Access management Google Professional Data Engineer GCP
Access management as
- attempts to access a resource by authenticated member is checked by Cloud IAM against IAM policy
Resource
- To whom access is granted
- grant the user a role for a resource.
- Resource examples
- Projects
- Compute Engine instances
- Cloud Storage buckets
- Fine granular access by some services
- Storage Admin role (roles/storage.admin) can be at bucket level
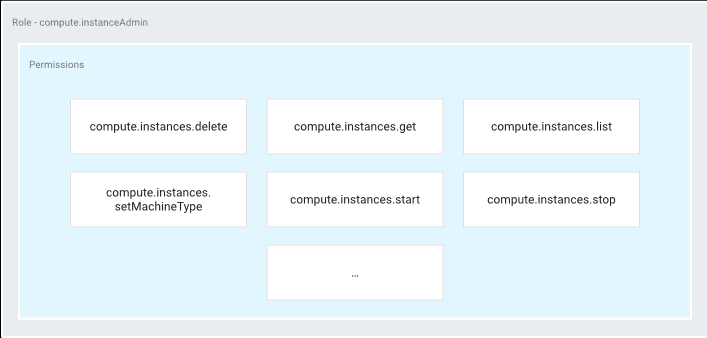
- Instance Admin role (roles/compute.instanceAdmin) at instance level.
- Mostly IAM permissions at project level.
- permissions are inherited by all resources within that project.
Permissions
- determine what operations are allowed on a resource.
- represented in the form of <service>.<resource>.<verb>, like pubsub.subscriptions.consume.
- mostly correspond one-to-one with REST API methods.
- users directly are not granted permissions.
- Users are given roles with specific permissions
Roles
- is a collection of permissions
- cannot grant a permission to the user directly.
- grant users a role and grant permissions to role
 3 roles types in Cloud IAM:
3 roles types in Cloud IAM:
- Primitive roles:
- historically available in the Google Cloud Console.
- roles are Owner, Editor, and Viewer.
- Avoid using them as have a wide range of permissions across GCP services.
- Predefined roles
- For finer-grained access control
- Custom roles:
- create to tailor permissions as per needs.
Google Professional Data Engineer (GCP) Free Practice TestTake a Quiz
