Cloud Key Management Service Google Professional Data Engineer GCP
- stores cryptographic keys in a hierarchical structure
- designed for access control management.
- Access to resources in this structure is governed by Cloud IAM
- The hierarchy levels, are:
- Project
- Location
- Key ring
- Key
- Key version
- Project
- resources belong to a project as in other GCP services.
- run Cloud KMS in a separate project from any other GCP resources.
- Location
- geographical data center location where Cloud KMS resources/keys created, stored and requests are handled
- A special location – global, its resources are available from multiple data centers.
 Key ring
Key ring
- a grouping of keys for organizational purposes.
- A key ring belongs to a Project and resides in a specific location.
- Keys inherit permissions from the key ring.
- Grouping enables to grant, revoke, or modify permissions to those keys at the key ring level.
- Key ring resource ID
- resource ID of key ring needed by API calls
- It is the fully-qualified KeyRing name.
- value is case-sensitive
- Key
- a named object representing a cryptographic key.
- The key material, (actual bits ) can change over time in new key versions
- Used to encrypt single or a collection of files
- Only people with decrypt permissions can decrypt them.
- Key version
- represents the key material associated with a key at some point in time.
- key can have many versions
- must have at least one version
- Versions are numbered sequentially, starting with 1.
- Cloud KMS automatically identifies version used for encryption so only key name is sent for decryption
- The key material with a key version has a type, listing key length and algorithm
- all keys are AES-256 keys used in Galois Counter Mode (GCM)
- Cloud KMS uses probabilistic encryption
- Key modes are not currently exposed through our API
- Key versions have states – enabled, disabled, scheduled for destruction or destroyed.
- Any version can be used till disabled, destroyed, or scheduled for destruction state.
- the raw cryptographic key material of a key version can never be viewed or exported.
- A symmetric key at any point in time will have a primary key version.
- With new key version and making that version the primary version, can rotate a symmetric key
- Asymmetric keys also have different rotation considerations
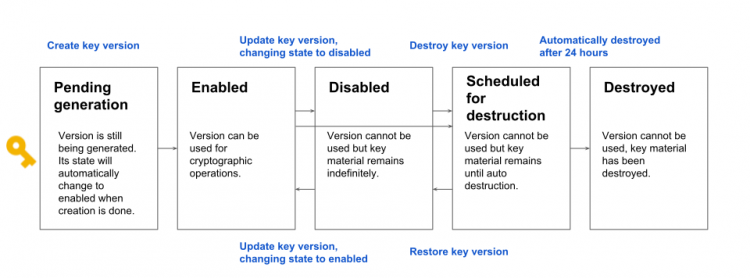
Lifetime of objects
- key ring and key resources CANNOT be deleted, to prevent resource name collisions.
- Key versions also cannot be deleted,
- key version material can be destroyed
- Key rings and keys do not have billable costs or quota limitations
Google Professional Data Engineer (GCP) Free Practice TestTake a Quiz
