Configuring Key rotation
In this tutorial, we will learn and understand how to automate the periodic rotation of secrets for databases and services that use two sets of authentication credentials. We’ll talk about how to make account key rotation functions. This tutorial, on the other hand, uses a function called by an Azure Event Grid notification to rotate Azure Storage account keys stored in Azure Key Vault as secrets.
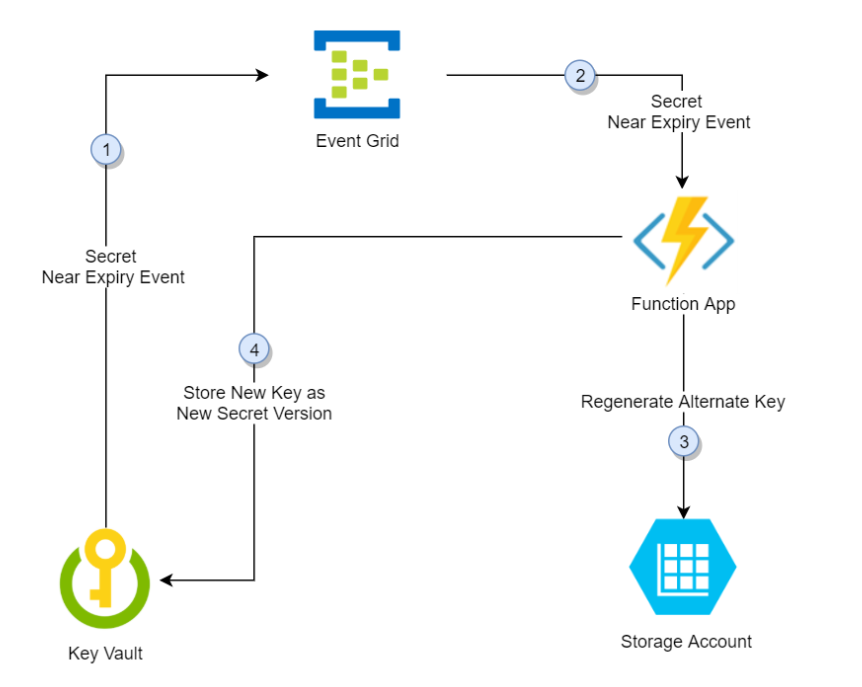
Azure Key Vault saves individual Storage Account access keys as versions of the same secret in the aforementioned approach, switching between primary and secondary keys in future versions. The alternate key is regenerated and added to Key Vault as a new version of the secret since one access key is saved in the latest version of the secret. That method allows apps to refresh to the most recent regenerated key throughout the duration of the rotation cycle.
Prerequisites
- Firstly, must have an Azure subscription.
- Secondly, Azure Key Vault.
- Thirdly, two Azure Storage Accounts
However, if you don’t have existing key vault and storage accounts then:
- Firstly, under the Resource group, select Create new and name the group akvrotation and click Ok.
- Secondly, select Review+Create.
- Thirdly, select Create.
Now, you’ll have a key vault, and two storage accounts. Here, you can verify this setup in the Azure CLI by running the command:
Azure CLI
az resource list -o table -g akvrotation
The output result will be like:
Console
Name ResourceGroup Location Type Status
———————– ——————– ———- ——————————— ——–
akvrotation-kv akvrotation eastus Microsoft.KeyVault/vaults
akvrotationstorage akvrotation eastus Microsoft.Storage/storageAccounts
akvrotationstorage2 akvrotation eastus Microsoft.Storage/storageAccounts
Creating and deploying storage account key rotation function
Next, create a function app with a system-managed identity, in addition to the other required components, and deploy storage account key rotation functions
However, the function app rotation functions require these components and configuration:
- Firstly, an Azure App Service plan
- Then, a storage account required for function app trigger management
- Next, an access policy to access secrets in Key Vault
- Fourthly, assign Storage Account Key Operator Service role to function app to access storage Account access keys
- After that, storage Account key rotation functions with event trigger and http trigger (on-demand rotation)
- Lastly, eventGrid event subscription for SecretNearExpiry event
- Firstly, select the Azure template deployment link.
- Secondly, in the Resource group list, select akvrotation.
- Thirdly, in the Storage Account Name, type the storage account name with access keys to rotate
- Fourthly, in the Key Vault Name, type the key vault name
- Then, in the Function App Name, type the function app name
- Next, in the Secret Name, type secret name where access keys would be stored
- After that, in the Repo Url, type function code GitHub location (https://github.com/jlichwa/KeyVault-Rotation-StorageAccountKey-PowerShell.git)
- Then, select Review+Create.
- Lastly, select Create
After completing the preceding steps, you’ll have a storage account, a server farm, a function app, application insights.
Adding Storage Account access key to Key Vault
- Firstly, set your access policy to grant manage secrets permissions to users:
Azure CLI
az keyvault set-policy –upn <email-address-of-user> –name akvrotation-kv –secret-permissions set delete get list
Now, you can create a new secret with a Storage Account access key as value. However, you will also require the Storage Account resource ID, secret validity period, and the key ID to add to secret. So the rotation function can regenerate keys in the Storage Account.
- Retrieving Storage Account resource ID. Value can be found under id property
Azure CLI
az storage account show -n akvrotationstorage
- Listing the Storage Account access keys to retrieve key values
Azure CLI
az storage account keys list -n akvrotationstorage
- Populating retrieved values for key1Value and storageAccountResourceId
Azure CLI
$tomorrowDate = (get-date).AddDays(+1).ToString(“yyy-MM-ddThh:mm:ssZ”)
az keyvault secret set –name storageKey –vault-name akvrotation-kv –value <key1Value> –tags “CredentialId=key1” “ProviderAddress=<storageAccountResourceId>” “ValidityPeriodDays=60” –expires $tomorrowDate
However, creating a secret with a short expiration date will publish a SecretNearExpiry event within several minutes. Further, this will trigger the function to rotate the secret. Now, you can verify that access keys are regenerated by retrieving and comparing Storage Account keys and Key Vault secrets.
Adding additional Storage Accounts for rotation
Same function app can be reused for rotating multiple Storage Accounts. However, adding additional storage account keys for rotation to existing function requires:
- Assigning Storage Account Key Operator Service role to function app to access Storage Account access keys
- EventGrid event subscription for SecretNearExpiry event
- Firstly, select the Azure template deployment link.
- Secondly, in the Resource group list, select akvrotation.
- Thirdly, in the Storage Account Name, type the storage account name with access keys to rotate
- Fourthly, in the Key Vault Name, type the key vault name
- Then, in the Function App Name, type the function app name
- After that, in the Secret Name, type secret name where access keys would be stored
- Next, select Review+Create.
- Lastly, select Create
Reference: Microsoft Documentation


