Methods for hybrid identity solution with Azure AD Connect Health
Exam AZ-304 is retired. AZ-305 replacement is available.
In this, we will discuss the various authentication options that organizations can configure and deploy for supporting access to cloud apps. Moreover, it will also cover password hash synchronization, Pass-through Authentication, and federation and overview of Azure AD connect health.
Azure AD Hybrid Identity Solution
For organizations wanting to move their apps to the cloud, the first goal is to choose the correct authentication method. However, the authentication method is a critical component of an organization’s presence in the cloud. As it controls access to all cloud data and resources. Also, it is the foundation of all the other advanced security and user experience features in Azure Active Directory.
Identity refers to the new control plane of IT security, so authentication is an organization’s access guard to the new cloud world. Moreover, organizations require an identity control plane that strengthens their security and keeps their cloud apps safe from intruders.
Authentication methods
When the Azure Active Directory hybrid identity solution is your new control plane then authentication is the foundation of cloud access. However, choosing the correct authentication method is a crucial first decision in setting up an Azure AD hybrid identity solution. For this, you need to consider the time, existing infrastructure, complexity, and cost of implementing your choice. Azure Active Directory includes authentication methods for hybrid identity solutions such as:
Cloud authentication
After choosing this authentication method, Azure AD handles users’ sign-in process. This includes seamless single sign-on (SSO) in which users can sign in to cloud apps without having to re enter their credentials. There are two options in cloud authentication:
- Firstly, Azure AD password hash synchronization. This enables authentication for on-premises directory objects in Azure Active Directory. Moreover, Users can use the same username and password that they use on-premises without having to deploy any additional infrastructure. Some features of Azure Active Directory such as Identity Protection and Azure AD Domain Services need password hash synchronization.
- Secondly, Azure AD Pass-through Authentication. This provides a simple password validation for Azure AD authentication services by using a software agent running on one or more on-premises servers. In this, the servers validate the users directly with on-premises Active Directory for ensuring that the password validation doesn’t happen in the cloud.
Federated authentication
With this authentication method, Azure Active Directory hands off the authentication process to a separate trusted authentication system. This includes on-premises Active Directory Federation Services (AD FS) for validating the user’s password. However, the authentication system can provide additional advanced authentication requirements.
The following section will help you in deciding which authentication method is right for you by using a decision tree. Moreover, it helps in determining whether to deploy cloud or federated authentication for your Azure AD hybrid identity solution.
Decision tree
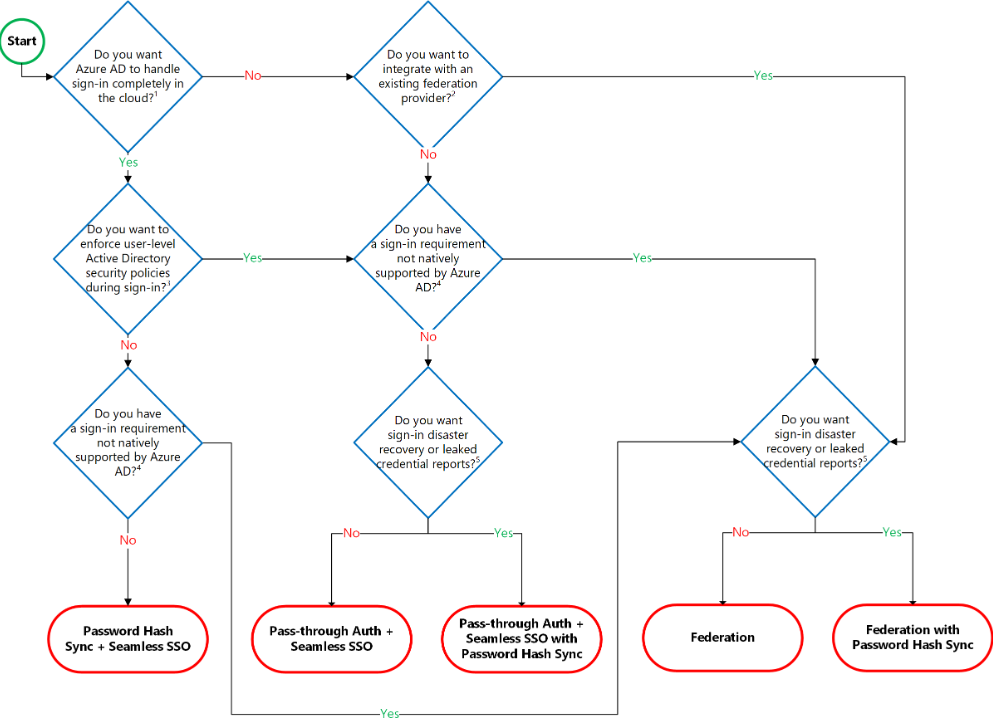
Details on Decision questions:
- Firstly, the Azure Active Directory can handle sign-in for users without relying on on-premises components to verify passwords.
