Subnets play a crucial role in AWS networking, allowing you to segment your network and control access to resources. Public subnets are typically used to host resources that are accessible from the public internet, such as web servers or load balancers, while private subnets are used to host resources that should not be accessible from the internet, such as database servers or internal applications. In addition to their connectivity characteristics, public and private subnets also differ in their routing, security, and availability features. Public subnets are usually associated with an internet gateway, which allows them to communicate with the internet and can be accessed from anywhere in the world. On the other hand, private subnets can only be accessed from within the VPC (Virtual Private Cloud) or through a VPN (Virtual Private Network) connection, providing an additional layer of security.
In this blog post, we will dive deeper into the technical details of public and private subnets, including their routing tables, security groups, and network ACLs (Access Control Lists). We will also discuss how to configure and deploy public and private subnets in your AWS environment using best practices, such as deploying resources across multiple Availability Zones to ensure high availability and fault tolerance.
By the end of this blog post, you will have a clear understanding of the differences between public and private subnets in AWS, their respective benefits and drawbacks, and how to deploy them effectively in your AWS environment. Whether you are building a new application or migrating an existing one to the cloud, understanding the fundamentals of AWS networking is essential for building a secure and scalable infrastructure.
Difference between Public and Private Subnet in AWS
In AWS, a subnet is a logical subdivision of an IP network that can be used to partition and organize resources within a virtual private cloud (VPC). There are two types of subnets in AWS: public subnets and private subnets. Let’s take a closer look at the differences between these two types of subnets.
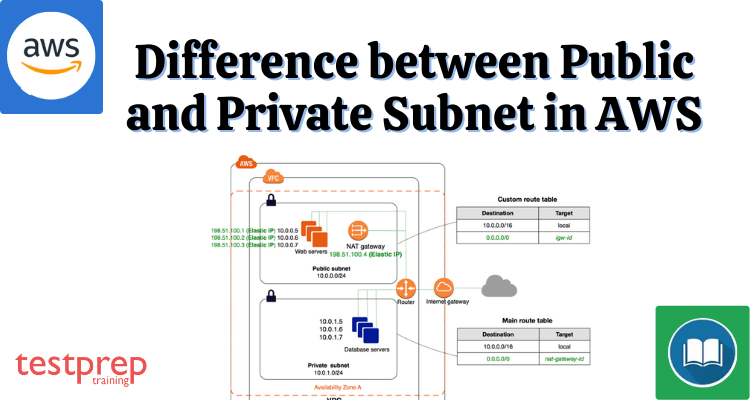
- Public Subnet: A public subnet is a subnet that has a route to the Internet Gateway. Resources in a public subnet can be accessed from the internet and can also access the internet directly. This is typically used for resources that need to be publicly accessible, such as web servers, load balancers, and other publicly accessible services.
- Private Subnet: A private subnet, on the other hand, is a subnet that does not have a route to the Internet Gateway. Resources in a private subnet can access the internet, but only via a NAT Gateway or a bastion host in a public subnet. This is typically used for resources that do not need to be publicly accessible, such as databases, application servers, and other internal services.
Here are some key differences between Public and Private Subnets in AWS:
- Public subnets have a direct route to the internet, whereas private subnets do not.
- Resources in a public subnet can be accessed from the internet, whereas resources in a private subnet cannot be accessed directly from the internet.
- Public subnets are typically used for resources that need to be publicly accessible, while private subnets are used for resources that do not need to be publicly accessible.
- Public subnets are often associated with load balancers, web servers, and other publicly facing resources, while private subnets are often associated with databases, application servers, and other internal resources.
Overall, the key difference between public and private subnets in AWS is the level of access that they provide to the internet. Public subnets have direct access to the internet, while private subnets require a NAT Gateway or a bastion host to access the internet.
Types of Subnets
Subnets can be public, private, or VPN-only, depending on how you configure your VPC:
Public subnet: IPv4 or IPv6 traffic on the subnet is routed to an internet gateway or an egress-only internet gateway and can access the public internet. See Connect to the internet using an internet gateway for more information.
