Learn to Implement password hash synchronization
Learn how to implement password hash synchronization with this tutorial. Passwords are stored in the Active Directory domain service as a hash value representation of the actual user password. The outcome of a one-way mathematical function (the hashing algorithm) is a hash value. There is no way to get the plain text form of a password from the result of a one-way function.
Detailed description of how password hash synchronization works
The next section goes over how password hash synchronization between Active Directory and Azure AD works in detail.
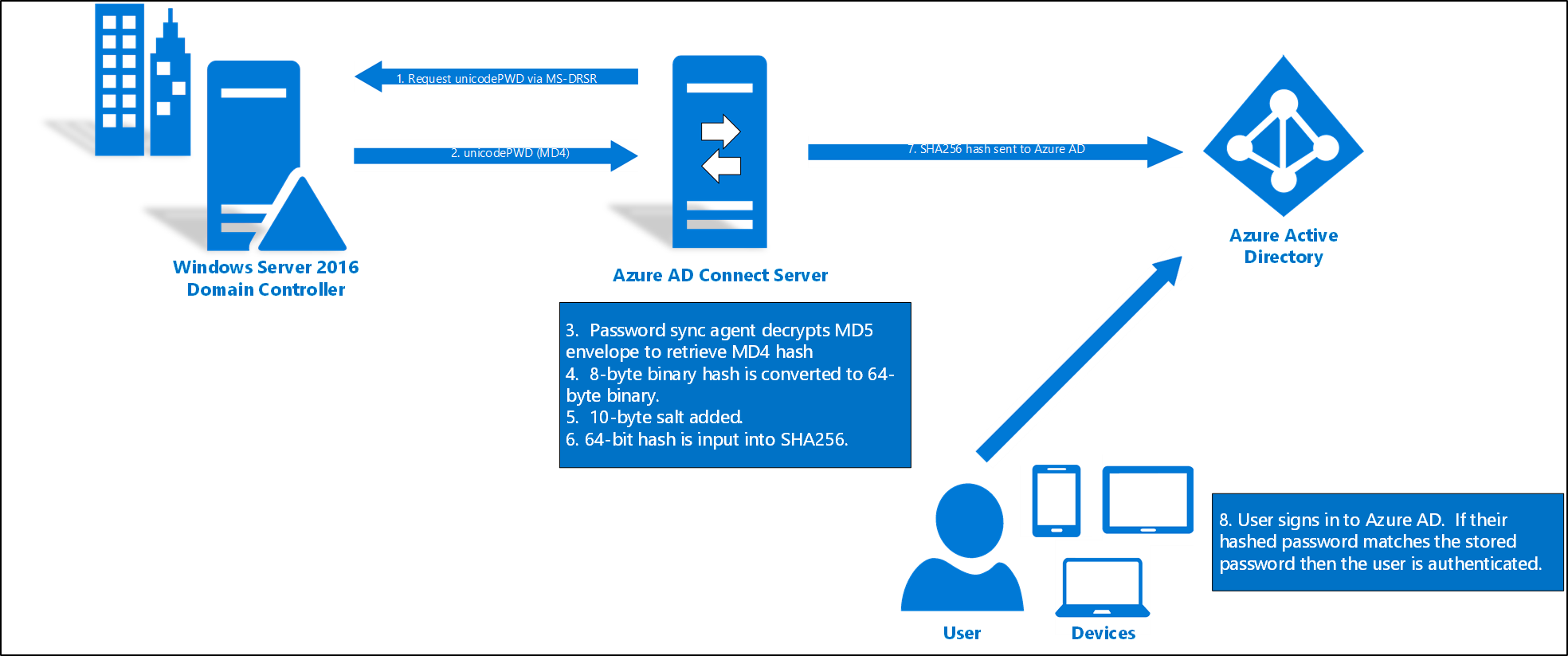
- Every two minutes, the password hash synchronization agent on the AD Connect server requests stored password hashes (the unicodePwd attribute) from a DC. This request is via the standard MS-DRSR replication protocol used to synchronize data between DCs. The service account must have Replicate Directory Changes and Replicate Directory Changes All AD permissions (granted by default on installation) to obtain the password hashes.
- Before sending, the DC encrypts the MD4 password hash by using a key that is a MD5 hash of the RPC session key and a salt. It then sends the result to the password hash synchronization agent over RPC. The DC also passes the salt to the synchronization agent by using the DC replication protocol, so the agent will be able to decrypt the envelope.
Further steps
- After the password hash synchronization agent has the encrypted envelope, it uses MD5CryptoServiceProvider and the salt to generate a key to decrypt the received data back to its original MD4 format. Indeed, The password hash synchronization agent never has access to the clear text password. The password hash synchronization agent’s use of MD5 is strictly for replication protocol compatibility with the DC. It is only used on premises between the DC and the password hash synchronization agent.
- Furthermore, The password hash synchronization agent expands the 16-byte binary password hash to 64 bytes by first converting the hash to a 32-byte hexadecimal string. Then converting this string back into binary with UTF-16 encoding.
- Subsequently, The password hash synchronization agent adds a per user salt, consisting of a 10-byte length salt, to the 64-byte binary to further protect the original hash.
- The password hash synchronization agent then combines the MD4 hash plus the per user salt, and inputs it into the PBKDF2 function. 1000 iterations of the HMAC-SHA256 keyed hashing algorithm are used.
- The password hash synchronization agent takes the resulting 32-byte hash. Concatenates both the per user salt and the number of SHA256 iterations to it (for use by Azure AD), then transmits the string from Azure AD Connect to Azure AD over TLS.
- When a user attempts to sign in to Azure AD and enters their password, the password is run through the same MD4+salt+PBKDF2+HMAC-SHA256 process. If the resulting hash matches the hash stored in Azure AD, the user has entered the correct password and is authenticated.
Security considerations
- The plain-text form of your password is not available to the password hash synchronisation function, Azure AD, or any of the related services when syncing passwords.
- Instead of using the organization’s own Active Directory instance, users are authenticated using Azure AD. The password data in Azure AD is SHA256, which is a hash of the original MD4 hash. It’s more secure than the information in Active Directory.
- Furthermore, because this SHA256 hash is unbreakable. It also can’t be restored to the Active Directory environment of the company. In a pass-the-hash attack, it is presented as a genuine user password.
Password policy considerations
There are two types of password policies that are affected by enabling password hash synchronization:
- Password complexity policy
- Also, Password expiration policy
Password hash synchronization and FIPS
You should learn about the Password hash sync process for Azure AD Domain Services. If your server has been locked down according to Federal Information Processing Standard (FIPS), then MD5 is disabled.
To enable MD5 for password hash synchronization, perform the following steps:
- Go to %programfiles%\Azure AD Sync\Bin.
- Open miiserver.exe.config.
- Go to the configuration/runtime node at the end of the file.
- Add the following node:
<enforceFIPSPolicy enabled="false"/> - Save your changes.
Reference documentation – Implement password hash synchronization with Azure AD Connect sync

