Security Token Service
- STS provides temporary credentials for AWS resource access
- Users can use STS from sources, as
- Federation using Active Directory –
- Requires SAML
- temporary credentials as per user’s AD credentials
- IAM user is not needed
- With SSO, can also sign in to AWS console without any IAM credentials
- Federation of Mobile Apps with web federation
- Web federation from Facebook/Amazon/Google/other OpenID providers
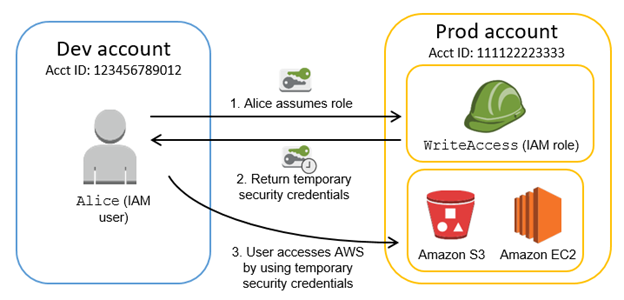
- Cross Account Access:
- Users from one AWS account access to access resources in other one
- Federation using Active Directory –
- Important terms
- Federation –join users in one domain with another like AD -> IAM
- Identity Broker – service to join or federate, identity from Domain A to Domain B
- Identity Store – Services storing identities like AD, Facebook, Google, Amazon, etc.
- Identities – user of service
- Steps of Authentication
- User enters username/password
- Application calls an Identity Broker with username/password
- Identity Broker validate user identity with organizational centralized authentication like AD
- After validation, Identity Broker calls GetFederationToken function with IAM credentials covering IAM policy, permission and duration
- STS if called by user, returns following values
- Access Key
- Secret Access Key
- Token
- Duration of token
- Identity Broker sends temporary credentials to application
- Application sends requests to AWS using temporary credentials
- AWS verifies credentials by IAM and provide requested operation or service
Web Identity Federation
- Access AWS resources
- Most useful for mobile apps
- Process involves
- application getting authentication token
- using token for temporary credentials.
- Recommended for temporary and should not be embedded or distributed with apps
- Supports following providers
- Amazon
- Any other OpenID Connect (OIDC) compatible id provider
AWS Certified Developer - Associate Free Practice TestTake a Quiz
