Understanding Keys, Secrets and Certificates
We will study and comprehend Azure Keys, Secrets, and Certificates in this tutorial.
Azure Key Vault, on the other hand, allows Microsoft Azure apps and users to store and access a variety of secret/key data:
- Firstly, the cryptographic keys that support multiple key types and algorithms. Moreover, it enables the use of Hardware Security Modules (HSM) for high-value keys.
- Secondly, Secrets that provides secure storage of secrets, such as passwords and database connection strings.
- Thirdly, certificates that support certificates built on top of keys and secrets and add an automated renewal feature.
- Lastly, Azure Storage is for managing keys of an Azure Storage accounts for you. Internally, Key Vault can list (sync) keys with an Azure Storage Account. Further, it regenerates (rotate) the keys periodically.
Data types
Referring to the JOSE specifications for relevant data types for keys, encryption, and signing.
- Firstly, an algorithm, that is a supported algorithm for a key operation. For example, RSA1_5
- Secondly, ciphertext-value, this includes ciphertext octets that encodes using Base64URL
- Thirdly, digest-value in which the output of a hash algorithm that encodes using Base64URL
- Then, key-type, this has one of the supported key types, for example RSA (Rivest-Shamir-Adleman).
- After that, plaintext-value this includes plaintext octets that encodes using Base64URL
- Next, signature-value – output of a signature algorithm that encodes using Base64URL
- base64URL – a Base64URL [RFC4648] encodes binary value
- boolean – this is either true or false
- Then, Identity – this an identity from Azure Active Directory (AAD).
- Lastly, IntDate – a JSON decimal value representing the number of seconds from 1970-01-01T0:0:0Z UTC until the specified UTC date/time.
Objects, identifiers, and versioning
- Objects in Key Vault are versioned whenever a new instance of an object is created. However, each version has a unique identifier and URL.And, when an object is first created, it’s given a unique version identifier and marked as the current version of the object.
- Thus, creation of a new instance with the same object name gives the new object a unique version identifier, causing it to become the current version.
- However, objects in Key Vault can be addressed by specifying a version or by omitting the version for operations on the current version of the object. When using a Key with the name MasterKey, for example, conducting activities without providing a version leads the system to utilise the most recent version available.
- Additionally, using the version-specific identifier instructs the system to utilise that particular version of the object.
- Further, the objects are uniquely identified within Key Vault using a URL. That means, no two objects in the system have the same URL, regardless of geo-location.
- Moreover, the complete URL to an object is the Object Identifier. And, the URL consists of a prefix that identifies the Key Vault, object type, user-provided Object Name, and an Object Version.
- Lastly, the Object Name is case-insensitive and immutable. And, the Identifiers that don’t include the Object Version refers to Base Identifiers.
An object identifier has the following general format:
“https://{keyvault-name}.vault.azure.net/{object-type}/{object-name}/{object-version}“
Where:
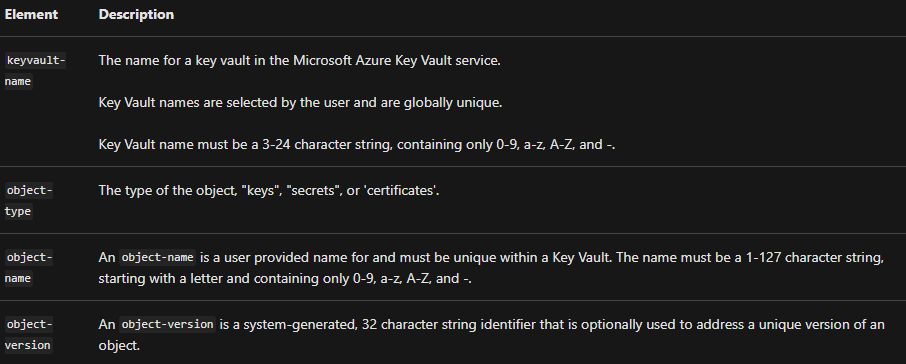
Reference: Microsoft Documentation
Prepare for Assured Success
Want to pass Microsoft Azure Security Technologies (AZ-500) Exam? Learn MoreAre you preparing for Microsoft Azure Security Technologies (AZ-500) Exam?Take a Quiz


