Determine Encryption Requirements or Implementation Technologies
AWS Big Data Exam updated to AWS Certified Data Analytics Specialty.
You can layer three main categories of preventative controls:
- IAM
- Infrastructure security
- Data protection (encryption and tokenization)
Server-side encryption at rest
- Data is encrypted after being received by the server
- Data is decrypted before being sent
- It is stored in an encrypted form thanks to a key (usually a data key)
- The encryption/decryption keys must be managed somewhere and the server must have access to it.
Client-side encryption
- Data is encrypted by the client and never decrypted by the server
- Data will be decrypted by a receiving client
- The server should not be able to decrypt the data
- Could leverage Envelope Encryption
- Client library such as the Amazon S3 Encryption Client
- Clients must encrypt data themselves before sending to S3
- Clients must decrypt data themselves when retrieving from S3
- Customer fully manages the keys and encryption cycle
S3 object encryption methods
- SSE-S3: encrypts S3 objects using keys handled & managed by AWS
- SSE-KMS: leverage AWS Key Management Service to manage encryption keys
- SSE-C: when you want to manage your own encryption keys
- Client-Side Encryption
SSE-S3
- SSE-S3: encryption using keys handled & managed by AWS S3
- Object is encrypted server side
- AES-256 encryption type
- Must set header: x “x- – amz- – server- – side- –
SSE-KMS
- SSE-KMS: encryption using keys handled & managed by KMS
- KMS Advantages: user control + audit trail
- Object is encrypted server-side
- Must set header: x “x- – amz- – server- – side- – encryption”: ” aws:kms” “
SSE-C
- SSE-C: server-side encryption using data keys fully managed by the customer outside of AWS
- Amazon S3 does not store the encryption key you provide
- HTTPS must be used
- Encryption key must provide in HTTP headers, for every HTTP request made
Encryption in transit (SSL)
AWS S3 exposes:
- HTTP endpoint: non encrypted
- HTTPS endpoint: encryption in flight
AWS KMS (Key Management Service)
- Anytime you hear “encryption” for an AWS service, it’s most likely KMS
- Easy way to control access to your data, AWS manages keys for us
- Fully integrated with IAM for authorization
- Seamlessly integrated into:
- Amazon EBS: encrypt volumes
- Amazon S3: Server-side encryption of objects
- Amazon Redshift: encryption of data
- Amazon RDS: encryption of data
- Amazon SSM: Parameter store
- You can also use the CLI / SDK
KMS can be used to decrypt/encrypt up to 4KB of data.
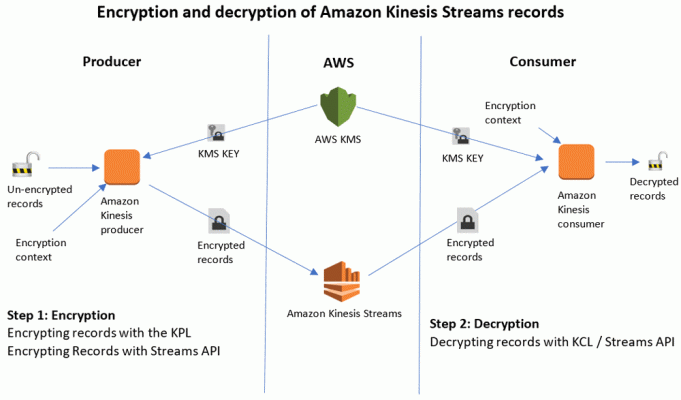
Steps to implement Envelope Encryption
- Create a new CMK, or re-use an existing CMK. This can be done the AWS Console, or with CLI using create-key.
- Use generate-data-key to get a data key.
- This returns the plain text data key, and also an encrypted (with the specified CMK) version of the data key. The encrypted version is referred to as a CipherTextBlob. Store the returned CipherTextBlob (we will need it later). The CipherTextBlob has metadata which tells KMS which CMK was used to generate it. Store this CipherTextBlob.
- Use the plain-text data key to encrypt any amount of data.
- Throw away the plain-text data key, but be sure to store the CipherTextBlob along side the encrypted data.
- To decrypt, use the Decrypt API, sending it the CipherTextBlob from step (3).
- The above step will return the plain text data key (the same one we threw away). Use this key to decrypt the data.
- Throw away the plain-text data key.
- To encrypt more data, repeat steps 6, 7, 8 except use the plain text key to encrypt instead of decrypt.