Private subnet: IPv4 or IPv6 traffic on the subnet is not routed to an internet gateway or egress-only internet gateway and thus cannot access the public internet.
VPN-only subnet: This subnet has no route to the internet gateway, but its traffic is routed to a virtual private gateway for a Site-to-Site VPN connection. More information can be found in the AWS Site-to-Site VPN User Guide.
Components of VPC
A virtual private cloud (VPC) is a virtual isolated network that is exclusive to your AWS account.
Subnet — An IP address range in your VPC.
Route table — A set of rules known as routes that determine where network traffic is directed.
Internet gateway — A gateway that you connect to your VPC to allow communication between your VPC’s resources and the internet.
VPC endpoint — This allows you to connect your VPC privately to supported AWS services and VPC endpoint services. Instances in your VPC do not need public IP addresses to communicate with service resources.
A public subnet is a subnet that is linked to a routing table and has a route to an Internet gateway. This links the VPC to the Internet as well as other AWS services.
A private subnet is one that is associated with a routing table but does not have a route to an internet gateway. Backend servers are instances in the private subnet that do not accept traffic from the internet.
Why Use a Public Subnet – The public subnet’s resources can send outbound traffic directly to the Internet and vice versa. Users from the internet, for example, must be able to access a web server.
Why a Private Subnet – Resources such as databases may require internet access for updates/patches, but they should not accept requests from the internet. A private subnet is to be used in such cases.
Functioning
The structure of IP addresses makes it relatively easy for Internet routers to find the appropriate network to route data into. However, in a Class A network, for example, there may be millions of connected devices, and it may take some time for the data to find the correct device. This is where subnetting comes in: subnetting restricts the use of an IP address to a specific set of devices.
Because IP addresses are limited to indicating the network and the device address, they cannot be used to indicate which subnet an IP packet should go to. Routers in a network use a subnet mask to divide data into subnetworks.
IPv4 and IPv6 addresses – Public and Private Subnet
IPv4 addresses
Private IPv4 addresses (also referred to as private IP addresses in this topic) are not public and can only be used to communicate between instances within your VPC. When you launch an instance into a VPC, the instance’s default network interface receives a primary private IP address from the IPv4 address range of the subnet (eth0). Each instance is also assigned a private (internal) DNS hostname that resolves to its own IP address. Hostnames are classified into two types: resource-based and IP-based. If you do not specify a primary private IP address, we will assign you an IP address in the subnet range that is available. More information about network interfaces can be found in Elastic Network Interfaces in the Amazon EC2 User Guide for Linux Instances.
Every subnet has an attribute that determines whether a network interface created in the subnet receives a public IPv4 address automatically (also referred to as a public IP address in this topic). As a result, when you launch an instance into a subnet with this attribute enabled; a public IP address is assigned to the instance’s primary network interface (eth0). Through network address translation, a public IP address is mapped to the primary private IP address (NAT).
IPv6 addresses
If an IPv6 CIDR block is associated with your VPC and subnet, and one of the following conditions is met, your instance in a VPC receives an IPv6 address:
- Your subnet is set up to automatically assign an IPv6 address to an instance’s primary network interface during launch.
- During the launch process, you manually assign an IPv6 address to your instance.
- After your instance is ready to launch, you assign it an IPv6 address.
- After launching your instance, you assign an IPv6 address to a network interface in the same subnet and connect the network interface to it.
When your instance receives an IPv6 address during startup, the address is associated with the instance’s primary network interface (eth0). The IPv6 address can be separate from the primary network interface. For your instance, we do not support IPv6 DNS hostnames.
When you stop and restart your instance, an IPv6 address is retained, and it is released when you terminate it. You cannot reassign an IPv6 address while it is assigned to another network interface; you must first unassign it. IPv6 addresses are globally unique and can be set as private or public on the Internet. By configuring your subnet’s routing or using security groups and network ACL rules, you can control whether instances can reach using their IPv6 addresses.