Microsoft is recognized globally for providing solutions to many businesses, organizations, and individuals through its various services. And, for creating this running environment, it is important to keep all the crucial data, files, and information safe and secure. In order to do this, Microsoft offers Azure Active Directory services. This is a universal platform for managing and securing identities.
To better understand the Azure AD concept, in this blog, we will cover all the important areas of this service. So, let’s begin with an overview!
What is Azure Active Directory?
For every business or organization, it is important to protect users’ data. Related to this, Microsoft offers Azure Active Directory (Azure AD), this is a universal identity platform that provides single sign-on and multi-factor authentication for protecting users from cybersecurity attacks. This is basically a cloud-based identity and access management service for helping employees to sign in and access resources in:
- Firstly, external resources like Microsoft 365, the Azure portal, and other SaaS applications.
- Secondly, internal resources like apps on your corporate network and intranet or cloud apps originated by the organization.

Who can use Azure AD?
Azure AD is intended for:
1. IT admins
IT admin can use Azure AD for managing application access depending on your business needs. For example, you can use Azure AD for requiring multi-factor authentication while accessing important organizational resources.
2. App developers.
App developers can use Azure AD as a standards-based method for adding a single sign-on (SSO) to your app by allowing it to operate with a user’s pre-existing credentials. Further, this also offers APIs that can help in creating a personalized app experience using existing organizational data.
3. Microsoft 365, Office 365, Azure, or Dynamics CRM Online subscribers
Subscribers already use Azure AD. That is to say, every Microsoft 365, Office 365, Azure, and Dynamics CRM Online tenant is automatically an Azure AD tenant. They can immediately start managing access to integrated cloud apps.
What are the functions of Azure AD?
There are many unique features of Azure Active Directory that make it useful in the market. Some of them include:
1. Connecting workforce
Azure AD provides smooth access to all apps for always staying productive whether on-site or remote. This helps in automating workflows for user lifecycle and provisioning thus saving time and resources with self-service management.
2. Option to choose numerous SaaS apps
Azure AD offers access to thousands of pre-integrated software as a service (SaaS) applications.
3. Protecting and governing access
This protects user credentials by applying strong authentication and conditional access policies. Moreover, it systematically handles identities by ensuring that the valid people have valid access to the valid resources.
4. Engaging with your customers and partners
Azure AD allows you to secure and manage customers and partners beyond your organizational boundaries using one identity solution. Moreover, you can personalize user journeys and clarify authentication with social identity, and more.
5. Integrating identity into your apps
This lets you advance the adoption of your application in the enterprise by supporting single sign-on and user provisioning. Moreover, it lowers the sign-in friction and automates the creation, removal, and maintenance of user accounts.
Abiove we have covered the basic functionalities of Azure AD. In this next section, we will talk about the essential Azure AD features used by the organizations.
Working Features of Azure AD
Azure AD provides access to the following features for organizations:
1. Application management
Azure AD helps in managing your cloud and on-premises apps using Application Proxy, single sign-on, the My Apps portal, and SaaS apps.
2. Authentication
This is for managing Azure Active Directory self-service password reset, MFA, custom banned password list, and smart lockout.
3. Azure Active Directory for developers
Azure AD helps in creating apps that sign in all Microsoft identities, acquire tokens to call Microsoft Graph, and other Microsoft APIs.
4. Business-to-Business (B2B)
Azure AD manages your guest users and external partners while maintaining control over corporate data.
5. Business-to-Customer (B2C)
You can personalize and manage users’ sign-up, and sign-in processes. And, can control their profiles when using your apps.
6. Conditional Access
Azure AD can manage access to your cloud apps.
7. Device Management
Azure AD provides you control over cloud or on-premises devices’ access to corporate data.
8. Hybrid identity
Use Azure Active Directory Connect and Connect Health for providing a single user identity for authentication and authorization to all resources.
9. Identity governance
Control your organization’s identity via employee, business partner, vendor, service, and app access controls.
10. Identity protection
This can identify potential vulnerabilities affecting your organization’s identities, configuring policies to respond to suspicious actions, and taking appropriate action for resolving them.
12. Managed identities for Azure resources
In this, Azure services get an automatically managed identity for authenticating any Azure AD-supported authentication service, including Key Vault.
13. Privileged identity management (PIM)
Managing, controlling, and monitoring access within your organization. This can provide access to resources in Azure AD and Azure and other Microsoft Online Services.
