Site recovery network in Azure VM
AZ-304 is retired. AZ-305 replacement is available.
In this tutorial we will learn and understand network guidance when replicating and recovering Azure VM from one region to another, using Azure Site Recovery.
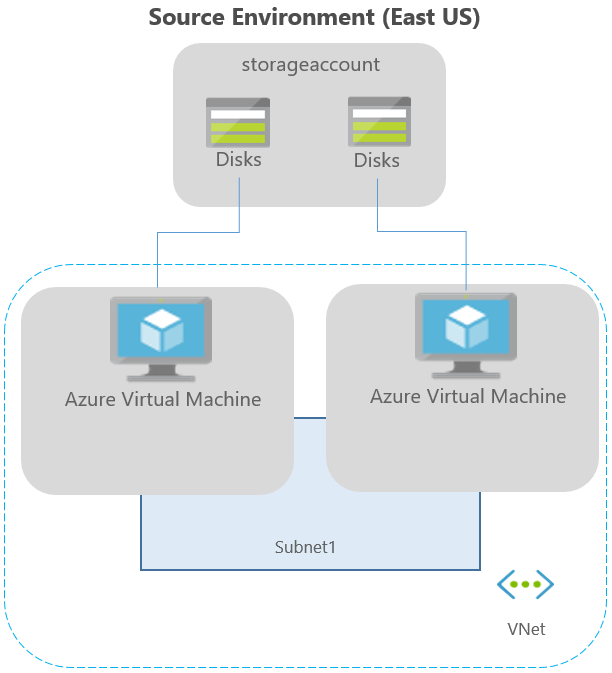
Typical network infrastructure
The diagram below represents a typical Azure environment, for applications running on Azure VMs:
However, if you are using Azure ExpressRoute or a VPN connection from your on-premises network to Azure, the environment is as follows:
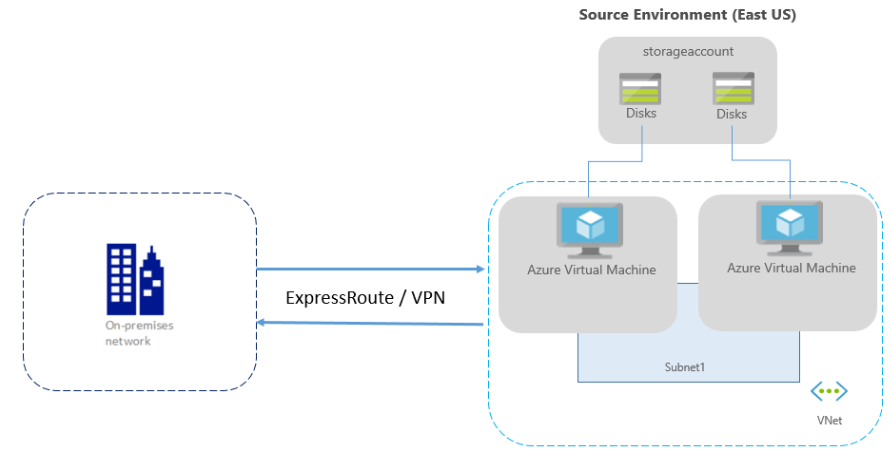
However, Typically, networks are protected using firewalls and network security groups (NSGs). Where the Firewalls use URL or IP-based whitelisting for controlling network connectivity. And, NSGs provide rules that use IP address ranges to control network connectivity.
