Overview of Azure KeyVault and KeyVault operations
In this, we will discuss Azure Key Vault and how it enables Microsoft Azure applications including the use of Azure key vault. However, Azure key vault use and store several types of secret/key data:
- Firstly, cryptographic keys for supporting multiple key types and algorithms. It enables the use of Hardware Security Modules (HSM) for high-value keys.
- Secondly, secrets for providing secure storage of secrets, such as passwords and database connection strings.
- Then, certificates for supporting certificates built on top of keys and secrets and add an automated renewal feature.
- Lastly, Azure Storage manages the keys of an Azure Storage account for you. Internally, Key Vault can list-keys with an Azure Storage Account, and regenerate the keys periodically.
Uses of Azure Key Vault
- Firstly, it has centralized storage for application secrets in the Azure Key Vault that allows you to control their distribution. And, the Key Vault reduces the chances that secrets may be accidentally leaked. While using Key Vault, application developers no longer need to store security information in their application. As not having to store security information in applications eliminates the need to make this information part of the code.
- Secondly, in this, the secrets and keys are protection assurance is given by Azure using industry-standard algorithms, key lengths, and hardware security modules (HSMs). The HSMs here is Federal Information Processing Standards (FIPS) 140-2 Level 2 validated. However, access to a key vault requires proper authentication and authorization before a caller can get access. This authentication is via Azure Active Directory. Also, the authorization is via role-based access control (RBAC) or the Key Vault access policy.
- Lastly, it provides access to monitoring. That is to say, after creating a couple of Key Vaults, you will want to monitor how and when your keys and secrets are being accessed. So, you can monitor activity by enabling logging for your vaults. You can configure Azure Key Vault to:
- Firstly, archiving to a storage account.
- Secondly, streaming to an event hub.
- Thirdly, sending the logs to Azure Monitor logs.
Data types
There are various data types in Azure Key Vault that are:
- Firstly, algorithm, it refers to a supported algorithm for a key operation
- Secondly, ciphertext-value, it is ciphertext octets for which there is encoding using Base64URL
- Thirdly, digest-value, in this the output of a hash algorithm in which there is encoding is using Base64URL
- Fourthly, key-type. These are some of the supported key types, for example, RSA (Rivest-Shamir-Adleman).
- Then, plaintext-value, it has plaintext octets, encoded using Base64URL
- After that, signature-value, the output of a signature algorithm, encoded using Base64URL
- base64URL. A Base64URL [RFC4648] encoded binary value
- Then, boolean. It is either true or false
- Lastly, Identity. This defines an identity from the Azure Active Directory (AAD).
Objects, identifiers, and versioning
- Objects that are storer in Key Vault are versioned whenever there is a creation of a new instance of an object. However, each version has a unique identifier and URL. And, during the development of an object, a unique version identifier is allocated. And it is marked as the current version of the object. This creation of a new instance with the same object name gives the new object a unique version identifier, causing it to become the current version.
- However, objects in Key Vault can be addressed by specifying a version or by omitting the version for operations on the current version of the object. For example, given a Key with the name MasterKey, performing operations without specifying a version causes the system to use the latest available version.
- Unique identification of objects is within Key Vault using a URL. And, no two objects in the system have the same URL, regardless of geo-location. However, the complete URL for an object is Object Identifier. The URL includes a prefix for identifying the Key Vault, object type, user given Object Name, and an Object Version. The Object Name is case-insensitive and immutable. And, identifiers that do not include the Object Version are Base Identifiers.
General format of an object identifier:
“https://{keyvault-name}.vault.azure.net/{object-type}/{object-name}/{object-version}”
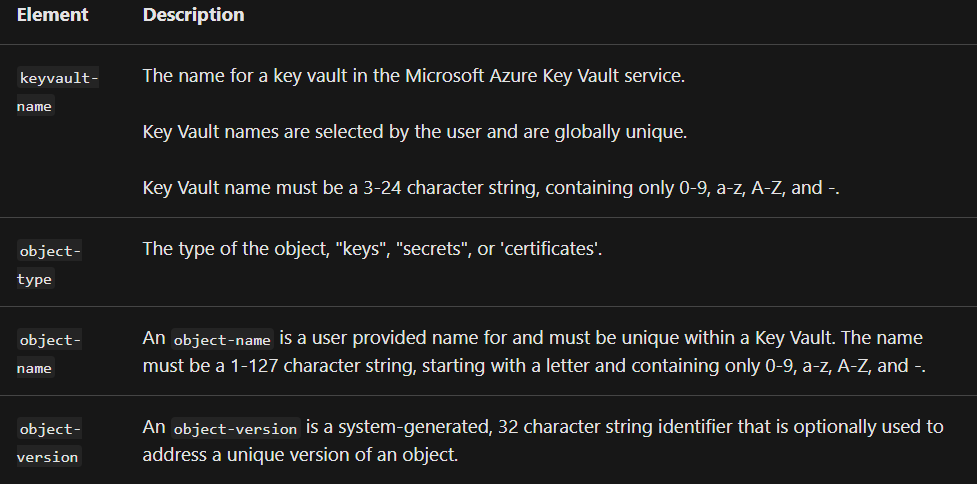
Reference: Microsoft Documentation
Are you preparing for Microsoft Azure Architect Design AZ-304 exam?Take a Quiz


