Concept of VPC Peering
Concept of VPC Peering
We will now be giving an overview of the concept of VPC Peering and VPC End Points.
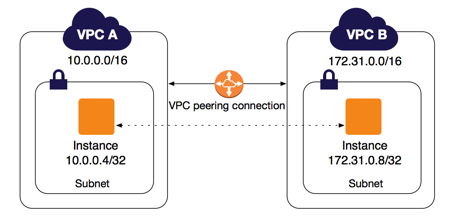
- Refers to connection between two VPCs
- Applicable within same region
- request/accept protocol for setup
- 1 to 1 relationship
- no overlapping CIDR
- cannot be different regions
- no transitive routing
- Connection between two VPCs that enables you to route traffic between them using private IP addresses via a direct network route
- Instances present in VPCs can communicate with each other akin to being in same network
- VPC peering connections can made
- between own VPCs
- with a VPC in another account but in a single region
- AWS infrastructure is used to create a VPC peering connection and separate gateway/VPN/ hardware is needed
- It enables in preventing SPOF or single point of failure
- It also addresses bandwidth bottleneck amongst VPCs
- There is no transitive peering between VPC peers (Can’t go through 1 VPC to get to another)
- Hub and spoke configuration model (1 to 1)
- Be mindful of IPs in each VPC, if multiple VPCs have the same IP blocks, they will not be able to communicate
- VPC belonging to different AWS accounts can also be peered with
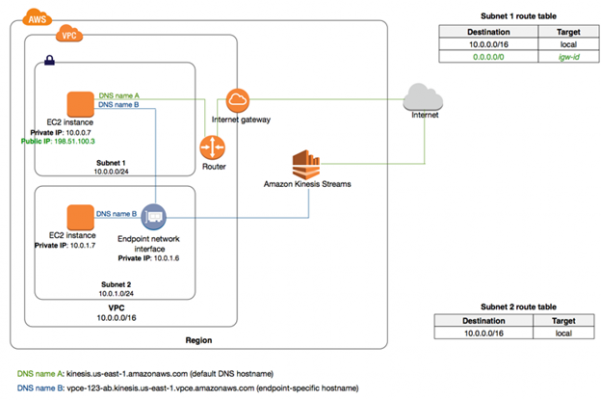
VPC End Points
- enables you to create a private connection between your VPC and another AWS service without going over the internet or through a NAT, VPN, or Direct Connect
- Provides an interface to EC2 instances for AWS resources without accessing public internet
- When you use an endpoint, the source IP address from your instances in your affected subnets for access the AWS service in the same region will use private IP address’s instead of public IP address’s
- When configuring VPC endpoints, existing connections from your affected subnets to the AWS service that use public IP address’s may be dropped
- Creation
- Specify VPC
- Specify service (com.amazonaws.<region>.<service>)
- Specify policy – full or custom
- Specify route tables
- service-destination
- endpoint-target
- It privately connect your VPC to services hosted on AWS without requiring an Internet gateway, a NAT device, VPN, or firewall proxies.
- They can scale horizontally
- highly available virtual devices
- Allow communication between instances in VPC and AWS services.
- Two Types
- Gateway type endpoints:
- available only for AWS services including S3 and DynamoDB.
- It will add an entry to your route table you selected
- route the traffic to the supported services through Amazon’s private network
- Interface type endpoints:
- provide private connectivity to services powered by PrivateLink,
- being AWS services, your own services or SaaS solutions
- supports connectivity over Direct Connect.
- Gateway type endpoints:
An interface endpoint for Kinesis Data Streams and an endpoint network interface in subnet 2.
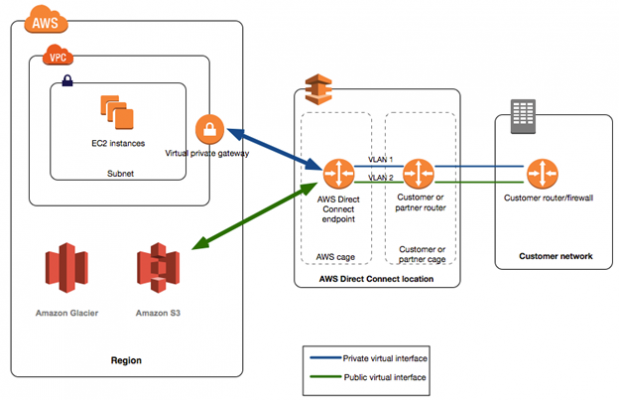
Direct Connect (DX)
- Provides a network connection from customer premises to AWS infrastructure
- A private connection amongst AWS DX locations and user’s data center/office/collocation
- High bandwidth private and dedicated connection is needed like MPLS or other circuit based communication link.
- Connect directly to AWS data centers / AWS DX locations
- Benefits include
- Lower network costs
- More bandwidth throughput
- Seamless network experience compared to internet connections
- Utilizes 802.1Q VLANs
- multiple virtual interfaces can be made by dividing the connection
- Can access both public and private, as
- public resources like S3 objects
- private resources like EC2 instances in a VPC
- still bifurcates public and private links
- configuration of Virtual interfaces can be altered any time
- VPC VPN connections utilize IPSec to establish encrypted network connectivity between your intranet and your AWS VPC over the internet
- VPN connections are configured quickly
- No internet links are used
- Direct one to one private link are used
AWS Certified Advanced Networking Specialty Free Practice TestTake a Quiz
