Mitigating DDoS Attacks
- DoS attack is malicious attempt to affect availability of a targeted system, to legitimate end users.
- During the attack, attackers generate large requests to overwhelm target system.
- In DDoS attack, attacker uses multiple sources to generate attack.
- DDoS attacks types, are as OSI being attacked
- Network (layer 3)
- Transport (Layer 4)
- Presentation (Layer 6)
- Application (Layer 7)
DDoS Mitigation
- process of successfully protecting a targeted system from a DDoS attack.
- Uses network equipment or protection service to mitigate incoming threat.
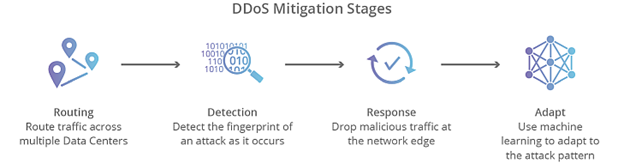
DDoS Mitigation Stages
- Detection – to stop a DDoS distinguish an attack from a high volume of normal traffic.
- Response – System responds to incoming identified threat by intelligently dropping malicious traffic
- Routing – routing traffic, to break remaining traffic into manageable chunks preventing denial-of-service.
- Adaptation – Analyzes traffic for patterns such as repeating offending IP blocks and attacks
AWS Services for DDoS Attack Mitigation
AWS Shield
- A managed DDoS protection service
- Available in Standard and Advanced tiers
- Shield Standard
- applies always-on detection and inline mitigation techniques, like deterministic packet filtering and priority-based traffic shaping
- included automatically to ELB load balancers, CloudFront and Route 53 at no extra cost.
- Use Shield with WAF rules to create a comprehensive DDoS attack mitigation strategy.
- AWS Shield Advanced
- provides enhanced DDoS attack detection and monitoring by – layer traffic to ELB, CloudFront and Route 53
- Uses additional techniques for granular detection of DDoS attackslike detect HTTP floods or DNS query floods.
- includes 24×7 access to AWS DDoS Response Team (DRT)
- Directly create or update AWS WAF rules
- Receive improvements to AWS architectures
- includes access to near real-time metrics and reports
- Combine with WAF metrics for comprehensive CloudWatch monitoring and alarming strategy.
AWS WAF
- It is a web application firewall
- Protects web applications from common web exploits
- define customizable web security rules to control which traffic accesses web applications
- Provided free with AWS Shield Advanced
- can engage the DRT to create WAF rules.
- WAF rules use conditions to
- target specific requests
- trigger an action
- identify and block common DDoS request patterns
Route 53
- A highly available and scalable DNS service
- to route end users to infrastructure running inside or outside of AWS.
- manage traffic globally by routing types
- Gives out-of-the-box shuffle sharding and Anycast routing capabilities
Amazon CloudFront
- distributes traffic across multiple edge locations
- filters requests to ensure that only valid HTTP(S) requests are forwarded to backend hosts
- supports geoblocking, to prevent requests from particular geographic locations.
ELB
- It automatically distributes incoming application traffic across multiple targets
- Targets can be
- Amazon EC2 instances
- Containers
- IP addresses
- multiple AZ
- It minimizes risk of overloading a single resource.
- ELB, like CloudFront, supports valid TCP requests
- UDP and SYN floods are not able to reach EC2 instances.
- Also gives a single point of management
- serves as a line of defense between internet and backend
- ELB includes Application Load Balancer, for HTTP/HTTPS traffic load balancing
- directly supports AWS WAF.
VPCs and Security Groups
- With Amazon VPC can configure
- subnet routes
- public IP addresses
- security groups
- network access control lists
- Can minimize application attack surfaces
- Can configure load balancers and EC2 instance security groups
- Controls traffic from specific IP addresses, from CloudFront or AWS WAF
Best Practices
- Be ready to scale. Scale to meet additional traffic volumes, if valid or a DDoS attack by ELB, CloudFront, Route 53
- Minimize the attack surface area and safeguard exposed resources- decouple infrastructure
- Know what is normal; alert on what is not.
- Architect for resilience
- Deploy Firewalls for Sophisticated Application attacks
For web applications –
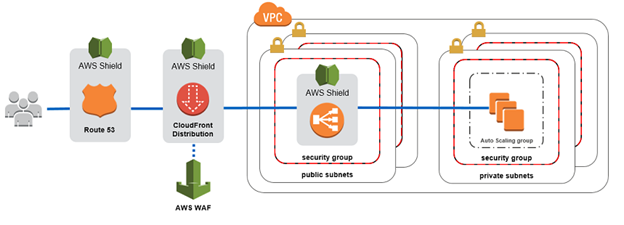
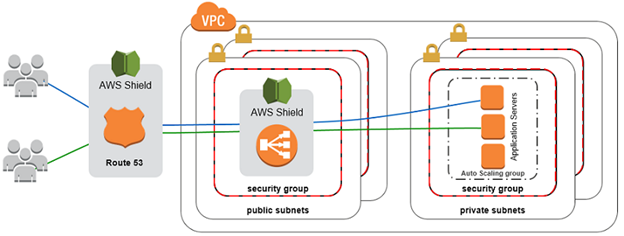
For Load Balanceable Applications
AWS Certified Solutions Architect Associate Free Practice TestTake a Quiz
