AWS Hypervisor Security
Here, we will learn about AWS Hypervisor Security.
- Virtual machines or guests run on top of hypervisor.
- Hypervisor or virtual machine monitor,
- is a shrunk down operating system
- layer between physical system resources and virtual machines
- manages and allocates system resources like CPU, memory
- 2
types
- type 1 – runs directly on physical hardware or is bare metal hypervisor
- type 2 – runs on top of an existing operating system
- Amazon uses custom version of hypervisor
CPU privilege modes
- CPU provides 3 privilege modes
- Modes are numbered as 0-3
- Also called as rings
- Ring 0 is most privileged
- Ring 3 is least privileged
- The host OS executes in Ring 0.
- The guest Operating system is present lesser-privileged Ring 1
- applications in the least privileged Ring 3
- It is a clear separation between guest and hypervisor
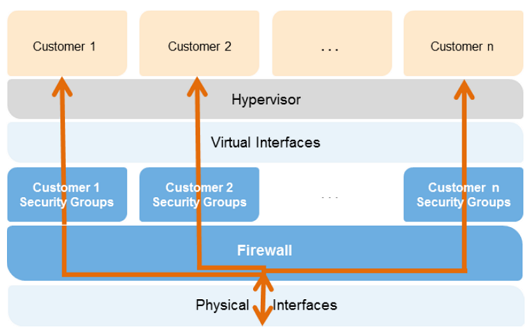
Instance Isolation
- Instances running on same machine can isolate from each other
- The Xen hypervisor used by Amazon, implements this feature
- Also, AWS firewall is present in hypervisor layer
- between physical network interface and instance’s virtual interface
- All packets pass through this layer
- An instance’s neighbors has no access to neighboring running instance
- Physical RAM is also separated amongst instances
- Instances have access to virtualized disks only and not raw disk
- AWS automatically resets every block of storage used by instance
- Memory allocated to guests is scrubbed (set to zero) before reusing it.
Host Operating System
- Users can use multi- factor authentication to restrict access to administration hosts
- Access is also logged and audited
- file system on top of the virtualized disk device, can be encrypted
Guest Operating System
- Virtual instances are controlled by users
- AWS does not have any access rights to instances or the guest OS.
- Various security practices are recommended as
- Disabling password-only access to guests
- Using multi-factor authentication
- Using SSH
- Implementing privilege escalation mechanism
- Enabling logging on a per-user basis
- Amazon-provided AMIs regularly update with the latest patches.
AWS Certified Security - Specialty Free Practice TestTake a Quiz
