Overview of Azure AD Identity Governance
In this, we will learn a brief about Azure AD Identity Governance.
Azure Active Directory (Azure AD) Identity Governance allows you to balance your organization’s need for security and employee productivity with the right processes and visibility. It gives you the tools you need to make sure that the correct individuals have access to the right resources. However, by safeguarding, monitoring, and auditing access to important assets, Azure AD and Enterprise Mobility Security capabilities help you mitigate access risk.
Further, Identity Governance gives organizations the ability to do the following tasks. This work covers employees, business partners, and vendors, as well as on-premises and cloud-based services and apps. They are as follows:
- Govern the identity lifecycle
- Govern access lifecycle
- Secure privileged access for administration
Identity lifecycle
- Identity Governance helps organizations achieve a balance between productivity.
- It is, however, the cornerstone for Identity Governance, and effective governance at scale necessitates the modernization of application identity lifecycle management infrastructure.
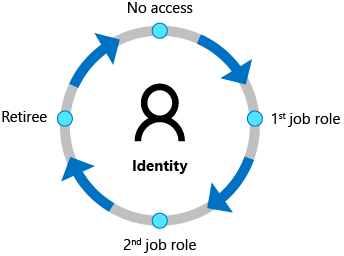
- In many firms, an employee’s identity lifecycle is linked to his or her representation in a human capital management system. In both Active Directory and Azure AD, Azure AD Premium automatically preserves user IDs for users represented in Workday and SuccessFactors.
- This is the same process as outlined in the Azure Active Directory user provisioning planning guidance for cloud HR applications. Microsoft Identity Manager is included in Azure AD Premium for importing records from on-premises HCM systems.
Access lifecycle
- Organizations must have a procedure in place to manage access beyond what was initially granted to a person when their identity was formed.
- Furthermore, corporate organisations must be able to expand effectively in order to continuously create and implement access policies and restrictions.
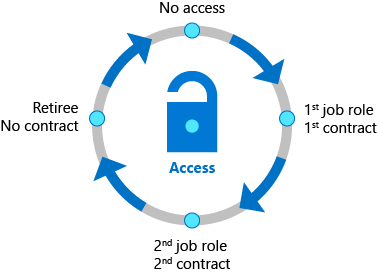
- Typically, IT delegates access approval decisions to business decision-makers.
- Furthermore, IT can involve the users themselves. Moreover, organizations can automate the access lifecycle process through technologies.
- This covers dynamic groups, as well as user provisioning for SaaS apps or programs that are SCIM-integrated. On-premises application access can also be controlled by organizations.
- Recurring Azure AD access reviews may then be used to review these access privileges on a regular basis. You can also determine how users seek access across packages of group and team memberships, application roles, and SharePoint Online roles using Azure AD entitlement management.
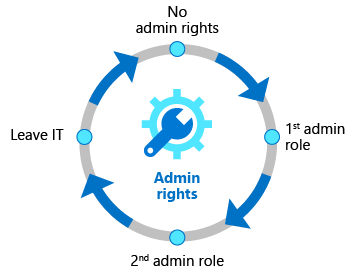
Privileged access lifecycle
- Azure AD Privileged Identity Management (PIM) provides additional controls for securing access rights for resources, across Azure AD, and other Microsoft Online Services.
- In addition to multi-factor authentication and Conditional Access, Azure AD PIM includes a full set of governance controls to help safeguard your company’s resources, including just-in-time access and role change notifications. Furthermore, access reviews may be used to set up regular access recertification for all users with administrator rights.
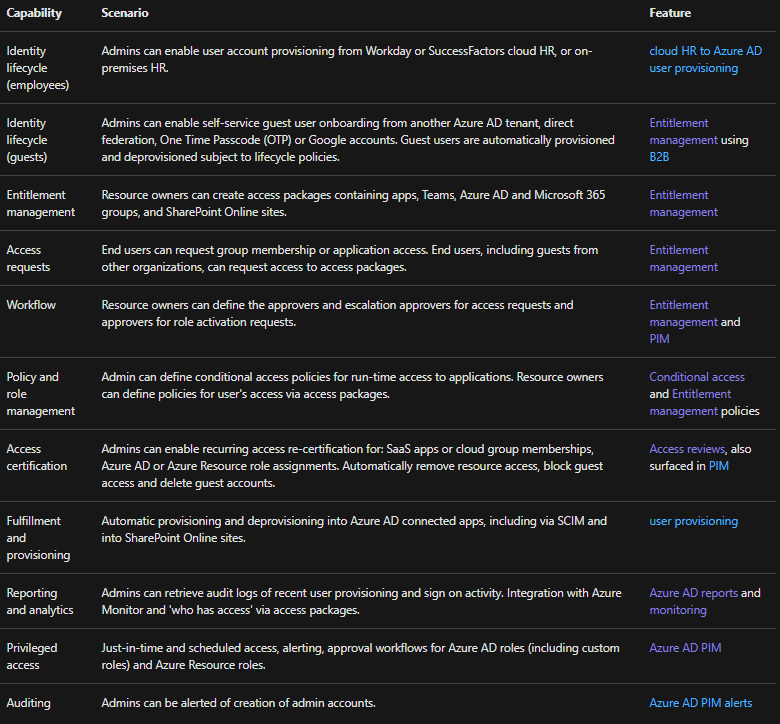
Governance capabilities in other Azure AD features
In addition to the features listed above, additional Azure AD features frequently used to provide identity governance scenarios include:
Reference: Microsoft Documentation


