Microsoft 365 – Threat Protection
This tutorial will help you to know about the threat protection in Microsoft 365 and its management. Digital estates are growing more complex. Devices, data, networks, apps, and identities are among them, some of which your company may control and others that it does not. As a result of this expansion, the attack surface has grown to the point that no single service can cover it all:
- Firstly, protect an organization from attack
- Subsequently, rapidly detect malicious activity
- Furthermore, effectively respond to and remediate threats across the digital estate
That’s why Microsoft has developed different services that specialize in protecting against various threat vectors such as endpoints, networks, email, and business critical data. These services integrate via Microsoft Graph.
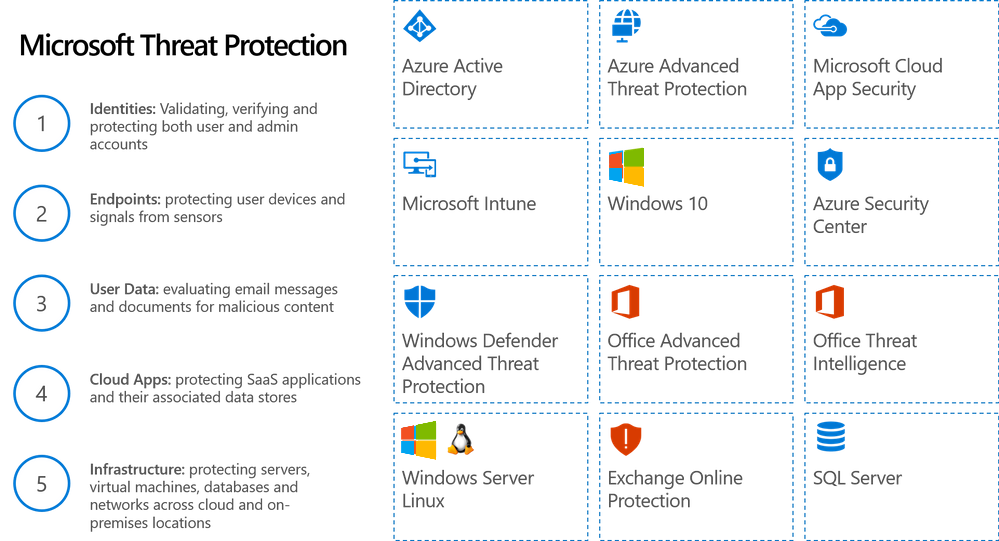
Azure Active Directory Identity Protection
- Azure Active Directory uses adaptive machine learning algorithms and heuristics to detect anomalies and suspicious incidents that indicate potentially compromised identities. Identity Protection creates reports and warnings based on this information, allowing you to assess problems and take action.
- You can define risk-based rules that automatically respond to concerns using Azure Active Directory Identity Protection, which is more than just a monitoring and reporting tool.
- These rules, in combination with other Azure Active Directory and EMS conditional access restrictions, can either prohibit or initiate remedial activities like as password resets and multifactor authentication.
Azure Advanced Threat Protection (ATP)
- Advanced Threat Protection (ATP) is a cloud-based security system that discovers, detects, and assists you in investigating advanced threats, compromised identities, and harmful insider acts directed against your company.
- Through security reports and user profile analytics, Azure ATP helps reduce your attack surface, making it harder to compromise user credentials and advance an attack.
Azure Security Center
- Azure Security Center provides unified security management and advanced threat protection across hybrid cloud workloads.
- Get an unified picture of security across your on-premises and cloud workloads, and apply security rules to guarantee compliance with security requirements.
- Security data may be gathered, searched, and analysed from a range of sources, including firewalls and partner solutions.
Microsoft Cloud App Security
Microsoft Cloud App Security gives you insight into your cloud applications and services, as well as analytics to help you discover and battle cyberthreats and govern how your data moves. The cloud app security framework aids you in the following ways:
- Firstly, Discover and control the use of Shadow IT
- Secondly, Protect your sensitive information anywhere in the cloud
- Furthermore, Protect against cyberthreats and anomalies
- Lastly, Assess the compliance of your cloud apps
Microsoft Exchange Online Protection (EOP)
- Microsoft Exchange Online Protection (EOP) is a cloud-based email filtering service that helps protect against spam and malware and includes features to safeguard against messaging-policy violations.
- EOP can help you manage your messaging environment more easily and relieve many of the difficulties that come with on-premises hardware and software.
Microsoft Intune
- Microsoft Intune, which is part of Microsoft Endpoint Management (MEM), works in tandem with other endpoint management components such as Azure Active Directory (Azure AD) for identity and access control and Azure Information Protection for data security.
- When combined with Microsoft 365, you can help your users be more productive across all of their devices while also securing your data.
Office 365 Advanced Threat Protection
- Because email is one of the most common ways for malware to enter your company, Advanced Threat Protection can detect threats before they reach a user’s inbox.
- This feature, is also included in Microsoft 365 E5 subscriptions, provides protection by scanning email and URLs, identifying malicious files, and detecting when someone tries to impersonate one of your users to access your organization’s data.
Office 365 Threat Intelligence
- The Microsoft 365 security center’s Office 365 Threat Intelligence is a repository of insights and information. As a result, Office 365 Threat Intelligence keeps an eye on signals and collects data from a variety of sources, including user behaviour, authentication, email, infected PCs, and security events.
- You can use this information to understand and respond to threats against users and intellectual property.
Windows Defender Advanced Threat Protection (ATP)
- Windows Defender Advanced Threat Protection (ATP) helps you prevent, detect, investigate, and respond to advanced threats. Also, Windows Defender ATP uses technologies built into Windows 10 that connect to Microsoft’s cloud services.
- Endpoint behavior sensors collect data and send it to cloud security analytics, Microsoft optics that use big data and machine learning to turn behavioral data into insights, detections, and recommended responses.
- ATP also uses threat intelligence collected from Microsoft hunters, security teams, and partners to identify attacker tools and generate alerts when it detects them in data from the endpoint sensors.
Windows 10
Windows 10 includes built-in security protections to help safeguard against viruses, phishing, and malware.
- Firstly, BitLocker and credential guard help protect the integrity of the boot process and user credentials.
- Also, Windows Hello uses biometric authentication (fingerprints and facial recognition) to guard against potential spoofing.
- Subsequently, Windows Information Protection (WIP) helps protect enterprise apps and data against accidental data leaks on both enterprise-owned and personal devices.
Reference Documentation – Threat protection in Microsoft 365