When to Use KMS
- Use AWS KMS to create and manage master keys (CMKs). You can establish policies that determine who can use your CMKs and how they can use them. You can track their use in transaction and audit logs, such as AWS CloudTrail.
- You can use your CMKs to encrypt small amounts of data (up to 4096 bytes). However, CMKs are typically used to generate, encrypt, and decrypt the data keys that encrypt your data. Unlike CMKs, data keys can encrypt data of any size and format, including streamed data.
When not to use KMS
- AWS KMS does not store or manage data keys, and you cannot use KMS to encrypt or decrypt with data keys. To use data keys to encrypt and decrypt, use the AWS Encryption SDK.
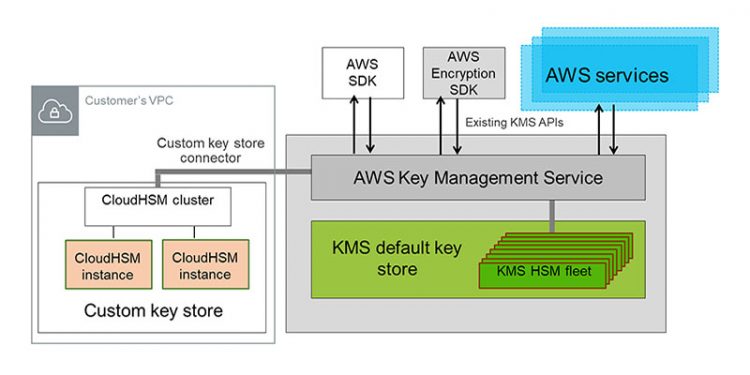
- AWS KMS CMKs are backed by FIPS-validated hardware service modules (HSMs) that KMS manages. To manage your own HSMs, use AWS CloudHSM.
- AWS KMS only supports symmetric encryption. If you want to use asymmetric encryption, use AWS CloudHSM.
AWS CloudHSM
- It is a cloud-based hardware security module (HSM)
- enables you to easily generate and use your own encryption keys on the AWS
- You can manage your own encryption keys
- using FIPS 140-2 Level 3 validated HSMs.
- Integrate with your applications using industry-standard APIs, such as PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries.
- Offload SSL/TLS processing for web servers,
- protect private keys linked to an issuing certificate authority (CA),
- enable Transparent Data Encryption (TDE) for Oracle databases.
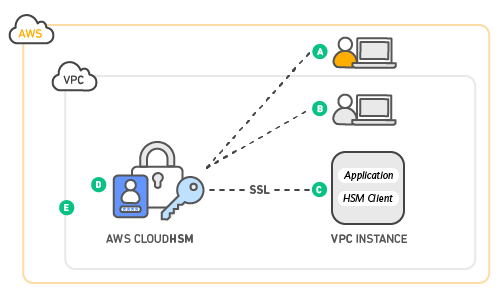
- A: AWS manages the hardware security module (HSM) appliance, but does not have access to your keys
- B: You control and manage your own keys
- C: Application performance improves (due to close proximity with AWS workloads)
- D: Secure key storage in tamper-resistent hardware available in multiple Availability Zones (AZs)
- E: Your HSMs are in your Virtual Private Cloud (VPC) and isolated from other AWS networks.
When to use AWS CloudHSM
- Use AWS CloudHSM when you need to manage the HSMs that generate and store your encryption keys. In AWS CloudHSM, you create and manage HSMs, including creating users and setting their permissions. You also create the symmetric keys and asymmetric key pairs that the HSM stores.
When not to use AWS CloudHSM
- If you need to secure your encryption keys in a service backed by FIPS-validated HSMs, but you do not need to manage the HSM, try AWS Key Management Service.
AWS Encryption SDK
- It is a client-side encryption library
- Makes it easy to encrypt and decrypt data using industry standards
- Enables you to focus on the core functionality of your application, rather than on how to best encrypt and decrypt your data.
- Use the AWS SDK for your preferred programming
language, as
- Java
- Python (Boto)
- JavaScript
- C++,
- The AWS Encryption SDK client library works with the AWS SDKs to support master keys stored in AWS KMS.
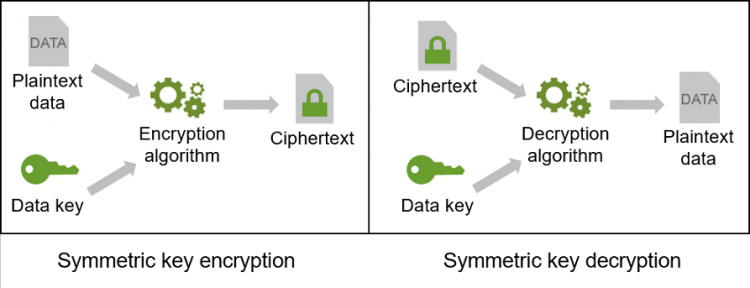
Symmetric Key Encryption
To encrypt data,
- Submits an encryption key, and the plaintext data to an encryption algorithm.
