Concept of AWS Security
We will now learn the concept of AWS Security and define AWS Cloud Security and Compliance Concepts
Cloud security at AWS is the highest priority. AWS cloud allows customers to scale and innovate while maintaining a secure environment.
AWS Cloud Security and Compliance covers the following aspects of AWS Security
- Infrastructure Security
- Infrastructure Resilience
- Data Encryption
- Monitoring and Logging
- Identity and Access Control
- Compliance Assurance Programs
- Security Support
- Standards and Best Practices
Infrastructure Security
- Network firewalls built into Amazon VPC.
- TLS encryption in transit across all services.
- Private or dedicated connections into the data centre
Amazon VPC
Amazon Virtual Private Cloud (Amazon VPC)
- enables you to launch AWS resources into a virtual network that you’ve defined.
- It resembles a traditional network in data centers
- Benefits of using the scalable infrastructure of AWS.
- Logically isolated from other virtual networks in AWS Cloud.
- Launch AWS resources, like EC2 instances, into VPC.
- Use a public subnet for resources that must be connected to the internet
- Use a private subnet for resources that won’t be connected to the internet.
- You can specify
- an IP address range
- add subnets
- associate security groups
- configure route tables.
Accessing the Internet
- Default VPC includes an internet gateway, and each default subnet is a public subnet.
- Each instance that you launch into a default subnet has a private IPv4 address and a public IPv4 address.
- These instances can communicate with the internet through an internet gateway.
An internet gateway connects to the internet through Amazon EC2 network edge.
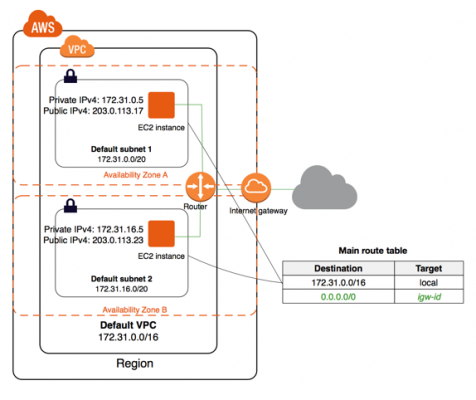
- By default, each instance launched into a nondefault subnet has a private IPv4 address, but no public IPv4 address, unless assigned or modify subnet’s public IP address attribute.
- These instances can communicate with each other, but can’t access the internet.
- It can enable internet access for a nondefault subnet by attaching an internet gateway to its VPC and associating an Elastic IP address with the instance.
- Amazon VPC provides a web-based user interface, Amazon VPC console.
- Access Amazon VPC console by signing in to AWS Management Console and choosing VPC.
Infrastructure Resilience
- Technologies built from ground up for resilience in face of DDoS attacks.
- Services can be used in combination to automatically scale for traffic load.
- Autoscaling, CloudFront, Route 53 can be used to prevent DDoS.
AWS Shield
- It is a managed DDoS protection service
- Available in two tiers: Standard and Advanced.
- AWS Shield Standard applies always-on detection and inline mitigation techniques like deterministic packet filtering and priority-based traffic shaping. It is included automatically and transparently to Elastic Load Balancing load balancers, Amazon CloudFront distributions, and Amazon Route 53 resources at no additional cost.
- AWS Shield Advanced includes access to near real-time metrics and reports, for extensive visibility into infrastructure layer and application layer DDoS attacks.
AWS WAF
- It is a web application firewall to protect web applications from common web exploits.
- It defines customizable web security rules to control which traffic accesses web applications.
- Rules use conditions to target specific requests and trigger an action,
- It helps you to identify and block common DDoS request patterns and effectively mitigate a DDoS attack.
Amazon Route 53
- It is a highly available and scalable DNS service
- Designed to route end users to infrastructure running inside or outside of AWS.
