Packet Capture
- Refers to intercepting a data packet being communicated at a specific point in data network.
- Capturing done for analysis
- Can be real time
- AWS has following issues for packet capture
- no access to hardware routers and switches
- AWS adds custom headers to data packets during transmission in AWS
- AWS uses custom mapping service and no need for ARP
- In same VPC, intercepting traffic from one endpoint to another is not possible
- VPC Flow Logs do not log some types of IP traffic
- network interface with promiscuous mode in AWS, will not show traffic from other hosts
- EC2 instance can gives root access
- Can be used to install capture software like wireshark
- Capture packets using tcpdump
- A security appliance can also be used to capture traffic and send it to a S3 bucket
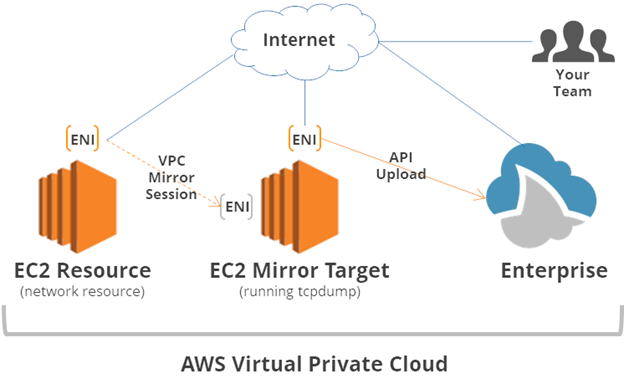
VPC Traffic Mirroring
- AWS feature of VPC to capture and inspect network traffic
- Has benefits of
- Can detect Network & Security Anomalies
- Leverage Operational Insights
- Better implement Compliance
- Troubleshoot Issues
- Have increased network performance
- remove network bottlenecks
- gives direct access to network packets flowing through VPC.
- Can capture all traffic or specific traffic as per filters
- Can also limit number of bytes captured per packet.
- Can capture traffic from VPCs in different AWS accounts and route to central VPC for inspection.
- Elements of VPC Traffic Mirroring
- Mirror Source – source of traffic
- Mirror Target – destination for mirrored traffic. Can be in same or different AWS account
- Mirror
Filter – Rules for traffic to capture. Rules specify
- protocol to capture
- source and destination port ranges
- CIDR blocks for the source and destination
- Rules are numbered, and processed as per order
- Traffic Mirror Session – connection between mirror source and target using a filter.
AWS Certified Security - Specialty Free Practice TestTake a Quiz