- The encryption algorithm uses those inputs to encrypt the data.
- Then, the AWS Encryption SDK returns an encrypted message that includes
- the encrypted data,
- an encrypted copy of the data key,
- and the encryption context, if you used one.
To decrypt the encrypted message,
Submit the data key and the encrypted message that the SDK returned to a decryption algorithm. The decryption algorithm uses those inputs to return the plaintext data.
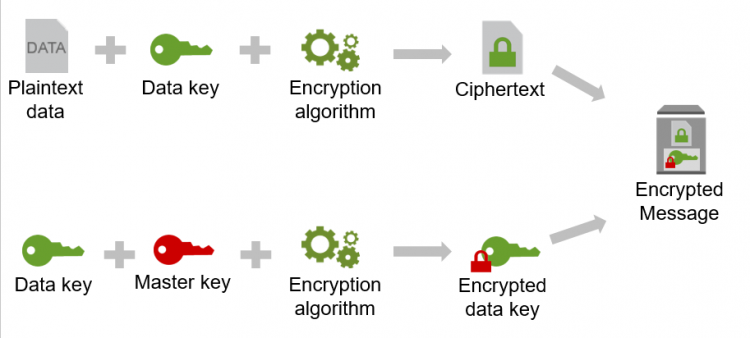
Envelope Encryption
- The AWS Encryption SDK encrypts your data with a data key.
- Then, it encrypts the data key with a master key.
- The AWS Encryption SDK returns the encrypted data and the encrypted data keys in a single encrypted message, as
Encrypting Data
- application passes plaintext data to one of the encryption methods.
- The encryption method asks the cryptographic materials manager (CMM) for encryption materials.
- The CMM is a assembles the data keys, signing keys, and other encryption materials. The AWS Encryption SDK provides a default CMM and a CMM that manages data key caching. You can also create custom CMMs for your applications. When you specify a master key provider or keyring, the AWS Encryption SDK creates a default CMM for you.
- The CMM requests encryption materials from the master key provider or keyring. The response includes a plaintext data key and the same data key encrypted under the master keys. The CMM returns these encryption materials to the encryption method.
- The encryption method uses the plaintext data key to encrypt the data, and then discards the plaintext data key. If you provided an encryption context, the encryption method also cryptographically binds the encryption context to the encrypted data.
- The encryption method returns an encrypted message that contains the encrypted data, the encrypted data key, and other metadata, including the encryption context, if one was used.
Decrypting Data
- Your application passes an encrypted message to a decryption method.
- To indicate the source of the data keys that were used to encrypt your data, your request specifies a cryptographic materials manager (CMM), or a master key provider or keyring. If you specify a master key provider or keyring, the AWS Encryption SDK creates a default CMM for you.
- The decryption method asks the CMM for cryptographic materials to decrypt the encrypted message. It passes in information from the encrypted message, including the encrypted data keys.
- In Java and Python, to get decryption materials, the Default CMM asks its master key provider for a master key that can decrypt one of the encrypted data keys. Other CMMs might use different techniques to get decryption materials. In C and JavaScript, the CMM asks the keyring for decryption materials. The keyring uses its wrapping keys to decrypt one of the encrypted data keys.
- The response includes the decryption materials, including the plaintext data key.
- The decryption method uses the plaintext data key to decrypt the data, then discards the plaintext data key.
- The decryption method returns the plaintext data.
When to use AWS Encryption SDK
- Use the AWS Encryption SDK to encrypt and decrypt data in a script or application. You can use it with AWS Key Management Service or any compatible master key provider.
When not to use AWS Encryption SDK
- Many AWS services optionally encrypt the data that they store and manage for you. (This is known as server-side encryption.) Many of these services are integrated with AWS KMS.
- You might want to use a client-side encryption library that includes special features for your data, such as the Amazon S3 Encryption Client or the DynamoDB Encryption Client.
- When you choose an SDK or encryption client library, remember that libraries are not compatible with one another. That is, you cannot use one library to encrypt data and a different library to decrypt the data. Unless you need a feature provided only by a different library, use the AWS Encryption SDK.
