- Ingress refers to enter in device or property
- Egress refers to leave a device or property.
- Data flows enter network or device by ingress interface and leave by egress interface
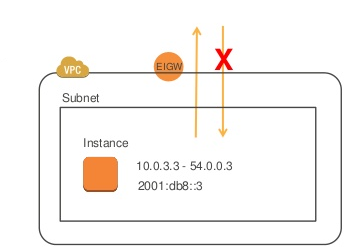
- Egress allows only outbound traffic
- Egress only is needed to
- Risk of internal user communicate with unauthorized external host
- Egress control in AWS VPC can be done by using various capabilities
Subnet-Level Routing Rules
- VPC has subnet route tables
- route tables specify rules to control data traffic flow in or out of VPC
- Every subnet can have different traffic routing rules.
- Bifurcate public-facing EC2 instance needing internet access, during VPC subnet design
- public-facing EC2 instance usually includes
- public load balancers
- proxy servers
- network gateways
- For non public-facing EC2 instance
- should not have internet access
- be in private subnets
- their egress should point to outbound network gateways having routing rules
- usually
includes
- application servers
- database servers
Security Groups
- similar to a virtual firewall for to and fro traffic for VPC
- act on instance level only
- not applicable on subnet
- assign a maximum of five security groups to the instance
- instance in subnet can be assigned different security groups
- default security group for instance is that of the VPC
- specify only allow rules and not deny rules in security group
- They are specified to network interfaces like eth0
- can be changed for the interface
Network ACLs
- ACL is ordered list of rules
- Each rule is numbered
- Highest number in a ACL is 32766
- Every VPC has a default network ACL which can be changed
- The default ACL allow all inbound and outbound IPv4 and IPv6 traffic.
- It is assigned to a subnet
- The default custom ACL denies all traffic
- Every subnet has one ACL
- ACL can be assigned to multiple subnets
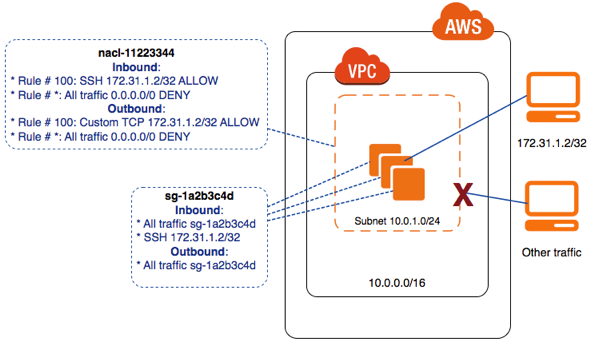
- ACL rule has the form
- Rule number
- Protocol
- CIDR and port number of source and destination
- ALLOW or DENY
- Default ACL has a rule with ‘*’ as number to deny non-matching traffic
- Example below, allows traffic from PC with IP 172.31.1.2/32
VPC Flow Logs
- VPC feature to capture IP traffic moving on a network interface in VPC
- Log data is stored using Cloudwatch Logs
- Flexibility to be created at 3 levels – VPC, Subnet and Network Interface
- Logs can also be configured to stream to other AWS services
- Flow log, tagging is not allowed
- Once created, its configuration cannot be altered
- Few IP traffic is monitored. Is not monitored like DHCP, DNS server, etc.
AWS Certified Security - Specialty Free Practice TestTake a Quiz
