- Sign in with MFA involves prompt for
- user name and password (also called as 1st factor or what the user knows)
- authentication response from MFA device (also called as 2nd factor or what user has)
- Multiple factors add more security for AWS account and resources access.
- It is recommended to enable MFA for AWS account root user and every IAM user
- MFA can control AWS service APIs access.
Types of MFA mechanism supported b AWS are
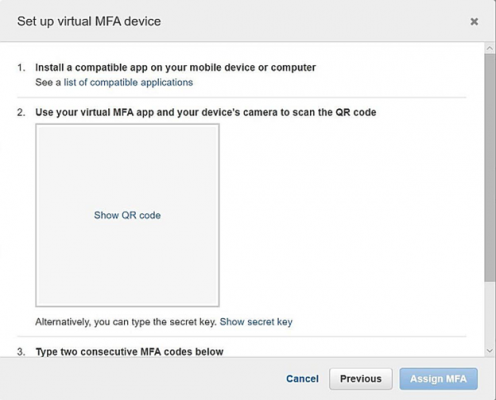
- Virtual MFA devices – Is a mobile app for mobile devices emulating a physical MFA device. App generates a six-digit numeric code as per time-synchronized one-time password algorithm. The code is to be given on second webpage during sign-in. Every virtual MFA device allocated to user should be unique so that another user’s virtual MFA is not used.
- U2F security key – Hardware USB device and whose authentication standard hosted by the FIDO Alliance. After sign in code from device is generated by tapping and to be entered for sign in.
- Hardware MFA device. Similar to virtual MFA but it is hardware device instead of mobile app.
- SMS based MFA. SMS is sent to IAM user phone number, with a six-digit numeric code for sign in. It is only for IAM users and not root user.
AWS Certified Developer - Associate Free Practice TestTake a Quiz
