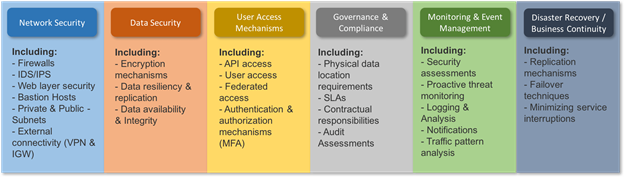
Network and Data Security in AWS
AWS provides several security capabilities and services to increase privacy and control network access. Network firewalls built into Amazon VPC, and web application firewall capabilities in AWS WAF let you create private networks, and control access to instances and applications.
Benefits of AWS Security
- Keep Data Safe – The AWS infrastructure puts strong safeguards in place to help protect customer privacy.
- AWS Compliance – AWS manages dozens of compliance programs in its infrastructure.
- Cost Savings – Maintain the highest standard of security without having to manage own facility.
- Quick Scaling – Security scales with AWS cloud usage.
Server side encryption at rest
- Data is encrypted after being received by the server
- Data is decrypted before being sent
- It is stored in an encrypted form thanks to a key (usually a data key)
- The encryption/decryption keys must be managed somewhere and the server must have access to it
Client side encryption
- Data is encrypted by the client and never decrypted by the server
- Data will be decrypted by a receiving client
- The server should not be able to decrypt the data
- Could leverage Envelope Encryption
- Client library such as the Amazon S3 Encryption Client
- Clients must encrypt data themselves before sending to S3
- Clients must decrypt data themselves when retrieving from S3
- Customer fully manages the keys and encryption cycle
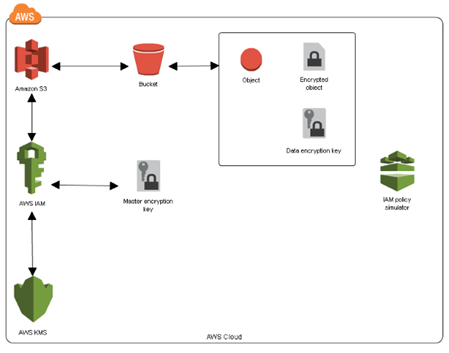
S3 object encryption methods
- SSE-S3: encrypts S3 objects using keys handled & managed by AWS
- SSE-KMS: leverage AWS Key Management Service to manage encryption keys
- SSE-C: when you want to manage own encryption keys
- Client Side Encryption
SSE-S3
- SSE-S3: encryption using keys handled & managed by AWS S3
- Object is encrypted server side
- AES-256 encryption type
- Must set header: x “x- – amz- – server- – side- –
SSE-KMS
- SSE-KMS: encryption using keys handled & managed by KMS
- KMS Advantages: user control + audit trail
- Object is encrypted server side
- Must set header: x “x- – amz- – server- – side- – encryption”: ” aws:kms” “
SSE-C
- SSE-C: server-side encryption using data keys fully managed by the customer outside of AWS
- Amazon S3 does not store the encryption key you provide
- HTTPS must be used
- Encryption key must provided in HTTP headers, for every HTTP request made
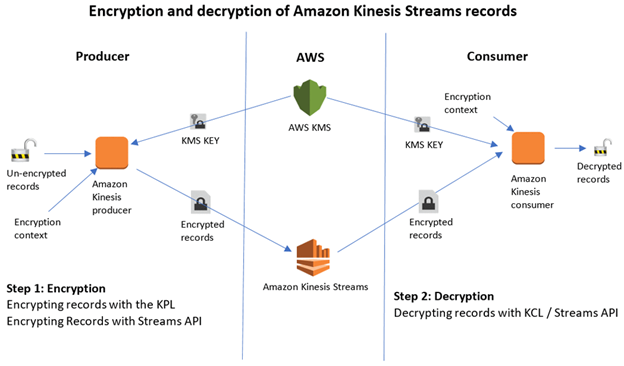
Encryption in transit (SSL)
AWS S3 exposes:
- HTTP endpoint: non encrypted
- HTTPS endpoint: encryption in flight
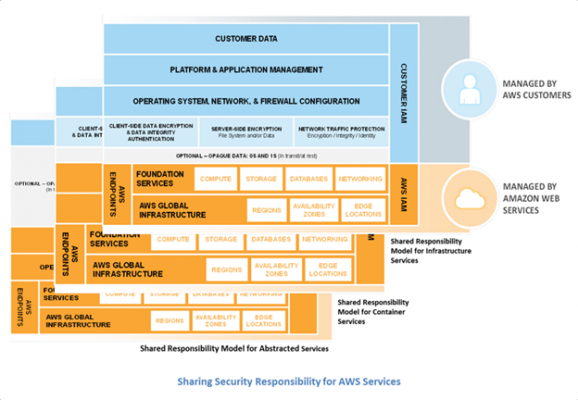
AWS KMS (Key Management Service)
- Anytime you hear “encryption” for an AWS service, it’s most likely KMS
- Easy way to control access to data, AWS manages keys for us
- Fully integrated with IAM for authorization
- Seamlessly integrated into:
- Amazon EBS: encrypt volumes
- Amazon S3: Server side encryption of objects
- Amazon Redshift: encryption of data
- Amazon RDS: encryption of data
- Amazon SSM: Parameter store
- You can also use the CLI / SDK
- KMS can be used to decrypt/encrypt up to 4KB of data.
