address translation (source NAT or SNAT) for VMs that don’t have external IP addresses. Moreover, for established inbound response packets, Cloud NAT additionally supports destination network address translation (DNAT).

Further, outbound NAT also deploys in your VPC network using Cloud NAT in conjunction with static routes, with the default internet gateway as the next hop. A default route in your VPC network fits this criterion in a basic configuration. And, Cloud NAT does not support improper inbound connections from the internet Only packets that arrive as a response to outbound packets is subject to DNAT.
What are the features of Google Cloud NAT?
The top-most features of Google Cloud NAT are:
- Automated Configuration: Cloud NAT is easy to set up and configure, with the option to automatically configure firewall rules and route tables for internet-bound traffic.
- Scalable Infrastructure: Cloud NAT uses the high-performance network infrastructure provided by Google Cloud Platform, which can scale to meet the demands of large organizations.
- Increased Security: Cloud NAT provides an extra layer of security by isolating instances within a VPC network from direct internet access, reducing the attack surface of the instances.
- Improved Compliance: Cloud NAT helps organizations comply with industry regulations and standards that require strict control over internet access.
- Centralized Management: Cloud NAT provides a centralized method for managing network access for instances within a VPC network, reducing the complexity of managing firewall rules and security groups.
- Cost Savings: Cloud NAT provides a cost-effective solution for organizations that need to provide internet access to instances within a VPC network, eliminating the need for expensive VPN solutions.
- High Availability: Cloud NAT provides high availability for internet-bound traffic, ensuring that instances within a VPC network have reliable and fast access to the internet.
Configuring Google Cloud NAT
Cloud NAT can be created to deliver internet NAT for packets sent from the following sources:
- The primary internal IP address of the Compute Engine VM’s network interface, assuming the network interface does not have an external IP address assigned to it. Because the network interface matches the Google Cloud internet access requirements, if the network interface has an external IP address allocated to it, Google Cloud executes one-to-one NAT for packets whose sources match the interface’s principal internal IP address. However, without Cloud NAT, the existence of an external IP address on an interface comes before precedence and one-to-one NAT executes.
- The network interface of the VM has an alias IP range. Even if the network interface has an external IP address, you can use a Cloud NAT gateway to provide NAT for packets that originate from the interface’s alias IP range. Further, for alias IP addresses, an external IP address on an interface never performs one-to-one NAT. However, in some cases, Cloud NAT for GKE clusters can offer service even if the cluster has external IP addresses.
1. Routes and firewall rules
- Cloud NAT is based on customized static routes with the default internet gateway as the next hop. In order to effectively utilize a Cloud NAT gateway, your VPC network must have a default route with the default internet gateway as the next hop. Moreover, there are no Google Cloud firewall rules necessary for Cloud NAT. That is to say, firewall rules can implement directly to Compute Engine VM network interfaces, not through Cloud NAT gateways.
- Further, no specific firewall rules are required to allow connections to or from NAT IP addresses. Before NAT, applicable egress firewall rules for that network interface are evaluated as packets for that network interface by a Cloud NAT gateway. After packets have been handled by NAT, ingress firewall rules are assessed.
2. Subnet IP address range applicability
As long as a Compute Engine VM’s network interface does not have an external IP address allocated to it, a Cloud NAT gateway can provide NAT services for packets transmitted from that network interface. In some cases, Cloud NAT can offer service to GKE clusters even if the cluster nodes have external IP addresses. Further, a Cloud NAT gateway can be set up to offer NAT for the following:
- Firstly, all subnets in the region have primary and secondary IP address ranges. The principal internal IP addresses and any alias IP ranges of eligible VMs whose network interfaces use a subnet in the area are NATted by a single Cloud NAT gateway. Per region, this option uses only one NAT gateway.
