Security Groups and NACLs
- It acts as a virtual firewall for instance to control inbound and outbound traffic.
- After launching instance in VPC, can assign up to 5 security groups to instance.
- Security groups act at instance level, not subnet level.
- each instance in a subnet in VPC could be assigned to a different set of security groups.
- If security group not specified at launch time, the instance is automatically assigned to the default security group for the VPC.
- Can add rules to control inbound traffic to instances,
- separate set of rules to control the outbound traffic.
- have limits on
- number of security groups, can be created per VPC,
- number of rules, can be added to each security group
- number of security groups, can be associated with a network interface.
- allow rules only can be specified
- deny rules cannot be specified
- inbound and outbound traffic can have their own separate rules.
- no inbound rules during security group creation
- By default, a security group has outbound rule to allows all outbound traffic.
- Security groups are stateful
- if request is sent from instance, the response traffic for that request is allowed to flow in regardless of inbound security group rules.
- Irrespective of outbound rules, response to permitted inbound traffic, will be sent
- Instances with a security group can’t talk to each other unless rules allow
- All security group has a set of rules added to them, by default
- security group name and description should comply
as
- Names and descriptions can be up to 255 characters in length.
- Names and descriptions are limited to the following characters: a-z, A-Z, 0-9, spaces, and ._-:/()#,@[]+=&;{}!$*.
- A security group name cannot start with sg-.
- The name of security group name should be unique in the VPC.
Default rules for a default security group
| Destination | Protocol | Port Range | Comments |
| Inbound – The security group ID (sg-xxxxxxxx) | All | All | Allow inbound traffic from instances assigned to the same security group. |
| Outbound – 0.0.0.0/0 | All | All | Allow all outbound IPv4 traffic. |
| Outbound – ::/0 | All | All | Allow all outbound IPv6 traffic. This rule is added by default if you create a VPC with an IPv6 CIDR block or if you associate an IPv6 CIDR block with existing VPC. |
Security Group Rules
- User can easily add or eliminate rules for a specific security group
- Security group rule can be applied either to ingress/inbound traffic to the security group or egress/ outbound traffic to the security group.
- Flexibility to grant access to
- specific CIDR range
- another security group in VPC
- in a peer VPC
- Following are applicable to security
- Contents of security group rule in an AWS VPC
- Name of any protocol as specified by IANA, and as per standard protocol number. Like for ICMP as protocol, can also enlist any or all of ICMP types and codes.
- An
description for security group rule.
- It is optional
- Description helps in identification, later.
- Maximum 255 characters in length.
- Allowed
characters are
- a-z
- A-Z
- 0-9
- Spaces
- ._-:/()#,@[]+=;{}!$*.
-
- For
rules which act on Inbound
- Specify source of traffic and destination port or port range
- source
can be
- another security group
- an IPv4 or IPv6 CIDR block
- single IPv4 or IPv6 address.
- For
rules which act on Inbound
- Specify destination for traffic and destination port or port range
- destination
can be
- another security group
- an IPv4 or IPv6 CIDR block
- single IPv4 or IPv6 address
- prefix list ID (ID of service for a Region).
- For
rules which act on Inbound
NACLs
- Default NACLs allow all Inbound / Outbound traffic.
- Custom NACLs by default deny all Inbound / Outbound traffic.
- stateless firewall
- creation of an ACL has a default deny inbound and outbound
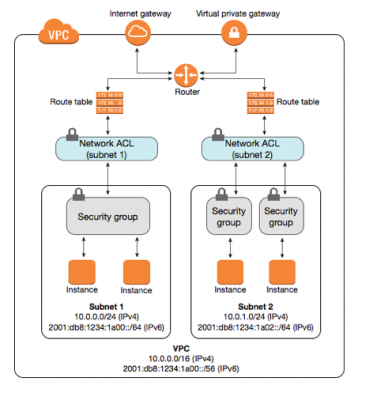
- All of the subnets present in a VPC, should have a NACL
- Numbered list of rules that are evaluated in order starting at the lowest numbered rule first to determine what traffic is allowed in or out depending on what subnet is associated with the rule
- The highest rule number is 32766
- Usually the rule number to start is, 100 and then more rules are added accordingly
- Different rules to deny or allow traffic can be applied on either incoming or outgoing traffic
- The default NACL present in VPC allows all traffic both in or out
- Any custom NACL when added, has default setting of denying all the traffic, till specific rules are added
- You must assign a NACL to each subnet, if a subnet is not associated with a NACL, it will allow no traffic in or out
- NACL rules do not maintain any state
- A single NACL can be assigned only to a single subnet
- After association of a NACl with a subnet, all of the past NACLs are deleted
- A single NACL can be assigned to many subnets whereas one subnet can have only one NACL
- Each subnet in VPC must be associated with a NACL. If you don’t explicitly associate a subnet with an ACL, the subnet automatically gets associated with the default ACL
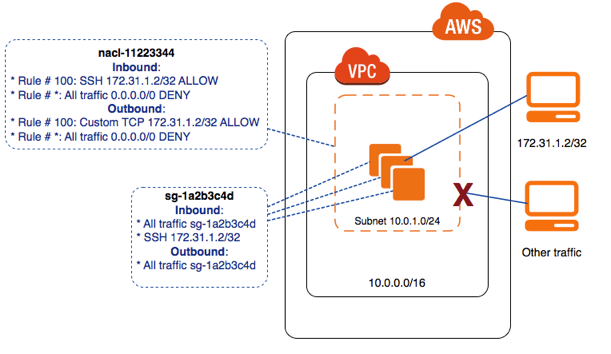
- You can block IP addresses using NACLs not Security Groups
- NACLs contain numbered rules evaluated in the order staring from the lowest one.
- NACLs are stateless. Response to allow inbound traffic is subject to outbound rules.
- Ideally, only ephemeral ports should be allowed in outbound traffic
AWS Certified Advanced Networking Specialty Free Practice TestTake a Quiz
