Cloud IAM working: Google Professional Data Engineer GCP
In this, we will learn the Cloud IAM working.
Cloud IAM:
- Can manage access control by defining
- who (identity)
- has what access (role)
- for which resource.
- permission to access a resource isn’t granted directly to the end user.
- permissions are grouped into roles
- roles are granted to authenticated members.
- IAM policy defines and enforces what roles are granted to which members
- policy is attached to a resource.
- During attempts to access a resource, Cloud IAM checks the resource’s policy
Permission management in Cloud IAM.
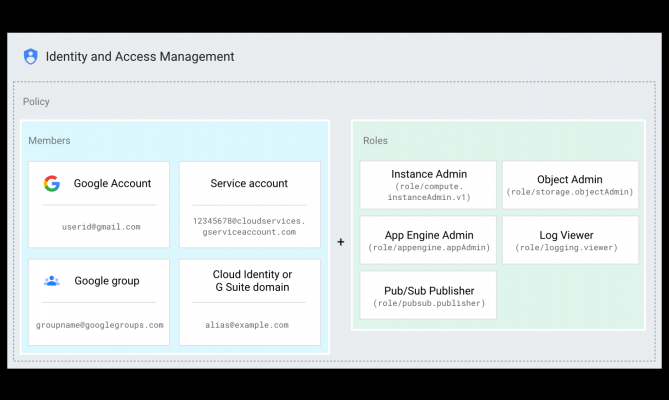
3 parts in figure
-
- can be a Google Account (for end users),
- service account (for apps and virtual machines)
- Google group
- G Suite or Cloud Identity domain that can access a resource.
- Role
- A collection of permissions.
- Permissions determine what operations have access to the resource.
- With role allocation, all permissions with the role are granted
- Policy
- binds one or more members to a role.
- Defines who (member) has what type of access (role) on a resource,
- create a policy and attach it to the resource.
In the above diagram,
- the Cloud IAM policy binds the end user identified by [email protected] to the App Engine Admin role (roles/appengine.appAdmin).
- If the policy is attached to a project, the user [email protected] has the App Engine Admin role within that project.
- the user can view, create, and update all project-level app configurations and settings for App Engine.
Members
Members can be of the following types:
- Google Account
- represents a developer, an administrator, or person who interacts with Google Cloud.
- Any email address that’s associated with a Google Account can be the identity
- Service account
- account for an application.
- Apps runs with role you specify.
- create as many service accounts as necessary
- Google group
- a named collection of Google Accounts and service accounts.
- has a unique email address that’s associate with the group.
- convenient way to apply an access policy to a collection of users.
- can grant and change access controls for a whole group at once
- also easily add or remove members from a Google group instead of updating a Cloud IAM policy.
- They don’t have login credentials
- cannot use Google Groups to establish identity to make a request to access a resource.
- G Suite domain
- represents a virtual group of all the created Google Accounts in an G Suite account.
- G Suite domains represent organization’s internet domain name
- If user add to G Suite domain, a new Google Account is created for the user in it
- It cannot establish identity, but they enable convenient permission management.
- Cloud Identity domain
- like a G Suite domain
- represents a virtual group of all Google Accounts
- users don’t have access to G Suite applications and features.
allAuthenticatedUsers
- a special identifier that represents
- all service accounts
- all users on the internet who have authenticated with a Google Account.
- It accounts that aren’t connected to a G Suite or Cloud Identity domain,
- Users who aren’t authenticated, like anonymous visitors, aren’t included.
allUsers
- a special identifier that represents anyone who is on the internet
- includes authenticated and unauthenticated users.
Google Professional Data Engineer (GCP) Free Practice TestTake a Quiz
