AWS Identity and Access Management (IAM) Principals
Here, we will learn about AWS Identity and Access Management (IAM) Principals.
- Service that allows to control how people and programs are allowed to manipulate the AWS infrastructure.
- Usually IAM uses identity like users, groups, and access control policies to control the use of AWS resources
- AWS IAM control is granular to limit a single user to perform a single action on a specific resource from a specific IP address during a specific time window.
- Applications can also be granted access to AWS resources
- AWS IAM is not an identity store/authorization system for applications.
- permissions assigned to manipulate AWS infrastructure, and not within given application.
- AWS IAM is not an operating system identity management.
Principals
- a principal is an IAM entity allowed to interact with AWS resources, and can be permanent or temporary, and represent a human or an application.
- three types of principals
- Root users
- IAM users
- Roles/temporary security tokens.
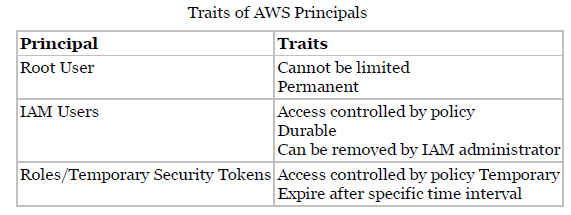
- Root User
- Present during AWS account creation
- Hence, single sign-in principal with the complete access to all AWS Cloud services and resources
- User present till open account with AWS
- root user can be used for both console and programmatic access to AWS resources.
- IAM Users
- persistent identities set up by IAM service to represent individual or applications.
- there is no expiration period
- are permanent entities that exist until an IAM administrator takes an action to delete them.
- may create separate IAM users for each member of operations team to interact with console and use the CLI.
- Simiarly, create dev, test, and production users for applications that need to access AWS Cloud services.
- can create using principals with IAM administrative privileges at any time
- Created through
- AWS Management Console
- CLI
- SDKs
- Roles/Temporary Security Tokens
- Used for advanced IAM usage
- used to grant specific privileges to specific actors for a set duration of time
- AWS offers the actor with a temporary security token from the AWS Security Token Service (STS)
- requesting a temporary security token needs duration of token before it expires.
- range of a temporary security token lifetime is 15 minutes to 36 hours.
- Use cases enabled by Roles and Temporary Security Tokens
- Amazon EC2 Roles — Involves granting permissions to applications running on an Amazon EC2 instance.
- Cross-Account Access — Involves granting permissions to users from other AWS accounts, whether you control those accounts or not.
- Federation — Involves granting permissions to users authenticated by a trusted external system.
Are you a Solution Architect Associate?Take a Quiz