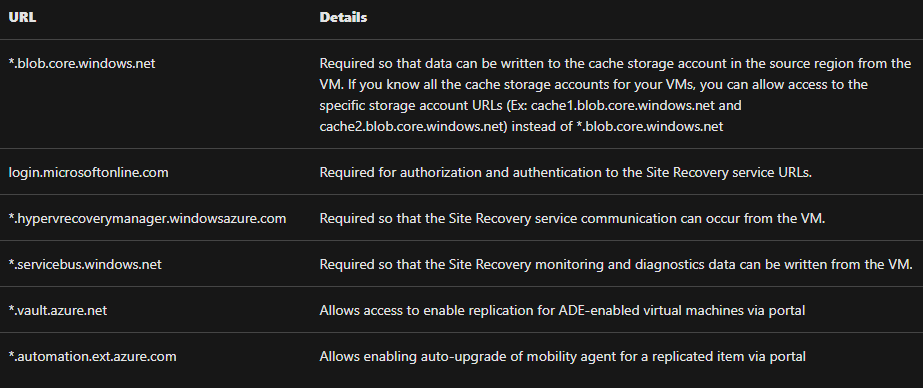
Outbound connectivity for URLs
If you are using a URL-based firewall proxy for controlling outbound connectivity, allow these Site Recovery URLs:
Outbound connectivity using Service Tags
If you are using an NSG for controlling outbound connectivity, these service tags need to be allowed.
- Firstly, for the storage accounts in the source region, create a Storage service tag-based NSG rule for the source region. And, allow these addresses to write data to the cache storage account, from the VM.
- Secondly, create an Azure Active Directory (AAD) service tag-based NSG rule for allowing access to all IP addresses corresponding to AAD
- Thirdly, create an EventsHub service tag-based NSG rule for the target region, allowing access to Site Recovery monitoring.
- Then, create an AzureSiteRecovery service tag-based NSG rule for allowing access to Site Recovery service in any region.
- Fifthly, create an AzureKeyVault service tag-based NSG rule. This is only necessary when enabling the replication of ADE-enabled virtual machines via portal.
- Lastly, create the required NSG rules on a test NSG. And verify that there are no problems before you create the rules on a production NSG.
NSG rules – East US
- Firstly, create an outbound HTTPS (443) security rule for “Storage.EastUS” on the NSG.
- Secondly, create an outbound HTTPS (443) security rule for “AzureActiveDirectory” on the NSG.
- Then, create an outbound HTTPS (443) security rule for “EventHub.CentralUS” on the NSG that corresponds to the target location for allowing access to Site Recovery monitoring.
- Lastly, create an outbound HTTPS (443) security rule for “AzureSiteRecovery” on the NSG for allowing access to Site Recovery Service in any region.
NSG rules – Central US
These rules are necessary for enabling replication from the target region to the source region post-failover:
- Firstly, create an outbound HTTPS (443) security rule for “Storage.CentralUS” on the NSG.
- Secondly, create an outbound HTTPS (443) security rule for “AzureActiveDirectory” on the NSG.
- Then, create an outbound HTTPS (443) security rule for “EventHub.EastUS” on the NSG that corresponds to the source location. This will provide access to Site Recovery monitoring.
- Lastly, create an outbound HTTPS (443) security rule for “AzureSiteRecovery” on the NSG for allowing access to Site Recovery Service in any region.
Network virtual appliance configuration
If you are using network virtual appliances (NVAs) for controlling outbound network traffic from VMs. Then, the appliance might get throttled if all the replication traffic passes through the NVA. So, we recommend creating a network service endpoint in your virtual network for “Storage” for replication traffic not to go to the NVA.
Creating network service endpoint for Storage
You can create a network service endpoint in your virtual network for “Storage” for the replication traffic to not leave Azure boundary.
- Firstly, select your Azure virtual network and click on ‘Service endpoints’
- Then, click ‘Add’ and ‘Add service endpoints’ tab opens
- Lastly, select ‘Microsoft.Storage’ under ‘Service’ and the required subnets under ‘Subnets’ field and click ‘Add’
Forced tunneling
You can override Azure’s default system route for the 0.0.0.0/0 address prefix using a custom route. Moreover, you can distract VM traffic to an on-premises network virtual appliance (NVA). However, if you’re using custom routes, then you should create a virtual network service endpoint in your virtual network for “Storage” for the replication traffic to not leave the Azure boundary.
Reference: Microsoft Documentation