- It can manage traffic globally through a variety of routing types and provides out-of-the-box shuffle sharding and Anycast routing capabilities to protect domain names from DNS-based DDoS attacks.
Amazon CloudFront
- Distributes traffic across multiple edge locations
- Filters requests to ensure that only valid HTTP(S) requests will be forwarded to backend hosts.
- Supports geoblocking, to prevent requests from particular geographic locations.
Elastic Load Balancing
- Distributes incoming application traffic across multiple targets like, such as Amazon Elastic Compute Cloud (Amazon EC2) instances, containers, and IP addresses, and multiple Availability Zones, to minimizes overloading a single resource.
- Elastic Load Balancing, like CloudFront, only supports valid TCP requests, so DDoS attacks such as UDP and SYN floods are not able to reach EC2 instances.
- It is a single point of management
- It can serve as a line of defense between the internet and private EC2 instances.
- It includes Application Load Balancer, for load balancing of HTTP and HTTPS traffic and also directly supports AWS WAF.
VPCs and Security Groups
Security groups or origin access identity (OAI), require attackers to make requests through AWS WAF and CloudFront instead from website origin and minimizes the attack surface of
- backend load balancers
- EC2 instances
- Amazon Simple Storage Service (Amazon S3) buckets
Amazon Virtual Private Cloud (Amazon VPC) allows configuring
- subnet routes
- public IP addresses
- security groups
- network access control lists
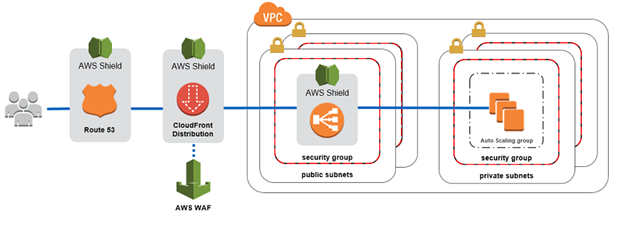
Above, uses Route 53, AWS WAF, CloudFront, and Elastic Load Balancing to control and distribute traffic.
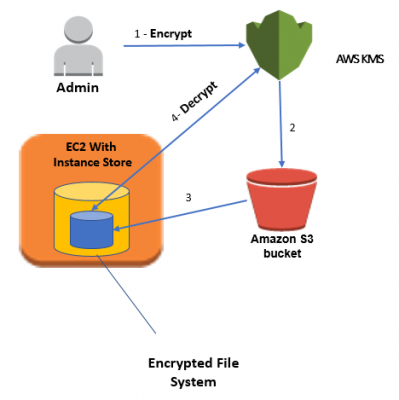
In the above diagram:
- administrator encrypts a secret password by using KMS. an encrypted password is stored in a file.
- administrator puts files containing the encrypted passwords in an S3 bucket.
- At instance boot time, instance copies encrypted files to an internal disk.
- EC2 instance then decrypts the file using KMS and retrieves plaintext password. password is used to configure the Linux encrypted file system with LUKS. All data written to the encrypted file system is encrypted by using an AES-256 encryption algorithm when stored on disk.
Standards and Best Practices
- A security assessment service, Amazon Inspector, that automatically assesses applications for vulnerabilities or deviations from best practices, including impacted networks, OS, and attached storage
- Deployment tools to manage the creation and decommissioning of AWS resources according to organization standards
- Inventory and configuration management tools, including AWS Config, that identify AWS resources and then track and manage changes to those resources over time
- Template definition and management tools, including AWS CloudFormation to create the standard, preconfigured environments
Amazon Inspector
- It is an automated security assessment service
- Improve the security and compliance of applications deployed on AWS.
- Automatically assesses applications for exposure, vulnerabilities, and deviations from best practices. After an assessment, it produces a detailed list of security findings prioritized by level of severity.
AWS Config
- It provides a detailed view of resources associated with AWS account,
- It includes
- how resources are configured
- how they are related to one another
- how configurations and their relationships have changed over time
- It continuously monitors and records AWS resource configurations
- You can automate the evaluation of recorded configurations against desired configurations.
