Delegation & Federation
- Identity Federation – Own IdP – IAM, allow users in other AWS accounts access to resources – Delegation,
- allows users from external IdP – Federation.
Types of Federation
- Corporate/Enterprise Identity Federation (LADP,AD,SAML,AWS Directory Service)
- Web Identity Federation (Amazon, Facebook, Google, Twitter, OpenID Connect) allow app or access to AWS resources.
- ROLES: object which contains 2 policy documents. TRUST Policy (who granted – ARN) ACCESS policy (what entity – Action)
- SESSIONS: set of temporary credentials; access and secret key with expiration; obtained by STS;
- Service Delegation – EC2 or Lambda auto refresh the session which auto refreshes temp credentials managed on behalf.
Console Multi-Account Access:
- Login to Prod account -> authenticate with access keys -> STS Service -> STS:AssumeRole -> Temp Credentials -> Dev Account
- Login to Dev account -> Create IAM role -> TrustProductionUsersFullAdmin -> Role for Cross account access -> between AWS accounts ->
- Prod account AWS Account ID -> Attach Policy -> Create Role
- Login to Prod Account -> Switch Role -> Account Name, Role, Display Name, Color
Delegate Access Across AWS Accounts Using IAM Roles
- share resources in one account with users in a different account.
- With cross-account access, don’t create individual IAM users in each account.
- users don’t have to sign out of one account and sign into another to access resources in different AWS accounts.
This workflow has three basic steps.
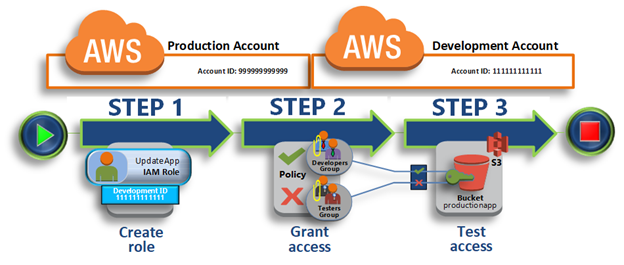
Step 1 – Create a Role
Step 2 – Grant Access to the Role
Step 3 – Test Access by Switching Roles
Federation
The creation of a trust relationship between an external identity provider and AWS. Users can sign in to a web identity provider, such as Login with Amazon, Facebook, Google, or any IdP that is compatible with OpenID Connect (OIDC). Users can also sign in to an enterprise identity system that is compatible with Security Assertion Markup Language (SAML) 2.0, such as Microsoft Active Directory Federation Services. When you use OIDC and SAML 2.0 to configure a trust relationship between these external identity providers and AWS, the user is assigned to an IAM role. The user also receives temporary credentials that allow the user to access AWS resources.
