Exploring security reports and dashboards
In this tutorial, we will get a brief about security reports and dashboards.
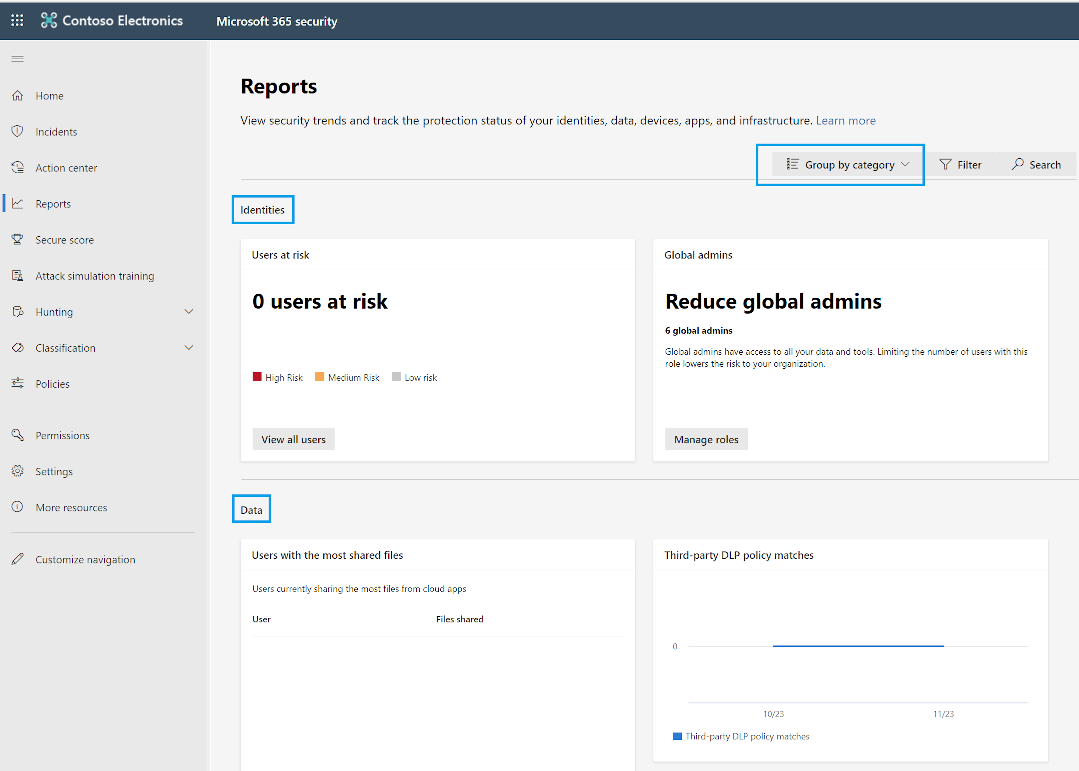
The Microsoft security center includes a Reports section that shows various cards covering different areas. Security analysts and administrators can track the cards as part of their day-to-day operations. On drill-down, cards provide detailed reports and, in some cases, management options. However, by default, cards are groups on the basis of the following categories:
- Firstly, Identities – user accounts and credentials.
- Secondly, Data – email and document contents.
- Then, Devices – computers, mobile phones, and other devices.
- Lastly, Apps – programs and attached online services.
In the example below, the cards are grouped by category. The first category is Identities where you find two cards, Users at risk and Global admins. The second category is Data where you find two cards, Users with the most shared files and Third-party DLP policy matches.
Further, you can group cards by topic, which will rearrange the cards and group them into the following areas:
- Firstly, Risk – cards that highlight entities, such as accounts and devices, that might be at risk.
- Secondly, Detection trends – cards that highlight new threat detections, anomalies, and policy violations.
- Thirdly, Configuration and health – cards that cover the configuration and deployment of security controls, including device onboarding states to management services.
- Lastly, Other – all cards not categorized under other topics.
Reference: Microsoft Documentation


