IAM Policies with Principal
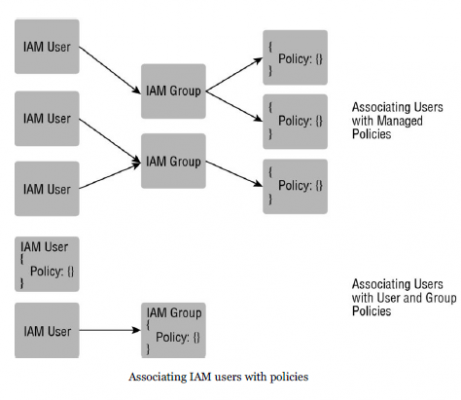
- Many ways to associate a policy with IAM
- policy can be associated directly with an IAM user, as
- User Policy
- It with reference to user to which they are associated.
- In console, a user policy is entered into user interface on the IAM user page.
- Managed Policy
- User Policy
- created in Policies tab on the IAM page (or through the CLI) and exist independently of any individual user.
- same policy can be associated with many users or groups of users.
- large number of predefined managed policies on Policies tab of IAM page in the AWS Management Console.
- can write own policies specific to your use cases.
- method to associate policies with users with the IAM Groups feature.
- Groups simplify managing permissions for large numbers of users.
- Once a policy is assigned to a group, any user who is a member of that group assumes those permissions.
- assignment of policies to an entire team in organization becomes much simpler.
Associate policy with an IAM Group
- Group Policy
- exist in context of group to which they are attached.
- In the AWS Management Console, a group policy is entered into the user interface on the IAM Group page.
- Managed Policies
- Managed policies can be associated with IAM users
- can also be associated with IAM groups.
- Associate a policy with actor, for
- Authenticated IAM user (can be a person or process) – IAM user must have rights to assume role.
- Trusted Service outside of AWS – Like on premises LDAP directory or a web authentication service. AWS Cloud service will assume role on actor’s behalf and return a token to actor.
- Once an actor has assumed a role, it then provided with a temporary security token associated with the policies of that role.
- token contains all information required to authenticate API calls.
- This information includes
- a standard access key
- additional session token required for authenticating calls under an assumed role.
Are you a Solution Architect Associate?Take a Quiz