- Secondly, all subnets in the region’s primary IP address ranges. That is, the primary internal IP addresses and alias IP ranges from subnet primary IP address ranges of qualifying VMs whose network interfaces utilize a subnet in the area are NATed by a single Cloud NAT gateway. However, you can add more Cloud NAT gateways to the area to offer NAT for alias IP ranges derived from eligible VMs’ subnet secondary IP address ranges.
- Lastly, IP address ranges for custom subnets. Subject to Cloud NAT quotas and limits, you can create as many Cloud NAT gateways as you need. Further, you decide which subnet primary and secondary IP address range each gateway should serve.
3. Applicable RFCs
Cloud NAT has the support for both Endpoint-Independent Mapping and Endpoint-Dependent Filtering, as defined by RFC 5128. However, the Endpoint-Independent Mapping can be enabled or disabled. And, when you construct a NAT gateway, Endpoint-Independent Mapping is deactivated by default.
1. Endpoint-Independent Mapping
- This means that if a VM delivers packets to numerous destinations from the same internal IP address and port pair, the gateway maps all of those packets to the same NAT IP address and port pair, independent of the packets’ destination.
2. Endpoint-Dependent Filtering
- This means that internet response packets are only allowed if they originate from an IP address and port to which a VM has already sent packets. Regardless of the Endpoint Mapping type, the filtering is based on the endpoint. However, this feature is always remains on.
4. NAT traversal
Cloud NAT is compatible with typical NAT traversal protocols such as STUN and TURN if Endpoint-Independent Mapping is enabled, and if you deploy your own STUN or TURN servers:
- After creating a communication channel, STUN (Session Traversal Utilities for NAT, RFC 5389) permits direct communication between VMs behind NAT.
- TURN (Traversal Using Relays around NAT, RFC 5766) allows VMs behind NAT to communicate with one another via a third server with an external IP address. Further, each VM connects to the server’s external IP address, which acts as a relay between the two VMs. The TURN protocol is more resilient, but it uses more bandwidth and resources.
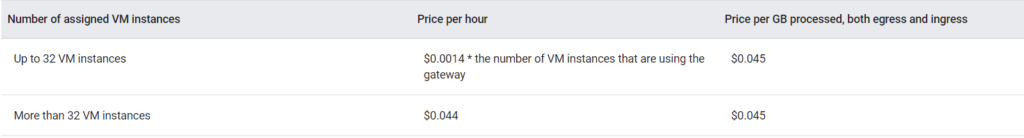
Cloud NAT pricing
The following usage is used to determine cloud NAT pricing:
- Firstly, the cost of the NAT gateway is calculated hourly based on the number of VM instances that use it. However, the number of VM instances available per hour is limited to 32. And, gateways that serve more than the given number of instances get charge at the highest per-hour rate.
- Secondly, the cost per GB of entry and egress data processed by the gateway. And, the cost of data processing is the same in all regions.
Final Words
Abobe we have gone through the overview of the Google Cloud NAT service by learning about its benefits, specifications, and pricing. Google Cloud NAT (Network Address Translation) is a service provided by Google Cloud Platform that enables instances within a private Google Cloud Virtual Private Cloud (VPC) network to access the internet or other Google services without being directly exposed to the public internet. It provides a layer of network security by allowing instances to communicate with external resources using a shared public IP address that is managed by Google.
Google Cloud NAT offers several benefits, including simplified networking, improved security, and reduced costs. By using Cloud NAT, organizations can simplify their networking setup and reduce the need for complex firewall rules. It also helps to improve security by isolating instances from the public internet and reducing the attack surface of their infrastructure. Finally, Cloud NAT can help to reduce costs by eliminating the need to assign public IP addresses to every instance within a private network.
Overall, Google Cloud NAT is a valuable service for organizations looking to secure their infrastructure and simplify their networking setup while also reducing costs. It is an important tool for organizations that want to use the public internet for connectivity without exposing their resources to the internet.
So, read the blog, gather some information, and if you believe this service meets your needs, start with Google docs as a reference guide.