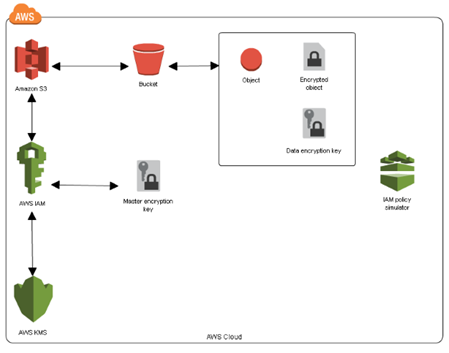
Steps to implement Envelope Encryption
- Create a new CMK, or re-use an existing CMK. This can be done the AWS Console, or with CLI using create-key.
- Use generate-data-key to get a data key.
- This returns the plain text data key, and also an encrypted (with the specified CMK) version of the data key. The encrypted version is referred to as a CipherTextBlob. Store the returned CipherTextBlob (we will need it later). The CipherTextBlob has metadata which tells KMS which CMK was used to generate it. Store this CipherTextBlob.
- Use the plain-text data key to encrypt any amount of data.
- Throw away the plain-text data key, but be sure to store the CipherTextBlob along side the encrypted data.
- To decrypt, use the Decrypt API, sending it the CipherTextBlob from step (3).
- The above step will return the plain text data key (the same one we threw away). Use this key to decrypt the data.
- Throw away the plain-text data key.
- To encrypt more data, repeat steps 6, 7, 8 except use the plain text key to encrypt instead of decrypt.
When to Use KMS
- Use AWS KMS to create and manage master keys (CMKs). You can establish policies that determine who can use CMKs and how they can use them. You can track their use in transaction and audit logs, such as AWS CloudTrail.
- You can use CMKs to encrypt small amounts of data (up to 4096 bytes). However, CMKs are typically used to generate, encrypt, and decrypt the data keys that encrypt data. Unlike CMKs, data keys can encrypt data of any size and format, including streamed data.
When not to use KMS
- AWS KMS does not store or manage data keys, and you cannot use KMS to encrypt or decrypt with data keys. To use data keys to encrypt and decrypt, use the AWS Encryption SDK.
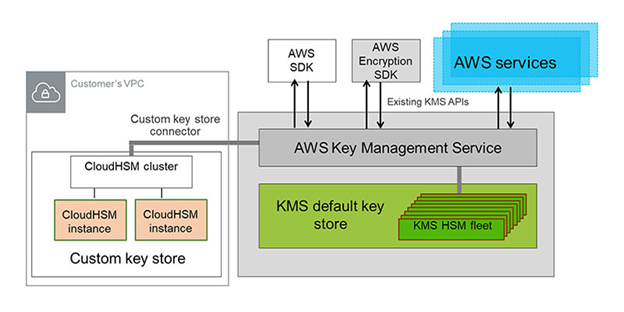
- AWS KMS CMKs are backed by FIPS-validated hardware service modules (HSMs) that KMS manages. To manage own HSMs, use AWS CloudHSM.
- AWS KMS only supports symmetric encryption. If you want to use asymmetric encryption, use AWS CloudHSM.
AWS Certified Solutions Architect Associate Free Practice TestTake a Quiz
