Sentinel providing integrated threat protection
In this tutorial, we will learn about the Sentinel providing integrated threat protection.
Microsoft Azure Sentinel is a scalable, cloud-native SIEM/SOAR solution that delivers intelligent security analytics and threat intelligence across the enterprise. Moreover, it provides a single solution for alert detection, threat visibility, proactive hunting, and threat response.
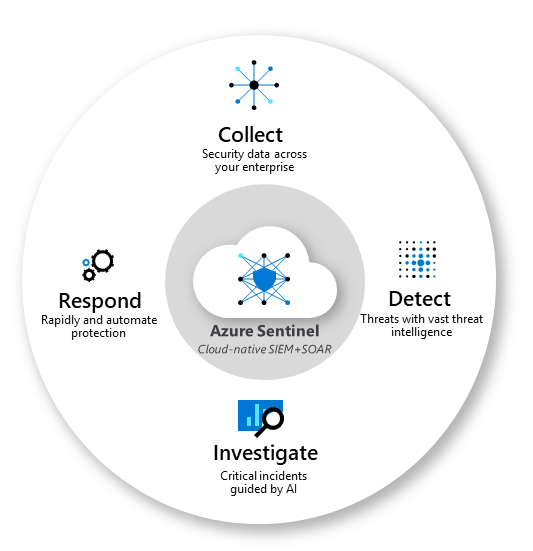
Above diagram shows the end-to-end functionality of Azure Sentinel.
- Firstly, Collecting data at cloud scale across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
- Secondly, Detecting previous threats and minimize false positives using analytics and unparalleled threat intelligence.
- Then, Investigating threats with AI and hunt suspicious activities at scale, tapping into decades of cybersecurity work at Microsoft.
- Lastly, Responding to incidents rapidly with built-in orchestration and automation of common security tasks.
Connecting Sentinel to your data
Azure Sentinel comes with many connectors for Microsoft solutions, available out of the box and providing real-time integration. This includes Microsoft 365 Defender (formerly Microsoft Threat Protection) solutions, and Microsoft 365 sources as well as Office 365, Azure AD, Microsoft Defender for Identity (formerly Azure ATP), Microsoft Cloud App Security, and more.
Firstly, you must have your data ingested into Azure Sentinel, for which you need data connectors. However, there are data connectors that cover a wide range of scenarios and sources, including but not limited to:
- syslog
- Windows Event Logs
- Common Event Format (CEF)
- Trusted Automated eXchange of Indicator Information (TAXII), for threat intelligence
- Azure
- AWS services
Workbooks
After you connect data sources to Azure Sentinel, you can monitor the data using the Azure Sentinel integration with Azure Monitor Workbooks. Here, you’ll see a canvas for data analysis and the creation of rich visual reports within the Azure portal. Through this integration, Azure Sentinel allows you to create custom workbooks across your data.
Analytics
Using built-in analytics alerts within the Azure Sentinel workspace, you’ll get notified when anything suspicious occurs. However, there are various types of alerts, some of which you can edit to your own needs.
Managing incidents in Azure Sentinel
An incident is created when an alert that you’ve enabled is triggered. However, you can do standard incident management tasks like changing status or assigning incidents to individuals for investigation in Azure Sentinel. And, it also has investigation functionality.
Security automation and orchestration
You can use Azure Sentinel for automating some of your security operations and make your security operations center (SOC) more productive. Azure Sentinel integrates with Azure Logic Apps, so you can create automated workflows, or playbooks, in response to events.
Playbooks
A security playbook is a collection of procedures that can help automate and orchestrate your response. It can be run manually or set to run automatically when specific alerts are triggered. Security playbooks in Azure Sentinel are based on Azure Logic Apps.
Hunting
Use Azure Sentinel’s powerful hunting search-and-query tools, based on the MITRE framework, for hunting proactively for security threats across your organization’s data sources, before an alert is triggered. After you discover which hunting query provides high-value insights into possible attacks, you can also create custom detection rules based on your query, and surface those insights as alerts to your security incident responders.
Integrated threat protection
Threat protection is a continuously evolving battlefront. Cybercriminals look for any vulnerability they can exploit to steal, damage, or extort company data, assets, and resources. However, Microsoft provides a suite of tools that give extended detection and response (XDR) through Microsoft 365 Defender and Azure Defender.

Reference: Microsoft Documentation


