Learning Incidence response
- It is an organized approach to address and manage aftermath of a security incident
- Aim to handle situation to limit damage and reduce recovery time and costs.
- Ideally, incident response is done by company’s computer security incident response team (CSIRT),
- CSIRT has professionals from
- IT
- legal
- human resources
- public relations
- CSIRT follows organization’s incident response plan
- Incident response aims to plan ahead and have a flight plan before it is required
Incident Response Process
Steps defined in NIST SP 800-61 as
- Establish response objectives – Goals may include
- containing and mitigating issue
- recovering affected resources
- preserving data for forensics, and attribution
- Respond using the cloud – Have response patterns if event occurs.
- Preserve Evidence – Preserve logs, snapshots, and other evidence by copying to centralized security cloud account. Use tags, metadata, and mechanisms that enforce retention policies.
- Use redeployment mechanisms – Address security anomaly if any
- Automate as applicable– Address repeat incidents by automation
- Select scalable solutions –solution should be scalable as per application
- Learn and improve your process – If gaps are identified, fix them. Simulations help in locating them
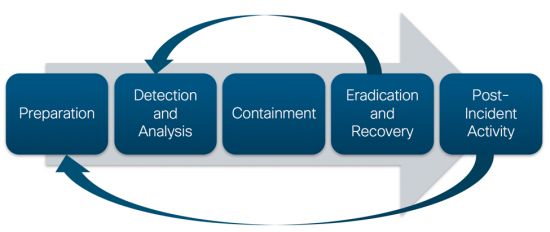
Incident response plan phases
- Prepare users to handle potential incidents
- Identify if event qualifies as a security incident.
- Isolate systems to limit damage by security incidents
- Search for root cause and remove affected systems
- Recover affected systems
- Perform analysis to learn from incident and improve future responses.
Metrics for measuring effectiveness of incident response
- Number of incidents detected.
- Number of incidents missed.
- Number of incidents requiring action.
- Number of repeat incidents.
- The remediation timeframe.
- Number of incidents that led to breaches.
Best practices
- Identify personnel and resources which will help respond to an incident.
- Identify tooling which will help in incidence response
- Develop incident response plans
- Automate containment capability
- Identify forensic capabilities
- Pre-provision access
- Pre-deploy tools
- Simulate incident response
AWS Certified Security - Specialty Free Practice TestTake a Quiz
