Authorization Approach in Azure App Service
In this article, we will learn about App Service for simplifying authentication and authorization for apps including details about Azure App Service. So, let’s understand it.
Azure App Services
Azure App Service provides built-in authentication and authorization support by using which you can sign in users and access data by:
- Writing less or no code for your web app
- RESTful API
- Mobile back end
- Or with Azure Functions
However, secure authentication and authorization need a deep understanding of security, including federation, encryption, JSON web tokens (JWT) management, grant types, and so on. But, App Service provides these utilities so that you can spend more time and energy on providing business value to your customer.
App Service Working
In App Service the authentication and authorization module runs in the same sandbox as the application code. However, when it’s enabled, every incoming HTTP request passes through it before being handled by your application code.
Below, you can see an architecture diagram showing requests intercepted by a process in the site sandbox interacting with identity providers before allowing traffic to the deployed site.
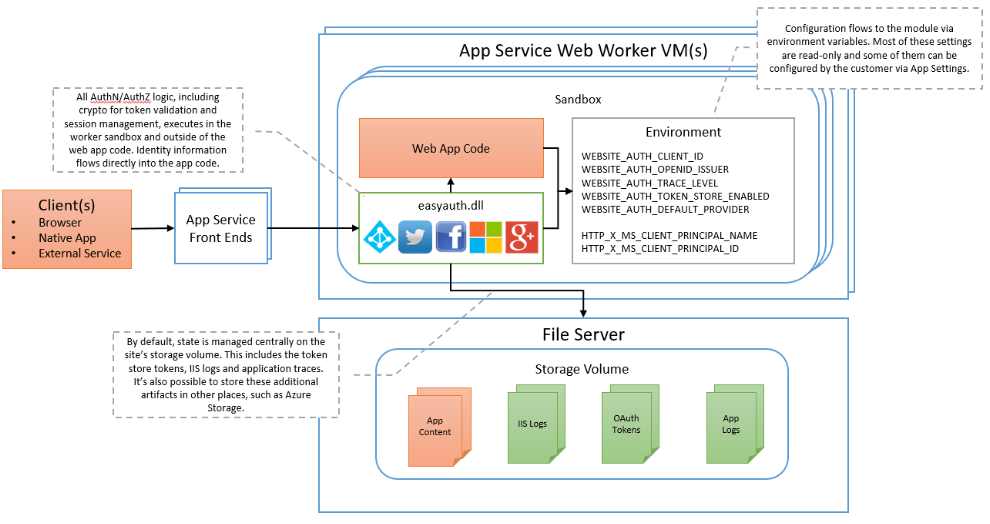
This module controls several things for your app:
- Firstly, authenticating users with the specified provider
- Secondly, validating, storing, and refreshing tokens
- Thirdly, managing the authenticated session
- Lastly, injecting identity information into request headers
Authorization behavior
In the Azure portal, you can configure App Service authorization with a number of behaviors when an incoming request is not authenticated.
The following headings describe the options.
Allow Anonymous requests (no action)
This option delays authorization of unauthenticated traffic to your application code. And, for authenticated requests, App Service passes along the authentication information in the HTTP headers. However, this option provides more flexibility in handling anonymous requests.
Allow only authenticated requests
The option is Log in with <provider>. However, App Service redirects all anonymous requests to /.auth/login/<provider> for the provider you choose. And, if the anonymous request comes from a native mobile app, the returned response is an HTTP 401 Unauthorized. With this option, there is no need of writing any authentication code in your app. As finer authorization, such as role-specific authorization, can be handled by inspecting the user’s claims.
Reference: Microsoft Documentation


