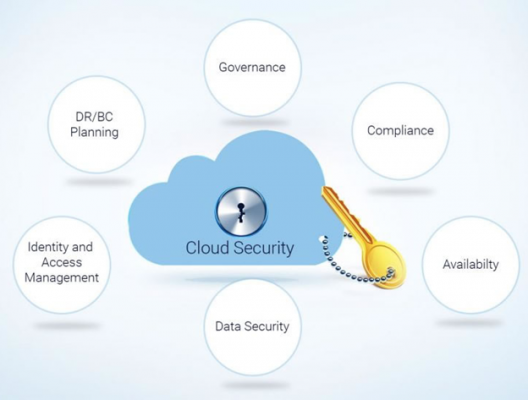
Cloud Security
- It is a part of information security.
- It refer to technologies, policies and controls used to protect data, applications and other resources in a cloud computing environment
- Many security issues. major threats and security
issues are
- Abuse and Nefarious Use of Cloud Computing
- Insecure Application Programming Interfaces
- Malicious Insiders
- Shared Technology Vulnerabilities
- Data Loss/Leakage
- Account, Service & Traffic Hijacking
- Unknown Risk Profile
- Identity management is main challenge and
components are
- Directory Services repositories – to store and manage accounts, identity information, and security credentials.
- Access Management – process of authenticating credentials and controlling access to networked resources based on trust and identity.
- Identity Life Cycle Management – processes used to create and delete accounts, manage account and entitlement changes, and track policy compliance.
- A security policy is organization wide and represents a statement of security goals.
- Security policy lifecycle involves
- Assess risk from business context
- Develop security policies
- Implement security policies
- Manage security policies
- Audit security policies
AWS and Cloud Security
AWS gives highest priority to cloud security so that, AWS maintains a secure environment so that users can easily scale their applications and computing infrastructure.
Few AWS tools are as
- Identity and Access Management or IAM – Create users, groups, and roles, and use permissions to allow and deny their access to AWS resources such as EC2, RDS, and VPC. With IAM, unique credentials can be given to every user so that they can access only allocated AWS services and resources.
- It is also compatible with Active Directory.
- Virtual Private Clouds (VPCs) – It enables provisioning of compute resources, like EC2 instances and RDS, in isolated virtual networks with total control of inbound and outbound network traffic.
- Security Group and NACLs – Use it to implement firewall rules to control network traffic, both incoming and outgoing. Control traffic as per type of protocol (TCP, UDP, ICMP), IP address, and port.
- Data Encryption – It is made available for EBS, S3, RDS and Glacier service. It encrypts data using AES-256.
- Direct Connect – Creates a virtual private interface amongst the on-premise network and the VPC.
AWS Cloud Trail – It gives a log of API calls made against account resources, include those by the AWS Management Console, SDKs, and command line tools.
AWS Certified Security - Specialty Free Practice TestTake a Quiz
