View effective security rules
In this we will learn about the effective security rules for each network interface attached to a virtual machine. And, we will cover the effective routes and various permissions for tasks.
However, effective security rules are a combination of the rules you’ve created in a network security group and default rules. Understanding this may help you to communicate to or from a virtual machine. Next, you can view the effective rules for any network interface that is attached to a running virtual machine.
- Firstly, in the search box at the top of the portal, enter the name of a virtual machine.
- Then, select Networking under SETTINGS.
- Thirdly, select the name of a network interface.
- After that, select Effective security rules under SUPPORT + TROUBLESHOOTING.
- Lastly, review the list of effective security rules. This is to determine if the correct rules exist for your required inbound and outbound communication.
Commands
- Azure CLI: az network nic list-effective-nsg
- PowerShell: Get-AzEffectiveNetworkSecurityGroup
View effective routes
The effective routes for the network interfaces attached to a virtual machine are a combination of default routes, any routes you’ve created, and any routes propagated from on-premises networks via BGP through an Azure virtual network gateway. Understanding the effective routes for a network interface may help you determine why you’re unable to communicate to or from a virtual machine. However, you can view the effective routes for any network interface that is attached to a running virtual machine.
- Firstly, in the search box at the top of the portal, enter the name of a virtual machine you want to view effective security rules for.
- Secondly, select Networking under SETTINGS.
- Thirdly, select the name of a network interface.
- Then, select Effective routes under SUPPORT + TROUBLESHOOTING.
- Lastly, review the list of effective routes to determine if the correct routes exist for your required inbound and outbound communication.
Permissions
For performing tasks on network interfaces, your account must be assigned to the network contributor role or to a custom role that is assigned the appropriate permissions listed in the following table:
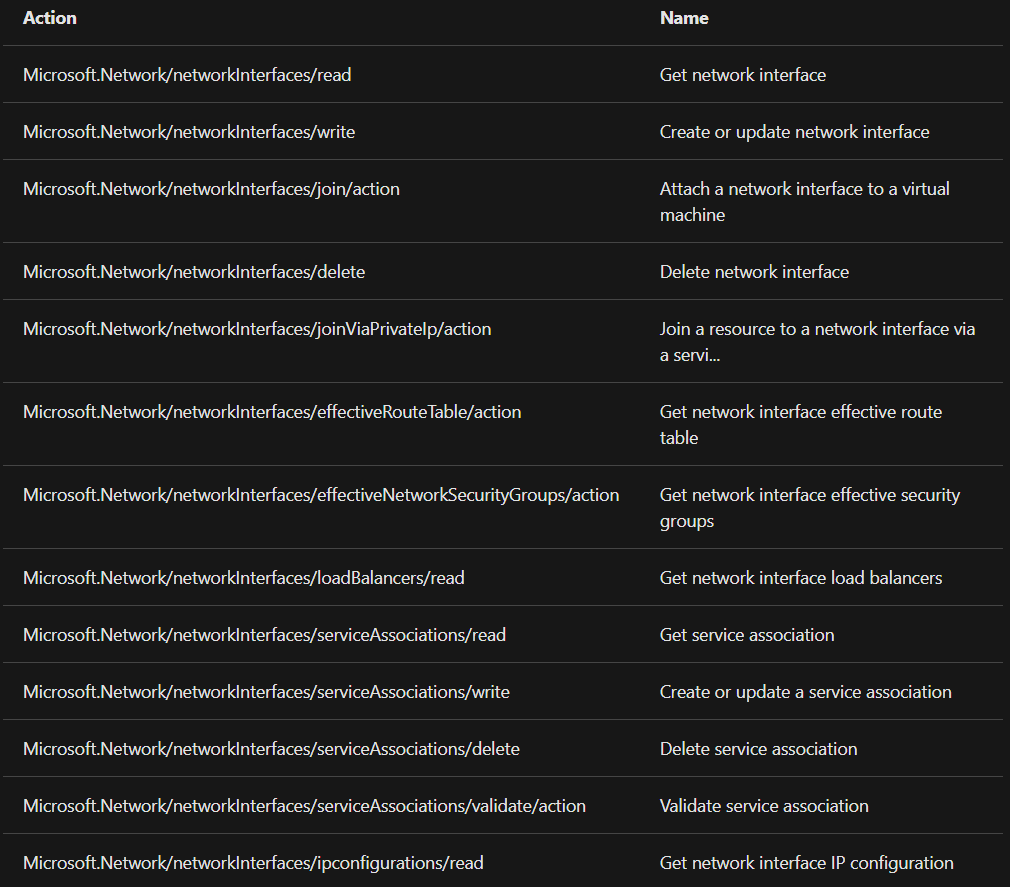
Reference: Microsoft Documentation


