Certified Information Security Manager (CISM)

Certified Information Security Manager (CISM) Certification Exam demonstrates in-depth knowledge and understanding of the relationship between information security programs and broader business goals and objectives. The CISM certification promotes international security practices. Moreover, CISM-certified employees provide enterprises with an information security management certification recognized by organizations and clients around the globe.
Who should take the exam?
The exam is designed for candidates who are able to manage, design, oversee, and assess an enterprise’s information security function. The CISM exam requirements are:
- Five (5) or more years of experience in information security management.
- Experience waivers are available for a maximum of two (2) years.
Solid Reasons to take the certification
Are you wondering Is CISM certification worth it? Then read on to find out!
- The CISM certification demonstrates your understanding of the relationship between an information security program and broader business goals and objectives.
- It distinguishes you as having not only information security expertise. But also knowledge in the development of an information security program.
- This particular certification holds the potential to put you in an elite peer network.
- It is considered essential to ongoing education, career progression, and value delivery to enterprises.
ISACA (CISM): Certified Information Security Manager
CISM Exam Format
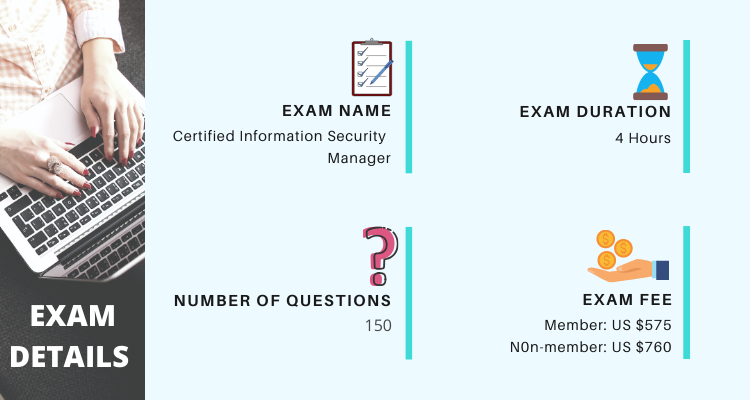
The Certified Information Security Manager (CISM) exam consists of 150 multiple-choice questions. Candidates have to score at least 450 or more points to pass the exam. Moreover, the CISM exam duration is 4 hours. The CISM exam costs $575 USD for members and $760 for non-members which includes additional taxes. Also, the CISM exam questions are available in 4 languages, namely Chinese Simplified, English, Japanese, and Spanish.
How to schedule the exam?
ISACA’s Certified Information Security Manager (CISM) certification indicates expertise in information security governance, program development and management, incident management and risk management. Candidates must select either online remote proctoring or an in-person testing center.
Candidates can schedule their exam at www.isaca.org/MYISACA.
Check out the Certified Information Security Manager Interview Questions to prepare for the interview.
Course Outline
First Domain: Information Security Governance (17%)
A–ENTERPRISE GOVERNANCE
- Organizational Culture
- Legal, Regulatory and Contractual Requirements
- Organizational Structures, Roles and Responsibilities
B–INFORMATION SECURITY STRATEGY
- Information Security Strategy Development
- Information Governance Frameworks and Standards
- Strategic Planning (e.g., Budgets, Resources, Business Case)
Second Domain: Information Security Risk Management (20%)
A–INFORMATION SECURITY RISK ASSESSMENT
- Emerging Risk and Threat Landscape
- Vulnerability and Control Deficiency Analysis
- Risk Assessment and Analysis
B–INFORMATION SECURITY RISK RESPONSE
- Risk Treatment / Risk Response Options
- Risk and Control Ownership
- Risk Monitoring and Reporting
Third Domain: Information Security Program (33%)
A–INFORMATION SECURITY PROGRAM DEVELOPMENT
- Information Security Program Resources (e.g., People, Tools, Technologies)
- Information Asset Identification and Classification
- Industry Standards and Frameworks for Information Security
- Information Security Policies, Procedures and Guidelines
- Information Security Program Metrics
B–INFORMATION SECURITY PROGRAM MANAGEMENT
- Information Security Control Design and Selection
- Information Security Control Implementation and Integrations
- Information Security Control Testing and Evaluation
- Information Security Awareness and Training
- Management of External Services (e.g., Providers, Suppliers, Third Parties, Fourth Parties)
- Information Security Program Communications and Reporting
Fourth Domain: Incident Management (30%)
A–INCIDENT MANAGEMENT READINESS
- Incident Response Plan
- Business Impact Analysis (BIA)
- Business Continuity Plan (BCP)
- Disaster Recovery Plan (DRP)
- Incident Classification/Categorization
- Incident Management Training, Testing and Evaluation
B–INCIDENT MANAGEMENT OPERATIONS
- Incident Management Tools and Techniques
- Incident Investigation and Evaluation
- Incident Containment Methods
- Incident Response Communications (e.g., Reporting, Notification, Escalation)
- Incident Eradication and Recovery
- Post-Incident Review Practices
Exam Policies
CISM is one of the most sought after information security certification, ensuring that the potential aspirants for the exam are well aware of the exam policies. These exam policies provide various required and relevant exam details, along with the certification exam procedures.

For More Queries Visit : Certified Information Security Manager (CISM) FAQs
CISM Exam Preparation Guide
We will provide the learning resources to get the most from your efforts in the exam preparation using the CISM certification guide

Step 1: Create a Study Plan
Before you begin your preparation process, it becomes highly important to create a study plan. Make your study plan in accordance to your exam objectives and be realistic about your work and obligations. For example, how much can you spend on preparation material, is there a need to take a training course, and what CISM exam training method best suits you. Creating a study plan can help you save your study time and boost your preparation process.
Learning Resource 2: Read ISACA Guide
Every year, ISACA issues an updated version of its candidate guide with a view to providing practical information for the CISM exam. This particular CISM exam guide aims to make candidates familiar with what to expect on the day of the exam. The ISACA guide contains valuable information like the exam domains, number of exam questions, exam length, and CISM exam pattern. Remember, no candidate should take the CISM exam without reading this guide that offers the CISM exam overview.
Learning Resource 3: Join Online Forums
ISACA sponsors online forums for its candidates which is quite easy to obtain. Online forums allow the sharing of questions study methods and tips for the exam. They are an amazing place for learning what to expect the day of the exam. Besides this, it costs nothing and allows candidates to ask and answer questions. Besides this, it allows direct contact with other like-minded professionals to solve a problem.
Learning Resource 4: Practice Tests
Practice tests are one of the efficient ways to prepare for the exam. However, there exists no substitute for practice questions when preparing for the CISM exam. CISM exam sample questions in practice tests are not actual exam questions. However, the type, structure, and level of difficulty fully represent what is expected of candidates during the real test. They help candidates to focus study efforts accordingly.
Practice tests allow aspirants to measure themselves anywhere with an internet connection.



