Identity Federation
Flow models in federated identity management, are of types
- identity provider initiated model or IdP-initiated
- service provider initiated model or SP-initiated
IdP-initiated
- user access intranet using company’s authentication
- user goes to web page and clicks link to Connections Cloud product like Connections Cloud S2.
- SSO is started and SAML assertion is sent to connections Cloud endpoint via HTTP POST. If valid, access is granted.
- The user interacts with Connections Cloud.
SP-initiated hybrid
- The user visits Connections Cloud login page and clicks Use My Organization’s Login.
- user provides email address linked with his or her account.
- Connections Cloud redirects to organization’s authentication mechanism.
- Rest flow as last step in IdP-initiated model.
AWS SAML
- SAML 2.0 or Security Assertion Markup Language 2.0 is supported by AWS
- SAML is an open standard that many identity providers (IdPs) use.
- Benefit of providing federated single sign-on (SSO)
- SAML validated users can log into the AWS Management Console or call AWS API even if not an IAM user
Use cases supported by IAM federation
- Federated access allows user/application to call AWS API.
- It uses SAML assertion to get temporary credentials.
- Web-based single sign-on (SSO) to AWS Management Console.
Using SAML-Based Federation for API Access to AWS Example to give employees to copy data from their computers to a backup folder.
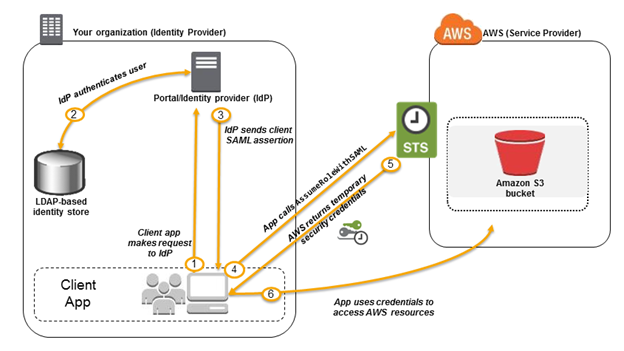
- User request authentication by IdP using a client app
- IdP authenticates the user
- IdP generates a SAML assertion and sends to client app
- client app gives ARN of SAML provider, role to assume by calling AWS STS AssumeRoleWithSAML API
- If valid, API responds with temporary credentials
- Client app uses temporary credentials to call S3 API operations
SAML – Console – AssumeRoleWithSAML
- Corporate user can access Active Directory Federation Services or ADFS
- AD FS authenticates user against Microsoft AD or Active Directory
- SAML Token contains membership generated
- Similar to IdP, Sigin in with SAML Token to AWS Sign-in Endpoint
- AssumeRoleWithSAML send to STS
- STS returns Credentials
- AWS Sign-in endpoint returns Console URL
- Corporate user Redirected to AWS Console
- Benefits include
- Federation proxy not needed
- No IAM permission for federation proxy, needed
AWS Certified Security - Specialty Free Practice TestTake a Quiz
