- Expands to Identity and Access Management
- Gives you centralised control of an AWS account
- Is global – there is no concept of regional IAM at this time; all users, groups, policies, etc are available in all regions.
- Supports Identity Federation which can be used for Single Sign-on i.e. via SAML
- Can be used to give temporary access
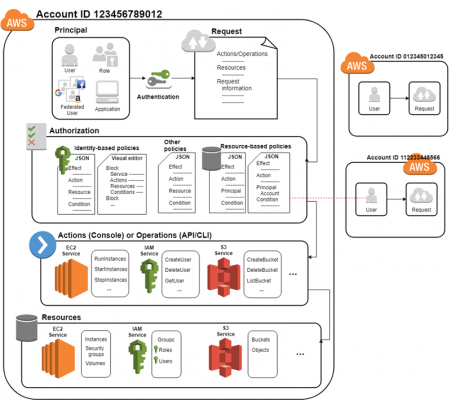
- IAM terms
- Resources – The user, group, role, policy, and identity provider objects that are stored in IAM. You can add, edit, and remove resources from IAM.
- Identities – The IAM resource objects that are used to identify and group. Attach a policy to an IAM identity. These include users, groups, and roles.
- Entities – The IAM resource objects that AWS uses for authentication and include users and roles. Roles can be assumed by IAM users and roles in your or another account. They can also be assumed by users federated through a web identity or SAML.
- Principals – A person or application that uses the AWS account root user, an IAM user, or an IAM role to sign in and make requests to AWS.
- Terms used
- User — an end user (like…a person)
- Groups — a collection of users under one set of permissions
- Policies — a document that defines permissions (which you assign to users, groups, and roles)
- Roles — this has nothing to do with the users in your account. Roles are for granting permissions to resources, like an EC2 instance (it can do other cool stuff too)
Default limits for IAM entities:
| Resource | Default Limit |
| Customer managed policies in an AWS account | 1500 |
| Groups in an AWS account | 300 |
| Roles in an AWS account | 1000 |
| Managed policies attached to an IAM role | 10 |
| Managed policies attached to an IAM user | 10 |
| Virtual MFA devices (assigned or unassigned) in an AWS account | Equal to the user quota for the account |
| Instance profiles in an AWS account | 1000 |
| Server certificates stored in an AWS account | 20 |
Limits for IAM entities:
| Resource | Limit |
| Access keys assigned to an IAM user | 2 |
| Access keys assigned to the AWS account root user | 2 |
| Aliases for an AWS account | 1 |
| Groups an IAM user can be a member of | 10 |
| IAM users in a group | Equal to the user quota for the account |
| Users in an AWS account | 5000 (If you need to add a large number of users, consider using temporary security credentials.) |
| Identity providers (IdPs) associated with an IAM SAML provider object | 10 |
| Keys per SAML provider | 10 |
| Login profiles for an IAM user | 1 |
| Managed policies attached to an IAM group | 10 |
| Permissions boundaries for an IAM user | 1 |
| Permissions boundaries for an IAM role | 1 |
| MFA devices in use by an IAM user | 1 |
| MFA devices in use by the AWS account root user | 1 |
| Roles in an instance profile | 1 |
| SAML providers in an AWS account | 100 |
| Signing certificates assigned to an IAM user | 2 |
| SSH public keys assigned to an IAM user | 5 |
| Tags that can be attached to an IAM role | 50 |
| Tags that can be attached to an IAM user | 50 |
| Versions of a managed policy that can be stored | 5 |
The following are the maximum lengths for entities:
| Description | Limit |
| Path | 512 characters |
| User name | 64 characters |
| Group name | 128 characters |
| Role name | 64 characters |
| Tag key | 128 characters |
| Tag value | 256 characters. Tag values can be empty. |
| Instance profile name | 128 characters |
| Unique IDs created by IAM | 128 characters |
| Policy name | 128 characters |
| Password for a login profile | 1 to 128 characters |
| Alias for an AWS account ID | 3 to 63 characters |
| Role trust policy JSON text (the policy that determines who is allowed to assume the role) | 2,048 characters |
| Role session name | 64 characters |
| Role session duration | 12 hours When you assume a role from the AWS CLI or API, you can use the duration-secondsCLI parameter or the DurationSecondsAPI parameter to request a longer role session. You can specify a value from 900 seconds (15 minutes) up to the maximum session duration setting for the role, which can range from 1 hour to 12 hours. |
| For inline policies | The total aggregate policy size (the sum size of all inline policies) per entity cannot exceed the following limits: User policy size cannot exceed 2,048 characters Role policy size cannot exceed 10,240 characters Group policy size cannot exceed 5,120 characters |
| For manage policies | You can add up to 10 managed policies to an IAM user, role, or group. The size of each managed policy cannot exceed 6,144 characters. |
| For session policies | You can pass only one JSON policy as a parameter when you programmatically create a temporary session for a role or federated user. The size of each managed policy cannot exceed 2,048 characters. |
Are you an AWS SysOps Administrator Associate?Take a Quiz
