Application Security Groups and Bastion
This tutorial will help you to understand about Application Security Groups and Bastion. Application security groups helps you to configure network security as a natural extension of an application’s structure. It also allows you to group virtual machines and also, define network security policies based on the available groups.
Allow-HTTP-Inbound-Internet
There is a rule which is needed to allow traffic from the internet to the web servers. Because the inbound traffic from the internet is not acceptable by the DenyAllInbound default security rule, no additional rule is needed for these – AsgLogic or AsgDb application security groups.
| Priority | Source | Source ports | Destination | Destination ports | Protocol | Access |
|---|---|---|---|---|---|---|
| 100 | Internet | * | AsgWeb | 80 | TCP | Allow |
Deny-Database-All
Because of the AllowVNetInBound default security rule allowing all communication between resources in the identical virtual network, the above mentioned rule is also needed to deny traffic from all resources.
| Priority | Source | Source ports | Destination | Destination ports | Protocol | Access |
|---|---|---|---|---|---|---|
| 120 | * | * | AsgDb | 1433 | Any | Deny |
Allow-Database-BusinessLogic
The above mentioned rule allows traffic from the AsgLogic application security group to the AsgDb application security group. Subsequently, The priority for this rule is higher than the priority for the Deny-Database-All rule. However, this rule is processed before the Deny-Database-All rule, so traffic from the AsgLogic application security group is permitted, whereas all other traffic is blocked.
| Priority | Source | Source ports | Destination | Destination ports | Protocol | Access |
|---|---|---|---|---|---|---|
| 110 | AsgLogic | * | AsgDb | 1433 | TCP | Allow |
Creating a bastion host
When you will be creating a bastion host in the portal by using an existing virtual machine, various settings will automatically default to correspond to your virtual machine and/or virtual network.
- Firstly, Visit the Azure portal. Go to your virtual machine, then select Connect.
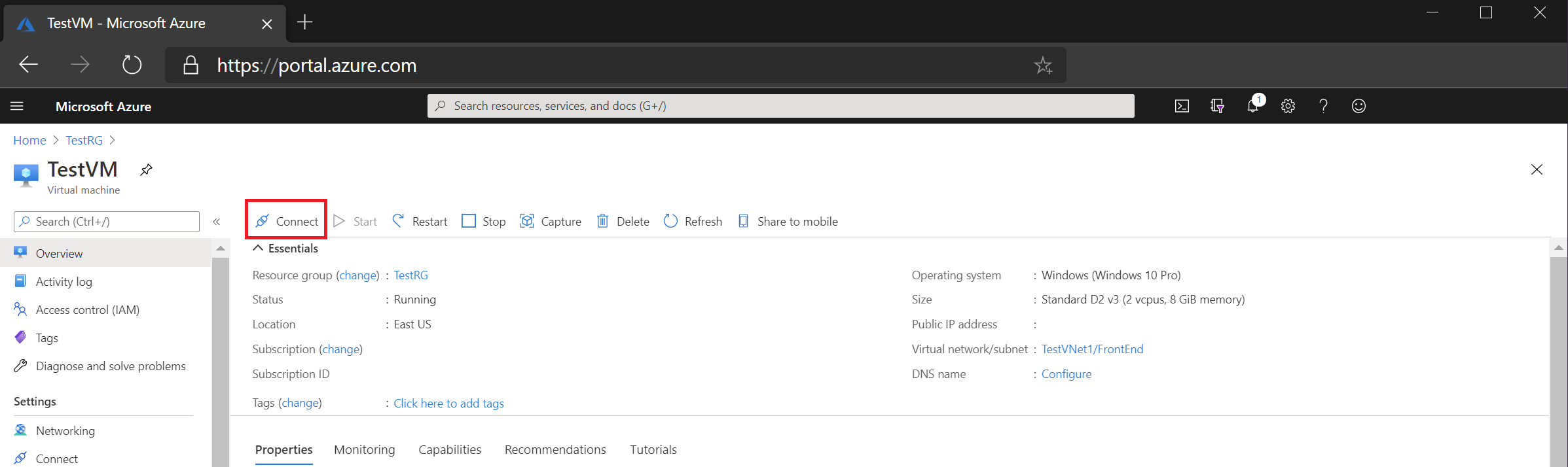
- Also, From the dropdown, choose Bastion.
- Subsequently, On the Connect page, choose Use Bastion.
