- It is a cloud-based hardware security module (HSM)
- Customer can use own encryption keys
- It uses FIPS 140-2 Level 3 validated HSMs only.
- Has the option for integration with applications by standard APIs like
- PKCS#11
- Java Cryptography Extensions or JCE
- Microsoft CryptoNG or CNG
- Results in offloading of SSL/TLS processing for web servers,
- Secures private keys linked to an issuing certificate authority (CA),
- Can also enable Transparent Data Encryption or TDE for Oracle databases.
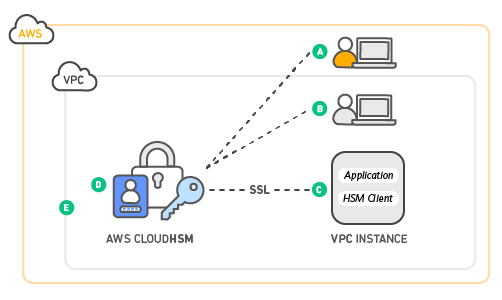
In above diagram,
- A – AWS managing HSM appliance, but no access to keys
- B – Customer controls and manages own keys
- C – Application has improved performance as closer to AWS workloads in AWS instance
- D – key are stored securely in tamper-resistant hardware present in different AZ
- E – HSMs in VPC which is isolated from other AWS networks.
When to use AWS CloudHSM
- Use to manage HSMs in AWS
- Create users and check permissions using HSMs, in AWS
- Create both symmetric and asymmetric key pairs for HSMs
AWS Certified Security - Specialty Free Practice TestTake a Quiz