- Secondly, Azure AD can hand off user sign-in to a trusted authentication provider such as Microsoft’s AD FS.
- Thirdly, if you need to apply user-level Active Directory security policies such as account expired, disabled account, password expired, account locked out, and sign-in hours on each user sign-in, Azure AD requires some on-premises components.
- Then, there are Sign-in features not natively supported by Azure AD such as Sign-in using smartcards or certificates, Sign-in using on-premises MFA Server, Sign-in using a third-party authentication solution and Multi-site on-premises authentication solution.
- Lastly, Azure AD Identity Protection requires Password Hash Sync regardless of which sign-in method you choose. This is for providing the Users with leaked credentials.
Cloud authentication: Password hash synchronization
- Firstly, the password hash synchronization requires the least effort regarding deployment, maintenance, and infrastructure. This level of effort applies to organizations that only require their users to sign in to Office 365, SaaS apps, and other Azure AD-based resources.
- Secondly, for improving users’ sign-in experience, it deploys a seamless SSO with password hash synchronization.
- Thirdly, there are advanced scenarios in which organizations choose to use insights from identities with Azure AD Identity Protection reports with Azure AD Premium P2. However, organizations that require multi factor authentication with password hash synchronization must use Azure Multi-Factor Authentication or Conditional Access custom controls.
- Then, there is business continuity in which it uses password hash synchronization with cloud authentication that is highly available as a cloud service that scales to all Microsoft datacenters. However, for making sure password hash synchronization does not go down for extended periods. But, deploys a second Azure AD Connect server in staging mode in a standby configuration.
- Lastly, password hash synchronization doesn’t immediately enforce changes in on-premises account states. In this, a user has access to cloud apps until the user account state is synchronized to Azure AD.
Cloud authentication: Pass-through Authentication
- Firstly, for pass-through authentication, you need one or more lightweight agents installed on existing servers. Also these agents must have access to your on-premises Active Directory Domain Services, including your on-premises AD domain controllers. And, they require outbound access to the Internet and access to your domain controllers.
- Secondly, for improving users’ sign-in experience, it deploys a seamless SSO with Pass-through Authentication. As, Seamless SSO removes unnecessary prompts after users sign in.
- Thirdly, there are advanced scenarios in which Pass-through Authentication enforces the on-premises account policy at the time of sign-in. However, organizations that require multi factor authentication with pass-through authentication must use Azure Multi-Factor Authentication (MFA) or Conditional Access custom controls. Advanced features require that password hash synchronization is deployed whether or not you choose pass-through authentication.
- Then, there is Business continuity for which it is recommended that you should deploy two extra pass-through authentication agents. However, these extras are in addition to the first agent on the Azure AD Connect server. And, there’s another benefit to deploying password hash synchronization in addition to pass-through authentication. That it acts as a backup authentication method when the primary authentication method is no longer available.
- Lastly, you can use password hash synchronization as a backup authentication method for pass-through authentication. This is when the agents can’t validate a user’s credentials due to a significant on-premises failure. However, failover to password hash synchronization doesn’t happen automatically and you must use Azure AD Connect to switch the sign-on method manually.
Monitoring AD FS using Azure AD Connect Health
This is specific for monitoring your AD FS infrastructure with Azure AD Connect Health. For information about monitoring Azure AD Connect (Sync) with Azure AD Connect Health check Azure AD Connect Health for Sync.
Alerts for AD FS
The Azure AD Connect Health Alerts section provides the list of active alerts. However, every alert covers relevant information, resolution steps, and links to related documentation.
Usage Analytics for Active Directory FS
Azure Active Directory Connect Health Usage Analytics is for analyzing the authentication traffic of your federation servers. There you can double-click the usage analytics box for opening the usage analytics blade that shows you several metrics and groupings.
Performance Monitoring for Active Directory FS
Azure AD Connect Health Performance Monitoring gives monitoring information on metrics. However, selecting the Monitoring box opens a new blade with detailed information on the metrics. With selecting the Filter option at the top of the blade, you can filter by the server to see an individual server’s metrics. For changing the metric, right-click on the monitoring chart under the monitoring blade and select Edit Chart (or select the Edit Chart button). From the new blade that opens up, you can select additional metrics from the drop-down and specify a time range for viewing the performance data.
Reference: Microsoft Documentation