DynamoDB Encryption Client
- It is a software library to protect your table data before you send it to Amazon DynamoDB.
- Encrypting your sensitive data in transit and at rest helps ensure that your plaintext data isn’t available to any third party, including AWS.
- Includes secure implementations that encrypt the attribute values in each table item using a unique encryption key,
- sign the item to protect it against unauthorized changes, such as adding or deleting attributes, or swapping encrypted values.
- use the DynamoDB Encryption Client with encryption keys from any source, as
- custom implementation or a cryptography service,
- AWS Key Management Service (AWS KMS)
- AWS CloudHSM.
- The DynamoDB Encryption Client libraries are developed available in
- Java
- Python
Encrypting Data
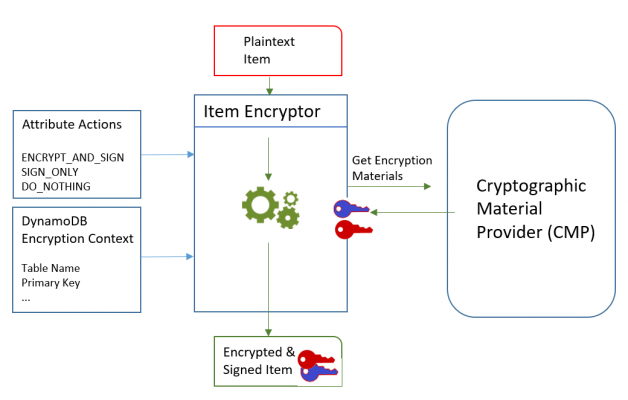
To encrypt, following are needed
- Information about the table. It gets information about the table from a DynamoDB encryption context that you supply. Some helpers get the required information from DynamoDB and create the DynamoDB encryption context for you.
- Which attributes to encrypt and sign. It gets this information from the attribute actions that you supply.
- Encryption materials, including encryption and signing keys. It gets these from a cryptographic materials provider (CMP) that you select and configure.
- Instructions for encrypting and signing the item. The CMP adds instructions for using the encryption materials, including encryption and signing algorithms, to the actual material description.
Decrypting Data
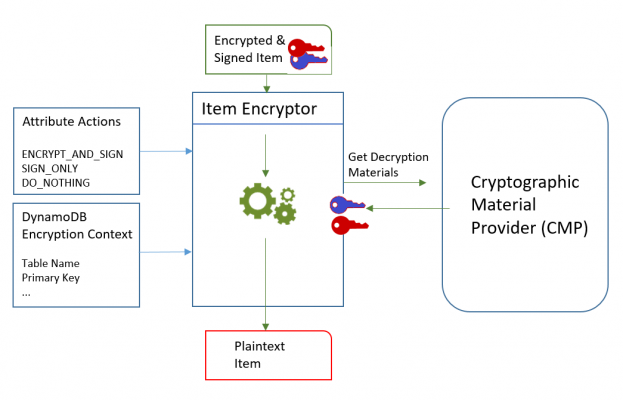
Following are needed to devrypt
- Information about the table from the DynamoDB encryption context.
- Which attributes to encrypt and sign. It gets these from the attribute actions.
- Decryption materials, including verification and decryption keys, from the cryptographic materials provider (CMP) that you select and configure.
- The encrypted item doesn’t include any record of the CMP that was used to encrypt it. You must supply the same CMP, a CMP with the same configuration, or a CMP that is designed to decrypt items.
- Information about how the item was encrypted and signed the item, including the encryption and signing algorithms. The client gets these from the material description attribute in the item.
When to use DynamoDB Encryption Client
- If you need to encrypt and sign DynamoDB table items before you send them to DynamoDB, use the DynamoDB Encryption Client.
- You can also use the DynamoDB Encryption Client to encrypt and sign data that is structured like DynamoDB table items—with attributes and values—even if it is not destined for DynamoDB. The DynamoDB Encryption Client does not require any AWS service.
When not to use DynamoDB Encryption Client
- You can rely on the server-side encryption at rest feature that Amazon DynamoDB provides. DynamoDB transparently encrypts all tables before writing them to disk and transparently decrypts the tables when you get them. Encryption at rest is provided by default, and you cannot disable it. However, if your data security standards require it, you can use both the DynamoDB Encryption Client and encryption at rest on your table data.
- With the DynamoDB Encryption Client, you can specify which attribute values you encrypt and which attributes are included in the item signature. However, if you have unusual data protection requirements that the DynamoDB Encryption Client cannot satisfy, you might be able to use the AWS Encryption SDK to protect your data.
