IAM Roles and Policies
Here, we will learn about IAM Roles and Policies.
Users
- Users refer to individual accounts.
- New users are not given to any AWS services, by default.
- MFA (Multifactor Authentication) can configure for root account.
- IAM provide facility to create and customise password rotation policies in AWS.
- There are two ways to access AWS:
- Username + Password
- Access Key ID + Secret Access Key
- Username and Password
- Cannot interact with API
- custom sign-in link created by IAM console for sign in
Access Key ID and Secret Access Key
- Assigned on user creation only
- Keys also enable interaction by
- the AWS command line
- SDKs
- APIs.
- Keys are not Username or Password.
- User can only view them once.
- They need to regenerate if lost
- Should be stored in a secured location
Groups
- Refer to a collection of IAM users
- It helps to simplify assignment of permissions
- It extensively denote individual departments in a company like Sales, HR, etc,
- Maximum of 10 groups can assign to a user
- Groups cannot have sub-groups as no nesting is permitted
- A group can only have users an no sub-groups
- There is no default group in AWS, for holding all users
- Any renaming of a group name or its path, reflects on policies attach to group, unique ids, users within the group.
- AWS IAM is not responsible to update policies if group list as a resource but it handled manually
- Group deletion involves detaching users and policies from the group and, deletion of inline policies.
- Varied access level for AWS service is needed as
- A user can belong to multiple groups
- Groups cannot belong to other groups
Roles
- Roles are used by any of the following
- AWS IAM user present in same AWS account as role
- Then, AWS IAM user present in different AWS account than role
- AWS offered web service like EC2
- external user that validates using IdP (external identity provider) compliant to SAML 2.0/OpenID Connect
- AWS resources can also assign to roles you create
- Like–EC2 instance having role to access S3, which is without any usernames, passwords, etc.
- Limited to 500 IAM roles under AWS account.
- API Actions for assuming roles:
- AssumeRole
- Can’t call AssumeRole from AWS root account credentials. use credentials for AWS IAM user or IAM role to call AssumeRole.
- AssumeRoleWithSAML –users are validated by SAML authentication response, like an on-premises VPC
- AssumeRoleWithWebIdentity – users are validated by in mobile/web app using a web based identity provider like Facebook/Google
- AssumeRole
Role types:
- AWS Service
- Another AWS Account (allowing entity in other AWS accounts to act in current account)
- Web Identity (Amazon, Cognito, Facebook, Google)
- SAML / OpenID Connect
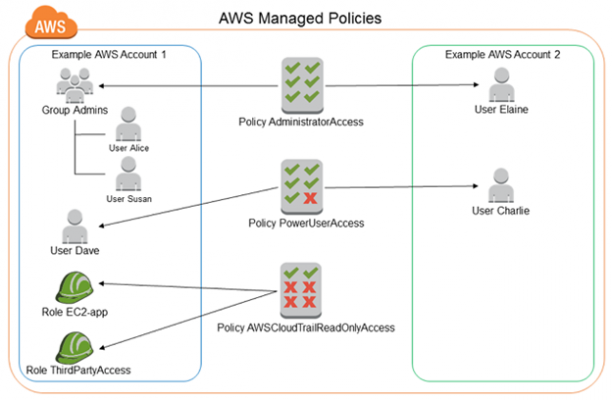
IAM Policies
- Resource property is a must in every IAM Policy
- Policies have 3 main parts – Action, Resource, and Effect
- Effect – refers to result i.e., access is allowed or denied by policy
- Action – Allowed action list, as per policy
- Resource –resource list on which actions can take place as per policy
- Condition (Optional) – Situation under which policy gives permission
- Roles as per their intrinsic capabilities, provide more security against programmatic access
- Multi-Factor Authentication or MFA should enable for all users for more secured access
- Policy Types
- Identity-based policies – It can attach to an IAM identity only like IAM user/ group/ role. To control what actions the assigned identity can perform, further classified as
- Managed policies – It is an standalone identity-based policy which can be attached to multiple users/groups/roles in the AWS account. Further two types, as
- AWS managed policies – creation and management by AWS
- Customer managed policies –creation and management by user by applying a visual editor or editing JSON policy document.
- Managed policies – It is an standalone identity-based policy which can be attached to multiple users/groups/roles in the AWS account. Further two types, as
- Inline policies – User created and embedded into a single user/group/role. Not recommended as management is precarious
- Resource-based policies – Can only be attached to a resource like S3 bucket
- Identity-based policies – It can attach to an IAM identity only like IAM user/ group/ role. To control what actions the assigned identity can perform, further classified as
Policy Example
{
“Version”: “2012-10-17”,
“Statement”: {
“Effect”: “Allow”,
“Action”: “s3:ListBucket”,
“Resource”: “arn:aws:s3:::example_bucket”
}
}
In the above listing, ListBucket Request can perform on example_bucket S3 bucket
Web Identity Federation
- allows trusted third party to authenticate users
- reduces efforts to create and manage users
- removes providing multiple ID to users
- Implements access control by roles
- Providing temporary credential is recommended
- Use External ID provider like Facebook/Google
Standard Web Identity Federation
- Mobile user authenticates with Web Identity provider
- Web Identity provider or WIP, authenticates identity
- Mobile user uses AssumeRole with STS or Security token service
- STS validates from WIP and also gives receives success/failure notification
- Success response checks the Role Trust policy
- Mobile User is provided a temporary access credentials in STS
Cognito
- identity management and sync service
- Supports
- Oauth 2.0
- SAML 2.0
- OpenID Connect
- 2 product streams
- cognito identity pool – is a set of identities
- Types of pools in Cognito
- User pools – user directory in Cognito. to sign in to web or mobile app and directory profile can be accessed by SDK.
- Identity pools – for temporary credentials to access AWS services, good for anonymous guest users
- allows 2 roles to associate one for authenticated user other for unauthenticated users
- It can
- orchestrate generation of unauthenticated identity
- merge unauthaorised identity into authorised identity
- merge multiple entities into one object
- Cognito Authenticated flow types
- Classic or Basic – Login to Web Identity provider rest flow is unauthenticated flow
- Enhanced – every time communicate with Cognito
Cognito Unauthenticated flow:
- A customer starts mobile app which asks for sign in.
- App uses Amazon as web based identity provider
- Cognito API exchange Login with Amazon ID token for a Cognito token.
- Request for temporary credentials requests with Cognito token to STS
- temporary credentials can access AWS resource
AWS Certified Security - Specialty Free Practice TestTake a Quiz
