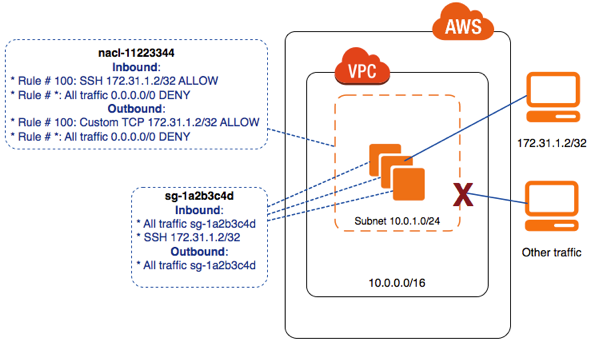
- Default NACLs allow all Inbound / Outbound traffic.
- Custom NACLs by default deny all Inbound / Outbound traffic.
- stateless firewall
- creation of an ACL has a default deny inbound and outbound
- All of the subnets present in a VPC, should have a NACL
- Numbered list of rules that are evaluated in order starting at the lowest numbered rule first to determine what traffic is allowed in or out depending on what subnet is associated with the rule
- The highest rule number is 32766
- Usually the rule number to start is, 100 and then more rules are added accordingly
- Different rules to deny or allow traffic can be applied on either incoming or outgoing traffic
- The default NACL present in VPC allows all traffic both in or out
- Any custom NACL when added, has default setting of denying all the traffic, till specific rules are added
- You must assign a NACL to each subnet, if a subnet is not associated with a NACL, it will allow no traffic in or out
- NACL rules do not maintain any state
- A single NACL can be assigned only to a single subnet
- After association of a NACl with a subnet, all of the past NACLs are deleted
- A single NACL can be assigned to many subnets whereas one subnet can have only one NACL
- Each subnet in VPC must be associated with a NACL. If you don’t explicitly associate a subnet with an ACL, the subnet automatically gets associated with the default ACL
- You can block IP addresses using NACLs not Security Groups
- NACLs contain numbered rules evaluated in the order staring from the lowest one.
- NACLs are stateless. Response to allow inbound traffic is subject to outbound rules.
- Ideally, only ephemeral ports should be allowed in outbound traffic
AWS Certified Security - Specialty Free Practice TestTake a Quiz