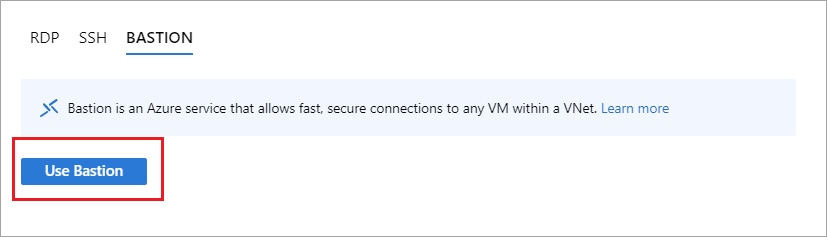
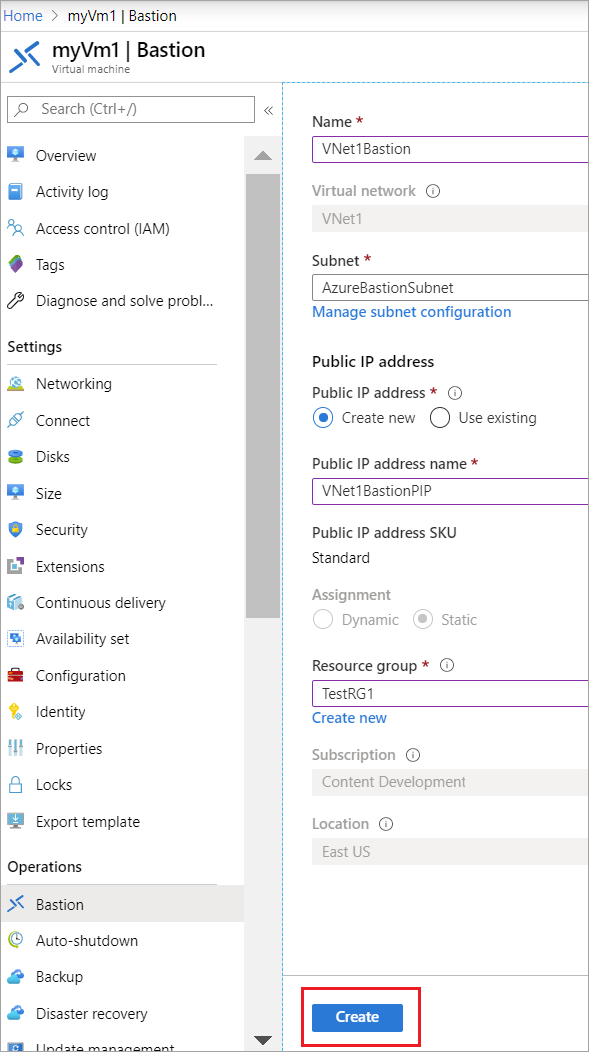
On the Bastion page, type the following settings as per your needs:
- Firstly, Name: Name the bastion host
- Subsequently, Subnet: The subnet inside your virtual network to which Bastion resource will be deployed.
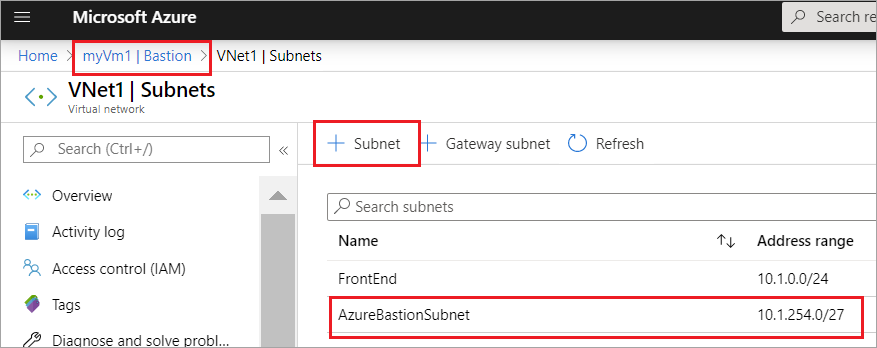
- Choose Manage subnet configuration, then click + Subnet.
- On the Add subnet page, search AzureBastionSubnet.
- You have to now Specify the address range in CIDR notation. For example, 10.1.254.0/27.
- Choose OK to create the subnet. At the top of the page, navigate back to Bastion to complete the rest of the necessary settings.
- Public IP address: Fill out public IP of the Bastion resource on which RDP/SSH will be accessed (over port 443). Choose a new public IP, or use an existing one.
- Public IP address name: Specify The name of the public IP address resource.
Finally, On the validation screen, select Create. Wait for arround 5 minutes for the Bastion resource create and deploy.
Connect
After Bastion has been deployed to the virtual network, the screen will display the connect page.
- Firstly, Type the username and password for your virtual machine. Then, choose Connect.
- Subsequently, The RDP connection to this virtual machine via Bastion will be displayed directly in the Azure portal (over HTML5) using port 443 and also the Bastion service.
Clean up resources
When you’re completed with using the virtual network and the virtual machines, remove the resource group and all of the resources it contains:
- Firstly, Type TestRG1 in the Search box at the top of the portal and choose TestRG1 from the search results.
- Subsequently, choose Delete resource group.
- Type TestRG1 for TYPE THE RESOURCE GROUP NAME and click Delete.
Reference documentation – Application security groups
Quickstart: Connect to a virtual machine using a private IP address and Azure Bastion

