What is Azure Network Security Groups?
In this, we will learn the Azure Network Security Groups and its rule.
You can use an Azure network security group for filtering network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. However, for each rule, you can specify source and destination, port, and protocol.
Security rules
A network security group contains zero, or as many rules as desired, within Azure subscription limits. Each rule specifies the following properties:
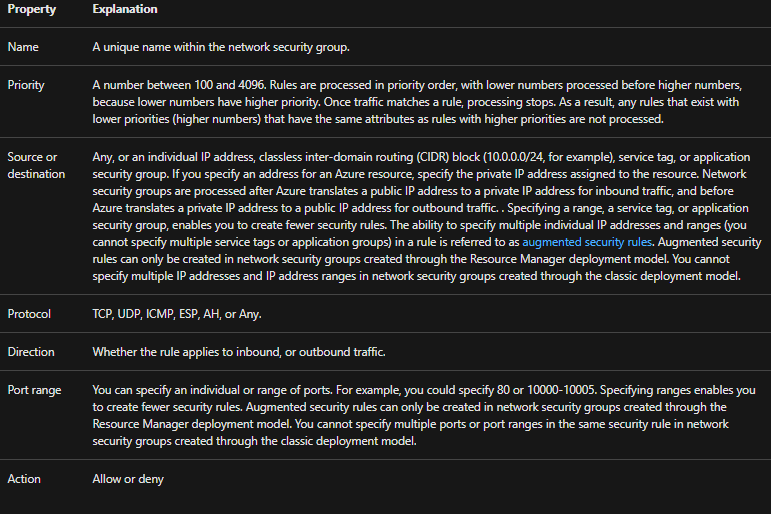
Network security group security rules evaluate by priority using the 5-tuple information to allow or deny the traffic. You may not create two security rules with the same priority and direction. A flow record get creates for existing connections. Communication allowance or deny depends on the connection state of the flow record. The flow record allows a network security group to be stateful. However, if you specify an outbound security rule to any address over port 80, for example, it’s not necessary to specify an inbound security rule for the response to the outbound traffic. You only need to specify an inbound security rule if communication initiates externally. The opposite is also true.
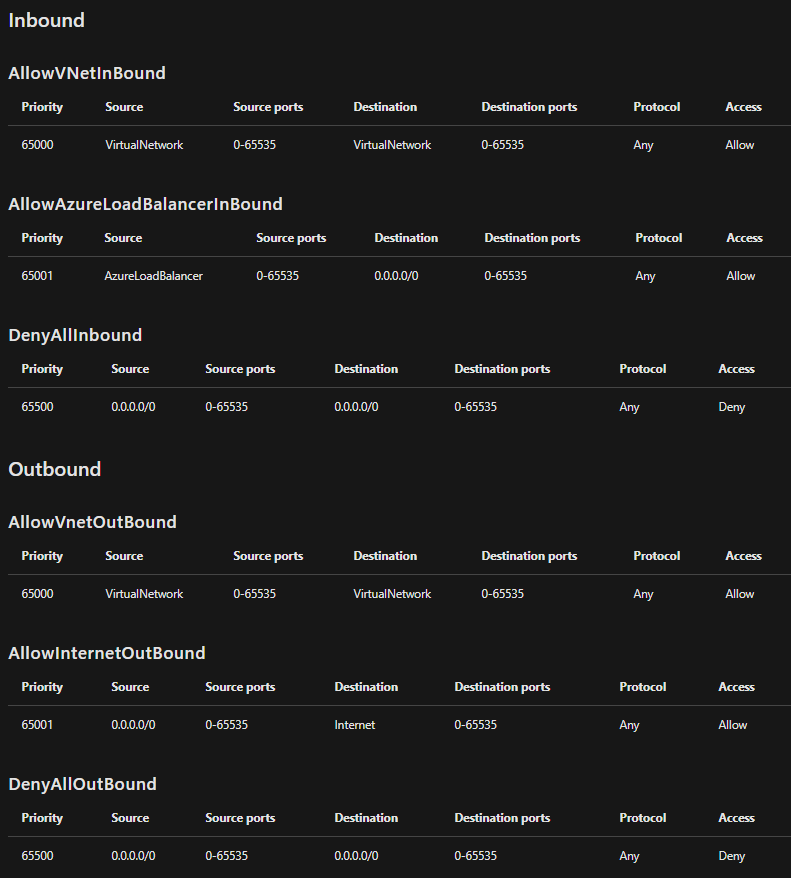
Default security rules
Azure creates the following default rules in each network security group that you create:
Azure platform considerations
- Firstly, Virtual IP of the host node. Basic infrastructure services like DHCP, DNS, IMDS, and health monitoring are provided through the virtualized host IP addresses 168.63.129.16 and 169.254.169.254. These IP addresses belong to Microsoft and are the only virtualized IP addresses used in all regions for this purpose. Further, for overriding this basic infrastructure communication, you can create a security rule to deny traffic by using the service tags on your Network Security Group rules.
- Secondly, Licensing (Key Management Service). Windows images running in virtual machines must have a license. To ensure licensing, a request is sent to the Key Management Service host servers that handle such queries. The request outbounds through port 1688.
- Thirdly, Virtual machines in load-balanced pools. The source port and address range applied are from the originating computer, not the load balancer. The destination port and address range are for the destination computer, not the load balancer.
- Then, Azure service instances. Instances of several Azure services, such as HDInsight, Application Service Environments, and Virtual Machine Scale Sets deploy in virtual network subnets.
- Lastly, Sending outbound emails. Microsoft recommends that you utilize authenticated SMTP relay services to send email from Azure Virtual Machines. SMTP relay services specialize in sender reputation, to minimize the possibility that third-party email providers reject messages.
Reference: Microsoft Documentation


