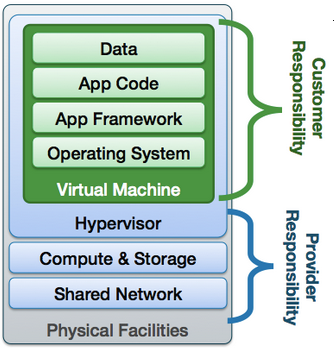
Shared Responsibility Model
In this, we will learn about Shared Responsibility Model.
Amazon safeguards the AWS infrastructure from
- Vulnerabilities
- Intrusions
- Fraud
- Abuse
So as to offer the customers with security capabilities as per their needs.
Multiple and varied AWS cloud services, emphasizes, demarcating responsibility between customer and AWS.
- AWS is responsible for the physical security of the facilities as well as the infrastructure that includes compute, database, storage and networking resources.
- The customer is responsible for software, data and access that sits on top of the infrastructure layer.
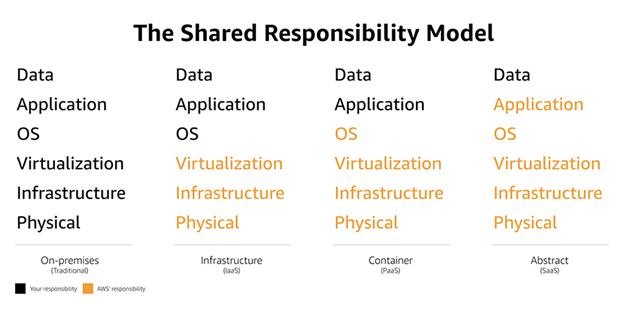
AWS Security Responsibilities
In general, AWS considers itself responsible for the security of the cloud as a whole, while customers should maintain responsibility for the security of their specific instances.
- AWS Hardware/Global Infrastructure: this includes regional, available, and edge zones of Amazon’s cloud infrastructure. This is done through physical security protections, and constant IT maintenance.
- AWS Software (Computation, Storage, Database, Networking): Amazon guarantees a secure software platform across all of its services. This aspect of Amazon’s responsibility also refers to AWS security services built by Amazon for use by customers. This can include encryption keys, network monitoring tools, database protection, and more.
Customer Security Responsibilities
Security control responsibility on the customer side is determined by the AWS Cloud service they select. When a customer chooses any of Amazon’s ‘Infrastructure as a Service’ (EC2, VPC, S3), the customer has perform all of the necessary security configuration and management tasks. This includes:
- Customer Data: protection of the businesses data on the network side, as it enters and exits the cloud service.
- Platform, Applications, Identity and Access Management: the customer is responsible for the maintenance and protection of the platform running on the cloud, and all aspects under that. For example, a customer running a clothing store online will have to ensure protection of its shoppers identities and accounts.
- Client Side Data Encryption: either through an AWS managed encryption key, or through a personal key not provided by AWS.
- File System Encryption: When protecting their data at rest, the customer can use an independent protection system, or by utilizing a file system protection provided by AWS.
- Network Traffic Protections: customers need to guarantee the security of all traffic going in and out of the server.
- Service and Communications Protection: a customer is responsible for routing and zoning data within specific security environments.
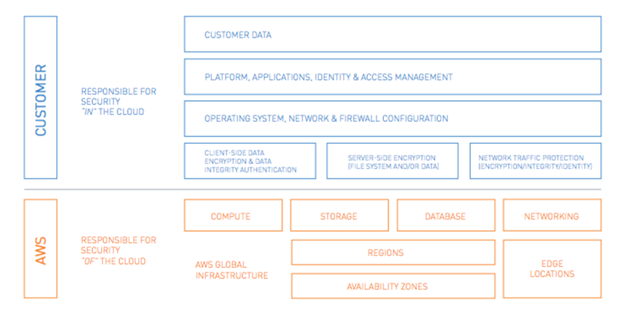
Shared Security Responsibilities
AWS using Shared Responsibility Model provides the requirements for the infrastructure and the customer must provide their own control implementation within their use of AWS services:
- IT Controls: Not only are IT operations shared between AWS and its customers, so are the management and operations of said controls. AWS can help with moderating the customer burden of security methods like firewall maintenance, network level encryption, while also overseeing IT controls deployment to ensure proper adherence to AWS security regulations.
- Patch Management: AWS is responsible for patching and fixing flaws within the infrastructure, but customers are responsible for patching their guest OS and applications.
- Configuration Management: AWS maintains the configuration of its infrastructure devices, but a customer is responsible for configuring their own guest operating systems, databases, and applications.
- Awareness & Training: AWS trains AWS employees, but a customer must train their own employees.
- Customer Specific: Controls which are solely the responsibility of the customer based on the application they are deploying within AWS services.
- Service and Communications Protection: or Zone Security which may require a customer to route or zone data within specific security environments.
Customers should
- implement access control policies using AWS IAM
- configuring AWS Security Groups (firewall) to prevent inappropriate access to ports
- enabling AWS CloudTrail
Customers are also responsible for
- enforcing appropriate data loss prevention policies for compliance with internal and external policies,
- Detecting and remediating threats arising from stolen account credentials or malicious/accidental misuse of AWS.
Amazon is focused on securing its software, hardware, and the facilities where AWS services are located. Amazon’s responsibilities include securing its
- Computing
- Storage
- Networking
- database services
- security configuration of AWS managed services like DynamoDB, RDS, Redshift, Elastic MapReduce, Workspaces, etc.
AWS Shared Responsibility Model Summary
| Customer | AWS | |
| Preventing or detecting when an AWS account has been compromised | x | |
| Preventing or detecting a privileged or regular AWS user behaving in an insecure manner | x | |
| Configuring AWS services (except AWS Managed Services) in a secure manner | x | |
| Restricting access to AWS services or custom applications to only those users who require it | x | |
| Updating Guest Operating Systems and applying security patches | x | |
| Ensuring AWS and custom applications are being used in a manner compliant with internal and external policies | x | x |
| Ensuring network security (DoS, MITM, port scanning) | x | x |
| Configuring AWS Managed Services in a secure manner | x | |
| Providing physical access control to hardware/software | x | |
| Providing environmental security assurance against things like mass power outages, earthquakes, floods, and other natural disasters | x | |
| Database patching | x | |
| Protecting against AWS zero day exploits and other vulnerabilities. | x | |
| Business continuity management (availability, incident response) | x |