Azure Active Directory architecture
Azure AD’s geographically allocated architecture integrates extensive monitoring, automated rerouting, failover, and recovery abilities for delivering company-wide availability and performance to customers. However, the architecture elements include:
1. Service architecture design
The most basic way for creating an accessible and usable system is by using independent building blocks or scale units. For the Azure AD data tier, scale units are known as partitions.
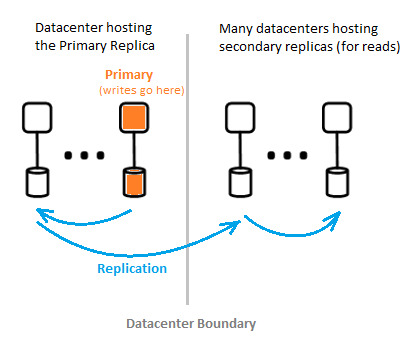
However, there are two components of a single-directory partition:
1. Primary replica
The primary replica gets all writes for the partition it belongs to. Any write operation is immediately recreated to a secondary replica in several datacenters before returning success to the caller for ensuring geo-redundant durability of writes.
2. Secondary replicas
All directory reads are serviced from secondary replicas, which are at data centers that are physically located over several geographies. Further, the secondary replicas oversee the read scalability.
2. Scalability
Scalability refers to the ability of a service to enhance to meet increasing performance demands. However, write scalability is accomplished by partitioning the data. And, read scalability is accomplished by replicating data from one partition to multiple secondary replicas allocated throughout the world.
3. Continuous availability
Availability specifies the ability of a system for performing uninterrupted. However, the solution to Azure AD’s high availability is that the services can instantly shift traffic over multiple geographically allocated datacenters. Where every data center is independent and enables de-correlated failure modes. This covers:
1. Fault tolerance
2. Data durability
4. Datacenters
Azure AD’s replicas are placed in data centers located globally. However, the Azure AD works over datacenters with the following features:
- Firstly, authentication, Graph, and other AD services reside behind the Gateway service. The Gateway controls the load balancing of these services. Further, it automatically failover if any unhealthy servers are detected using transactional health probes.
- Secondly, for reads. The directory has secondary replicas and corresponding front-end services in an active-active configuration operating in multiple datacenters. However, if there is any failure in the data center then, the traffic will automatically get routed to a different data center.
In the next section, we will learn the differences and similarities between AD and Azure AD based on various areas.
Comparing Active Directory and Azure Active Directory
In this, we will outline the differences and similarities between Active Directory concepts and Azure Active Directory.
1. Users
- In Active Directory, organizations create internal users manually or use an automated provisioning system like the Microsoft Identity Manager for integrating with an HR system. And, it creates external users manually as regular users in a dedicated external AD forest. Thus, resulting in administration overhead for managing the lifecycle of external identities. In this, the administrators make users members of groups.
- In Azure Active Directory, the existing AD organizations use Azure AD Connect for syncing identities to the cloud. Moreover, it adds support for automatically creating users from cloud HR systems. This can supply identities in SCIM enabled SaaS apps for automatically providing apps with the necessary details for allowing access for users. Further, it also offers a special class of identity for supporting external identities. Here, administrators can use Entitlement management in Azure AD for providing users access to a collection of apps and resources using workflows.
2. Applications
- Active Directory structures the basis for many infrastructure on-premises components like DNS, DHCP, IPSec, WiFi, and VPN access However, it doesn’t support SaaS apps natively and needs a federation system like AD FS. In this, the organizations can use AD FS with Active Directory for supporting LOB apps needing modern authentication.
- Azure AD refers to the new control plane for accessing apps versus depending on networking controls. However, when users authenticate, Conditional access (CA), will manage which users have access to which apps under required circumstances. Moreover, it supports SaaS apps with OAuth2, SAML, and WS-* authentication for using Azure AD for authentication. Further, LOB apps needing modern authentication can be configured for using Azure AD for authentication.
3. Devices
- Active Directory doesn’t naturally support mobile devices without third-party solutions. It offers the ability to domain join Windows devices for managing them using Group Policy, System Center Configuration Manager, or other third-party solutions. Further, it also provides strong management abilities for on-premises Windows servers using Group Policy or other management solutions.
- In Azure AD, Microsoft’s mobile device management solution and Microsoft Intune are integrated. However, the Windows devices can be joined to Azure AD. In which, the conditional access can examine if a device is Azure AD joined as part of the authentication process. Further, the Windows server’s virtual machines in Azure can be controlled with Azure AD Domain Services.