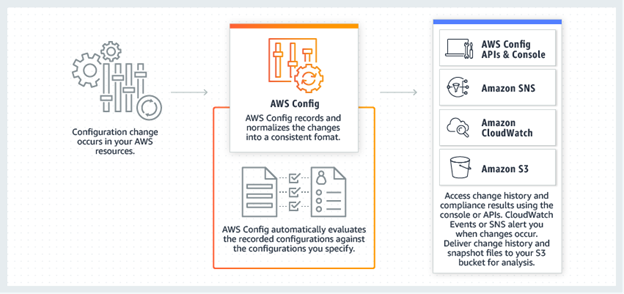
Monitoring and Logging
- Deep visibility into API calls through AWS CloudTrail, including who, what, who, and from where calls were made
- Log aggregation options, streamlining investigations and compliance reporting
- Alert notifications through Amazon CloudWatch when specific events occur or thresholds are exceeded
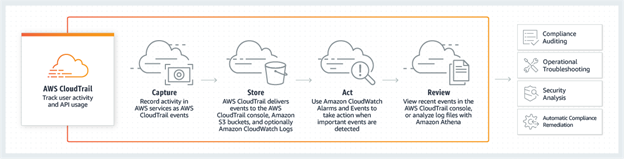
AWS CloudTrail
- It helps you enable governance, compliance, and operational and risk auditing.
- Actions taken by a user, role, or an AWS service are recorded as events in CloudTrail.
- Events include actions taken in AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs.
- CloudTrail is enabled on the AWS account when you create it.
Identity and Access Control
- AWS Identity and Access Management (IAM) lets you define individual user accounts with permissions across AWS resources
- AWS Multi-Factor Authentication for privileged accounts, including options for hardware-based authenticators
- AWS Directory Service allows you to integrate and federate with corporate directories to reduce administrative overhead and improve end-user experience
AWS Multi-Factor Authentication
- With MFA, when a user signs in to an AWS website, they will be prompted for
- their user name and password (first factor—what they know)
- an authentication response from their AWS MFA device (second factor—what they have)
- Multiple factors provide increased security for AWS account settings and resources.
- Enable MFA for the AWS account and for individual IAM users created under account.
- MFA can be also be used to control access to AWS service APIs.
Supported MFA mechanism other than, regular sign-in credentials, are
- Virtual MFA devices. A software app that runs on a phone or other mobile device and emulates a physical device. the device generates a six-digit numeric code based upon a time-synchronized one-time password algorithm. Users must type a valid code from the device on a second webpage during sign-in. Each virtual MFA device assigned to a user must be unique. A user cannot type a code from another user’s virtual MFA device to authenticate.
- U2F security key. A device that you plug into a USB port on the computer. U2F is an open authentication standard hosted by FIDO Alliance. When you enable a U2F security key, you sign in by entering credentials and then tapping the device instead of manually entering a code.
- Hardware MFA device. A hardware device that generates a six-digit numeric code based upon a time-synchronized one-time password algorithm. Users must type a valid code from the device on a second webpage during sign-in. Each MFA device assigned to a user must be unique. A user cannot type a code from another user’s device to be authenticated.
- SMS text message-based MFA. A type of MFA in which IAM user settings include the phone number of the user’s SMS-compatible mobile device. When the user signs in, AWS sends a six-digit numeric code by SMS text message to the user’s mobile device. user is required to type that code on a second webpage during sign-in. Note that SMS-based MFA is available only for IAM users. You cannot use this type of MFA with the AWS account root user.
Security Support
- Real-time insight through AWS Trusted Advisor
- Proactive support and advocacy with a Technical Account Manager (TAM)
Boost your chances to qualify AWS Certified Solutions Architect Associate with hundreds of practice tests. Upgrade your profile Now!
