- can record actions taken by users, roles, or AWS services on S3
- maintain log records for auditing and compliance
- Logging can be done by
- S3 Server Access Logging
- AWS CloudTrail logs
- combination of both above
AWS CloudTrail based logging features
- Can be forwarded to other systems (CloudWatch Logs, CloudWatch Events)
- Deliver logs to more than one destination (send to 2 buckets)
- Turn on logs for a subset of objects
- Cross-account log delivery
- Validate the integrity of the log file by usage of hashing or digital signature
- Default/choice of encryption for log files
- Searchable UI for logs
- Provides fields for lock parameters of the objects
- For S3 can select properties for log records
- Management events (first delivery) are free; data events incur a fee, also storage of logs
- Log delivery for data events every 5 mins; management events every 15 mins
- JSON based log format
S3 Server Logs based logging features
- Object and Bucket operations (using Amazon S3 APIs)
- Has fields for
- Object Size
- Total Time
- Turn-Around Time
- HTTP Referrer for log records
- Lifecycle transitions, expirations, restores
- During batch delete operation, keys are logged
- Authentication failures
- Only storage of logs is charged and no extra cost for usage
- Within a few hours logs are delivered
- Log format of log file with space-separated, newline-delimited records
S3 Server Access Logging
- By default, server logging is disabled
- If set to enabled, logs are saved to bucket in same AWS Region as source bucket.
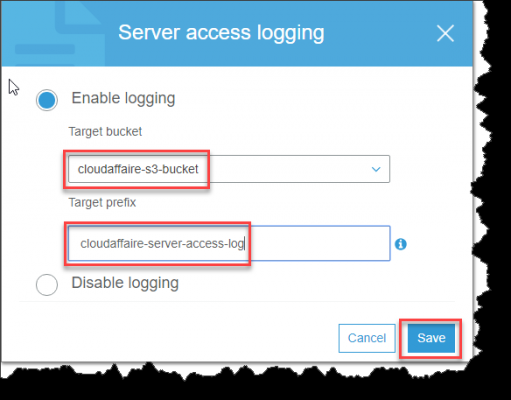
- To enable access logging
- Turn on log delivery by adding logging configuration on bucket for which S3 to deliver access logs or source bucket.
- Grant S3 Log Delivery group write permission on bucket to save access logs to, or target bucket.
- S3 supports permission granting for access logs delivery through bucket ACL only.
- Default bucket encryption on destination bucket can be used if AES256 (SSE-S3) is selected.
- SSE-KMS encryption is not supported.
- log destination bucket cannot have S3 object lock
- Logging configuration information, needed is
- name of the target bucket
- prefix for Amazon S3 to assign to all log object keys (optional)
- Permissions to access generated logs.(optional)
- S3 object key format for log objects – TargetPrefixYYYY-mm-DD-HH-MM-SS-UniqueString where,
- YYYY, mm, DD, HH, MM, and SS are digits of year, month, day, hour, minute, and seconds (respectively) when the log file was delivered as per UTC.
- log records for server access are sent on best effort basis, only.
- No guarantee for completeness and timeliness of server logging and is only best effort basis
- Enabling Logging Using
- the Console
- S3 API
- AWS SDKs
- The log record fields consists of
- Bucket Owner – user ID of owner of source bucket.
- Bucket – name of bucket that the request was processed against.
- Time – time at which request was received;
- Remote IP – IP of requester.
- Requester – user ID of requester
- Request ID – string generated by S3 to uniquely identify each request.
- Operation – Can be declared as
- SOAP.operation
- REST.HTTP_method.resource_type
- WEBSITE.HTTP_method.resource_type
- BATCH.DELETE.OBJECT
- Request-URI
- HTTP status
- Error Code – S3 Error Code
- Bytes Sent
- Object Size
- Total Time – milliseconds request was in flight from server’s perspective.
- Turn-Around Time – milliseconds that S3 spent processing request.
- use Amazon S3 lifecycle configuration
AWS Certified Security - Specialty Free Practice TestTake a Quiz
