Data in Transit Security
- TLS encryption in transit across all services.
- For security
- put database in an Amazon Virtual Private Cloud (Amazon VPC)
- using Secure Sockets Layer (SSL) for data in transit
- Use Transport Layer Security 1.2 (earlier Secure Sockets Layer – SSL) with AES-256 cipher.
- Web traffic should use Secure Sockets Layer SSL, using TLS.
- Application data should be encrypted using application level encryption
- Connection between database and application also be encrypted
- Apply network level encryption like IPSec or SSH tunneling as applicable
- Encryption should also be applied when transmitting between protected subnets
- VPC with NACLs can be used for data in transit security by restricting traffic flow
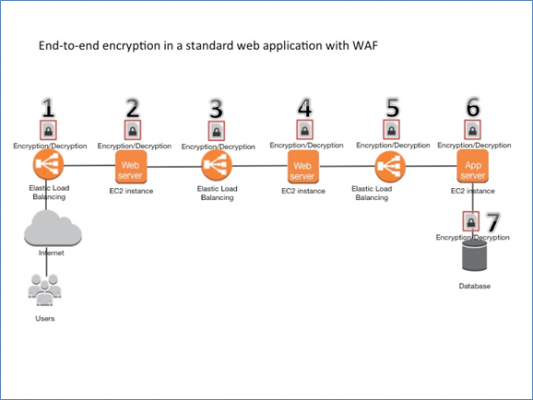
- Using WAF also adds application level security, encryption and decryption.
Point to consider
- Limit the count and usage of public subnets
- Use NAT public subnet for routing egress traffic to Internet
- Deploy hosts in private subnets
- Check source and destination at instance level.
- Apply security groups and NACLs for traffic control
- Use AWS KMS or implement custom key and certificate management
- configure security group to allow HTTPS protocol
- Configure HTTPS with CloudFront
- Apply only VPN for external connectivity:
- Enable only HTTPS listener to application load balancers
- Use HTTPS encryption on instances.
- Apply only SSL/TLS connection to database instances.
- Configure secure protocols for AWS services
AWS Certified Security - Specialty Free Practice TestTake a Quiz
