- It is a cloud-based hardware security module (HSM)
- enables you to easily generate and use your own encryption keys on the AWS
- You can manage your own encryption keys
- using FIPS 140-2 Level 3 validated HSMs.
- Integrate with your applications using industry-standard APIs, such as PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries.
- Offload SSL/TLS processing for web servers,
- protect private keys linked to an issuing certificate authority (CA),
- enable Transparent Data Encryption (TDE) for Oracle databases.
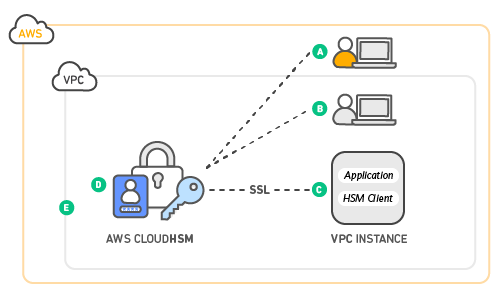
- A: AWS manages the hardware security module (HSM) appliance, but does not have access to your keys
- B: You control and manage your own keys
- C: Application performance improves (due to close proximity with AWS workloads)
- D: Secure key storage in tamper-resistent hardware available in multiple Availability Zones (AZs)
- E: Your HSMs are in your Virtual Private Cloud (VPC) and isolated from other AWS networks.
When to use AWS CloudHSM
Use AWS CloudHSM when you need to manage the HSMs that generate and store your encryption keys. In AWS CloudHSM, you create and manage HSMs, including creating users and setting their permissions. You also create the symmetric keys and asymmetric key pairs that the HSM stores.