Now, we have covered all the details of Azure AD. Its time to get started with Azure AD by creating a tenant.
Creating a new tenant in Azure AD
Using the Azure AD portal, you can perform all of your administrative tasks including creating a new tenant for your organization.
For creating a new tenant:
- Firstly, sign in to your organization’s Azure portal.
- Secondly, select Azure Active Directory from the Azure portal menu.
- Thirdly, select Create a tenant.
- Then, select the type of tenant you want to create on the Basics tab. This can be either Azure Active Directory or Azure Active Directory (B2C).
- Now, select Next: Configuration for moving on to the Configuration tab.
- After that, enter the following information on the Configuration tab:
- In the Organization name box, type Contoso Organization into.
- In the Initial domain name box, type Contosoorg.
- Leave the United States option in the Country or region box.
- Lastly, select Next: Review + Create. Here, you can examine the information you entered to see if it is correct. Then, select create.
After creating a new Azure AD tenant, you become the first user of that tenant. That is to say, you will automatically get assigned the Global Admin role.
For deleting the tenant, use the following steps:
- Firstly, check that you’re signed in to the directory that you want to delete using the Directory + subscription filter in the Azure portal.
- Secondly, select Azure Active Directory, and then, select Delete directory on the Contoso – Overview page.
Viewing organization’s groups and members in Azure AD
Using Azure Portal, you can view your organization’s existing groups and group members. However, the groups are used for managing users that all require the same access and permissions for potentially restricted apps and services.
1. Creating a new group
- Firstly, select Azure Active Directory, Groups. After that, select New group.
- Secondly, complete the Group page:
- Firstly, Group type: Select Security
- Secondly, Group name: Type MDM policy – West
- Then, Membership type: Select Assigned.
- Lastly, select Create.
2. Create a new user
You must know that a user must exist before being added as a group member. For this, check the “Custom domain names” tab first for getting the verified domain name in which to create users.
- Firstly, select Azure Active Directory, Users. After that, select New user.
- Secondly, complete the User page:
- Firstly, Name: Type ABC.
- Secondly, User name: Type [email protected].
- Lastly, copy the auto-generated password provided in the Password box. Then, select Create.
3. Adding a group member
After creating a group and a user, you can add ABC as a member to the MDM policy – West group.
- Firstly, select Azure Active Directory > Groups.
- Secondly, search for and select the MDM policy – West group from the Groups – All groups page.
- Then, select Members from the Manage area from the MDM policy – West Overview page.
- After that, select Add members, and then search and select ABC.
- Lastly, choose Select.
4. Viewing all groups
You can view all the groups for your organization on the Groups – All groups page of the Azure portal.
- Just, select Azure Active Directory > Groups. Then, the Groups – All groups page will appear.
5. Searching for the group
- Firstly, type MDM into the Search box from the Groups – All groups page.
- Secondly, select the group MDM policy – West.
- Lastly, view the group information on the MDM policy – West Overview page.
6. Viewing group members
Firstly, select Members from the Manage area. After that, examine the complete list of member names allocated to that specific group.
Azure Active Directory (AD) pricing
Microsoft Azure Active Directory is a complete identity and access management cloud solution that is a combination of core directory services, application access management, and advanced identity protection. The pricing option of Azure AD are:
1. Premium P1
This is designed for empowering organizations with more demanding identity and access management requirements. In other words, the Azure Active Directory Premium edition adds feature-rich enterprise-level identity management capabilities and provides hybrid users smooth access to on-premises and cloud capabilities. This edition contains all the information about worker and identity administrators in hybrid environments over application access, self-service IAM, and security in the cloud.
2. Premium P2
Azure Active Directory Premium P2 contains all the features of all other Azure Active Directory editions build up with advanced identity protection and privileged identity management capabilities.
3. Azure Active Directory Free
This offers:
- Firstly, user and group management
- Secondly, on-premises directory synchronization
- Thirdly, basic reports
- Next, self-service password change for cloud users
- Lastly, single sign-on over Azure, Microsoft 365, and popular SaaS apps.
Final Words
Above we have covered the in-depth details about Azure Active Directory (AD) including its features, uses, and working architecture. However, with having the trust of top companies like Walmart, Uniper, and Amtrak, Azure AD is providing authentication solutions for making the environment safe and secure. To better understand this service, you can go through the Microsoft documentation and learn about the important areas of Azure AD. So, start your journey with the Azure AD and share your experiences as well as doubts in the comments.



