Automated AWS Incidence response
- AWS has documented incident response plan to
cover
- addresses purpose
- scope
- roles
- responsibilities
- management commitment
- As per ISO 27001 and NIST 800-53 standards.
- AWS approach to incident management, is as
- AWS detects an incident.
- Specialized teams address incident.
- AWS conducts a postmortem and deep root-cause analysis of incident.
- customer support team is notified of operational issues impacting customer experience.
- AWS customer support team alert customers to any issues having broad impact, with help from Service Health Dashboard
- independent external auditors review the AWS incident management program on continual basis
AWS Security Domains
- Security incidents may occur in AWS
- Various domains in customer’s responsibility,
security incidents might occur
- service
- infrastructure
- application
- Difference is related to tools to use during the response
Service Domain
- Incidents affect user’s
- AWS account
- IAM permissions
- resource metadata
- billing
- Such event response is exclusively with
- AWS API mechanisms
- have root causes associated with configuration or resource permissions
- may relate to service-oriented logging.
Infrastructure Domain
- Incidents include data or network-related activity, as
- traffic to Amazon EC2 instances within VPC
- processes and data on EC2 instances
- Response involves
- retrieval, restoration, or acquisition of incident-related data for forensics.
- interaction with operating system of an instance
- also involve AWS API mechanisms
- Usage of AWS APIs digital forensics/incident response (DFIR) software are needed
- Incidents may involve analyzing
- network packet captures
- disk blocks on an EBS volume,
- volatile memory acquired from an instance.
Application Domain
- Incidents occur in application code or software deployed to AWS
- With appropriate application architecture, can manage this domain
- Usage of following is involved
- automated forensics
- recovery
- deployment
Detecting Cloud Security Events
- Logs and Monitors – Involves review of AWS logs
from
- CloudTrail
- S3 access logs
- VPC Flow Logs
- security monitoring services GuardDuty and Macie.
- Route 53 health checks
- CloudWatch Alarms
- OS logs as Windows Events or Linux syslog logs
- application-specific logs, as generated
- Billing Activity –sudden change in billing activity
- Threat Intelligence –third-party threat intelligence feed may correlate information with logging and monitoring tools
- Partner Tools Usage –AWS Partner Network (APN) offer many security related products
- AWS Outreach – AWS Support may contact if abusive or malicious activity is identified
- One-Time Contact – Unusual activity noticed by customers, developers, or other staff by a public-facing security contact mechanism.
Automation for abuse events handling
- AWS has
- Automated processes for abuse alerts
- set up remediation steps
- control access to sensitive abuse cases.
- Use following for automating abuse event
handling
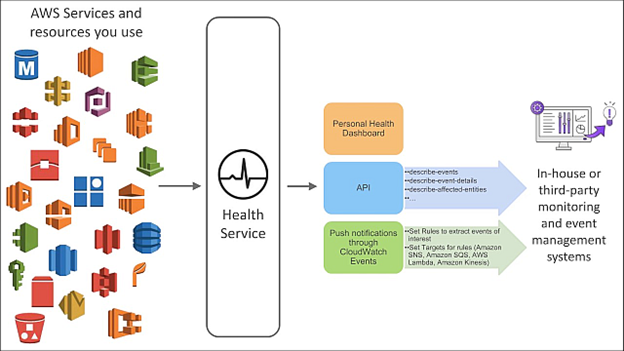
- AWS Personal Health Dashboard (PHD)
- Health APIs
- Health Amazon CloudWatch Events channel.
- Abuse types handled by AWS Health
- Sending email spam
- Spamming online forums or other websites
- Hosting a site advertised in spam
- Excessive web crawling
- Intrusion attempts (e.g., SSH or FTP)
- Exploit attacks (e.g., SQL injections)
- Hosting unlicensed copyright-protected material
- Phishing website
- Website hosting viruses/malware
- Credit card fraud
- Open proxy
- Port scanning
- IRC botnet activity
- Custom automation programs can be developed on basis of abuse events.
- Like for DoS event, route to correct team, person, or system.
- Can also use SNS notifier for events
- Also manage access to sensitive abuse alerts
like related to security.
- With fine-grained access control, limit access to sensitive alerts to specific users
- Health API programmatic access to the AWS Health
information, as
- DescribeEvents: Summary information about events.
- DescribeEventDetails: Detailed information about one or more events.
- DescribeAffectedEntities: It gives details on AWS resources which are affected by events.
- DescribeEventTypes: Details on types of events which are tracked by AWS Health.
- DescribeEventAggregates: A count of the number of events that meet specified criteria.
- DescribeEntityAggregates: A count of the number of affected entities that meet specified criteria.
AWS Certified Security - Specialty Free Practice TestTake a Quiz
